Organizations should configure system logs to detect incidents and to identify the type and scope of malicious activity. Properly configured logs enable rapid containment and appropriate response. Response An organization’s ability to rapidly respond to and recover from an incident begins with the development of an incident response capability. An …
Read More »Publicly Available Tools Seen in Cyber Incidents Worldwide
Remote Access Trojan: JBiFrost First observed in May 2015, the JBiFrost RAT is a variant of the Adwind RAT, with roots stretching back to the Frutas RAT from 2012. A RAT is a program that, once installed on a victim’s machine, allows remote administrative control. In a malicious context, it …
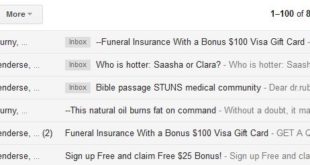
Read More »telus.com spam emails to gmail account
Just something I bumped into this morning and decided to quickly write a post. Woke up this morning and first thing I saw is a bunch of spam emails in my Gmail account. I kept getting these spam emails that are said to be sent by me but are sent …
Read More »How to create a Bot Net legally? Put that in your ToS, that’s how!
This is a #rant post, TL'DR. In summary, you can just create a Chrome, Firefox, iOS, Android extension/plugin/app for free, let it grow bigger overtime and then just sell idle users bandwidth to Bot Net for profit. And you just put that somewhere in your looong ToS that everyone just presses "I Agree, get it over with and let me use the service already".
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….