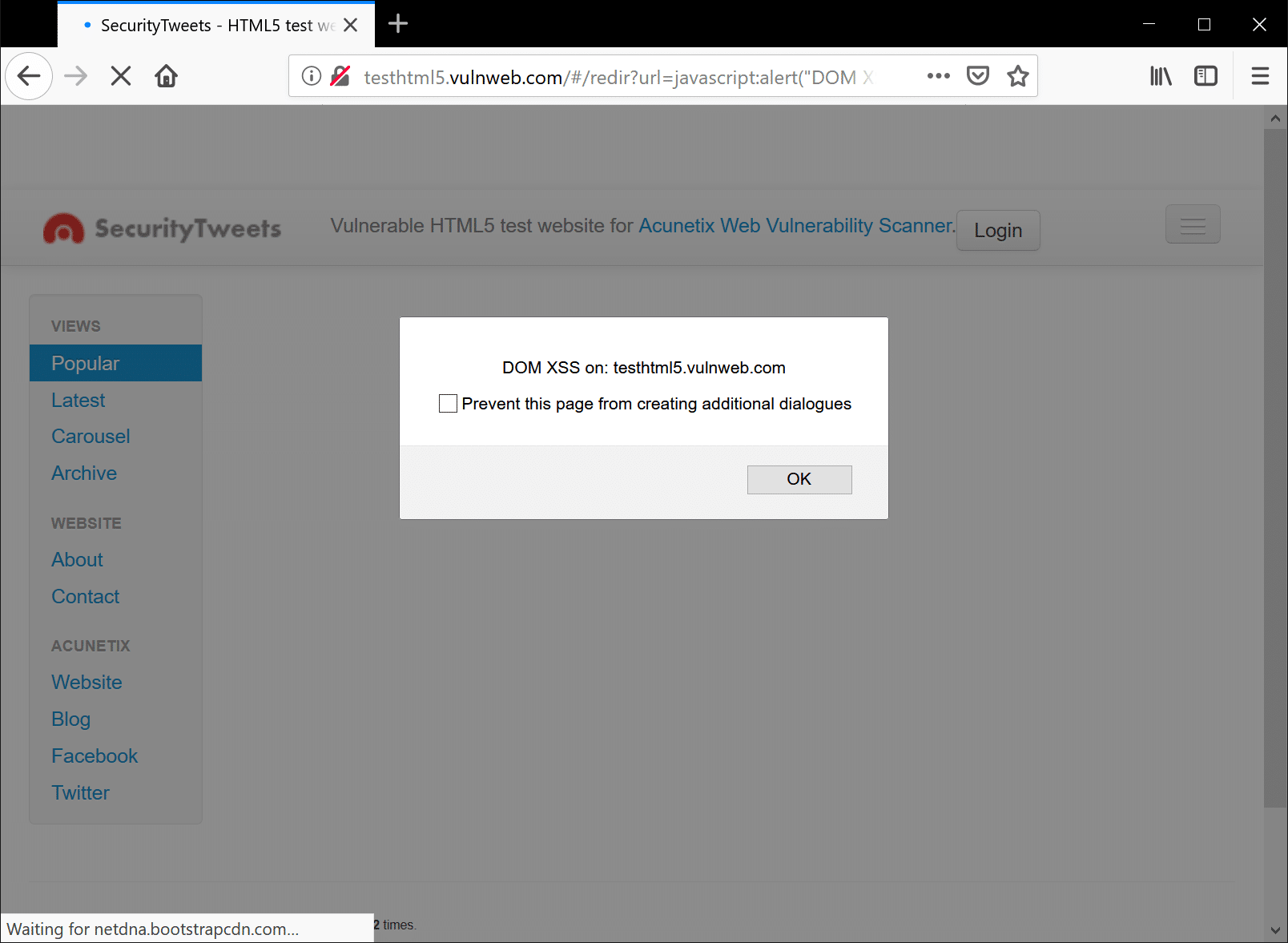
There’s no denying the role that JavaScript has played in making web applications the sleek, interactive, online experiences that we know and love today. This powerful scripting language brought interactivity and animation to the web. But with great power comes great responsibility. Cross-site-scripting (XSS) remains a persistent stalwart among the …
Read More »How to access Dark Web?
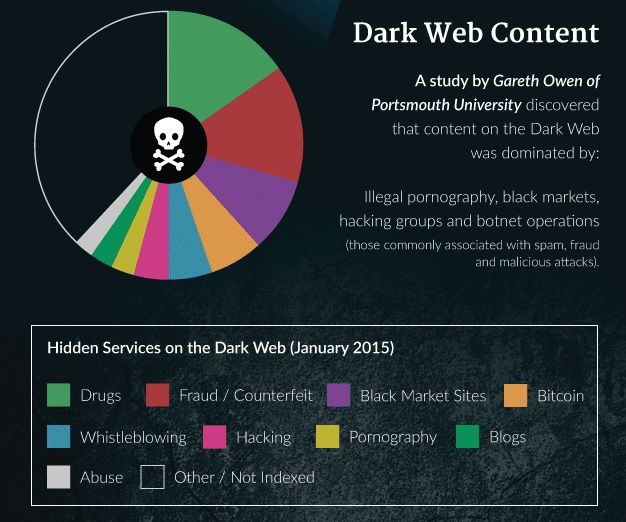
The concept of the Dark Web isn’t vastly different from the Surface Web. There are message boards (e.g. 8chan, nntpchan), places you can buy things (e.g. Alphabay, Hansa), and blogs (e.g. OnionNews, Deep Web Radio). The rules, or rather a lack thereof, is what makes the Dark Web unique. Anything …
Read More »Inception Attackers Target Europe with Year-old Office Vulnerability
The Inception attackers have been active since at least 2014 and have been documented previously by both Blue Coat and Symantec; historical attacks used custom malware for a variety of platforms, and targeting a range of industries, primarily in Russia, but also around the world. This blog describes attacks against …
Read More »Targeting websites with Password Reset Poisoning
Most of web application security vulnerabilities, leverage user input in ways that were not initially intended by their developer(s). Password Reset Poisoning is one such vulnerability, that leverages commonly unthought of headers, such as the Host header seen in an HTTP request: GET https://example.com/reset.php?email=foo@bar.com HTTP/1.1 Host: evilhost.com Notice the difference …
Read More »Emotet Malware – one of the most destructive malware right now
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate. Emotet continues to be among the most costly …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….