Sometimes you need to send a file containing sensitive information across to someone over internet and you started thinking, “Gee, I’ve got some pretty sensitive information in the file. How can I send it securely?” There are many ways to send encrypted files. A good way for encrypting files is using …
Read More »Three effective solutions for Google Analytics Referral spam
I opened my Analytics account yesterday cause I saw 25% traffic increase from Facebook, Twitter and many random sources and 83% increase on the root ("/") of the server. Well, 25% is nothing, it can happen due to a post going viral. But this wasn't the case this time as 83% increase was specific to the root ("/") of the server It seems, our 'beloved' 'Vitaly Popov' has started a new stream of referral spam. He's got more crafty as I predicted in my original post. He's now actually using Facebook, Twitter as referrals including some new domains.
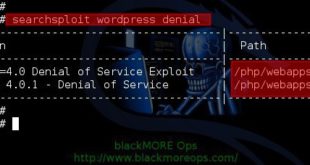
Read More »Denial of Service Attack Proof of Concept PHP Exploit for <=4.0 WordPress DoS Attack - CVE-2014-9034
Proof of Concept PHP exploit for WordPress DoS Attack CVE-2014-9034 worked like a charm on my own WordPress website. Surprisingly, CVE-2014-9034 was published for sometime and it seems WordPress still hasn’t fixed this issue. I will explain how to use this Proof of Concept tool and test your own WordPress …
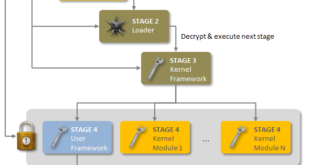
Read More »Regin Malware: Top-tier espionage tool enables stealthy surveillance
I don’t usually reblog or post others post in here. But this is something EVERYONE should be aware of. An advanced piece of malware, known as Regin Malware, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, …
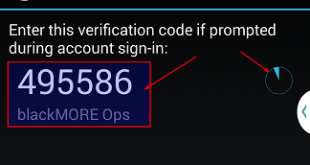
Read More »Securing SSH with two factor authentication using Google Authenticator
Two-step verification (also known as Two-factor authentication, abbreviated to TFA) is a process involving two stages to verify the identity of an entity trying to access services in a computer or in a network. This is a special case of a multi-factor authentication which might involve only one of the …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….