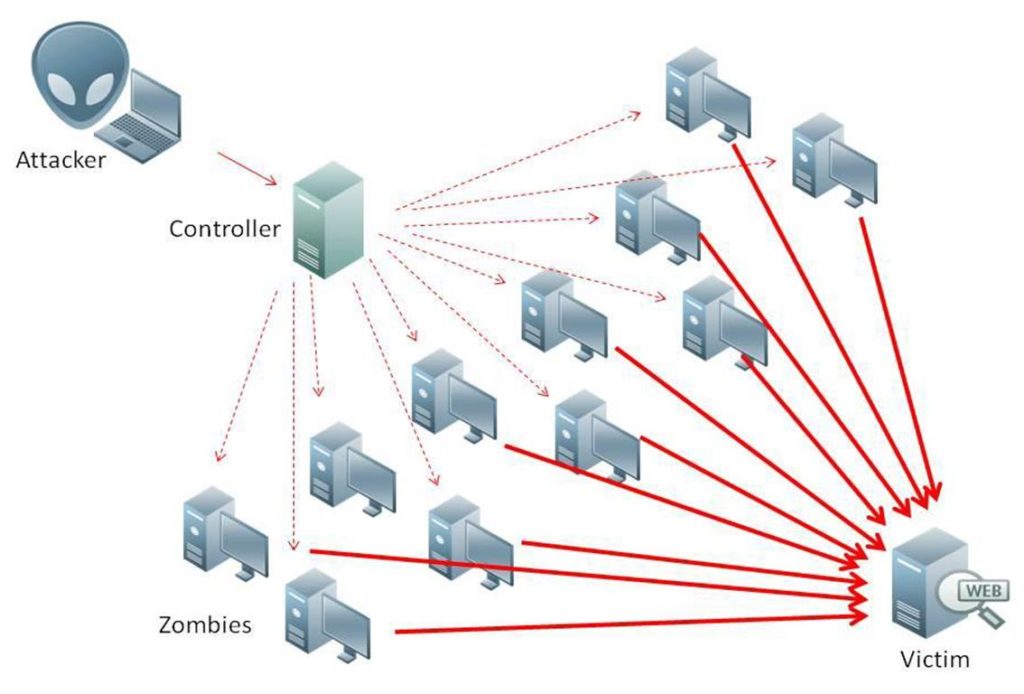
This is something I would like to keep track, so posting it here. Very useful and scary that how easily it can happen. Alert (TA14-017A) Following diagram shows how UDP based Amplification Attacks are carried out. Very simple, a 4MB ADSL connection can amplify upto 400MB traffiic easily. …
Read More »Notable Penetration Test Linux distributions of 2014
A penetration test, or the short form pentest, is an attack on a computer system with the intention of finding security weaknesses, potentially gaining access to it, its functionality and data. A Penetration Testing Linux is a special built Linux distro that can be used for analyzing and evaluating security …
Read More »Fix Metasploit error “The following options failed to validate: RHOSTS”
Fix Metasploit error “The following options failed to validate: RHOSTS” The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing …
Read More »How to fix “not starting portmapper is not running … (warning)” in Debian or Kali Linux?
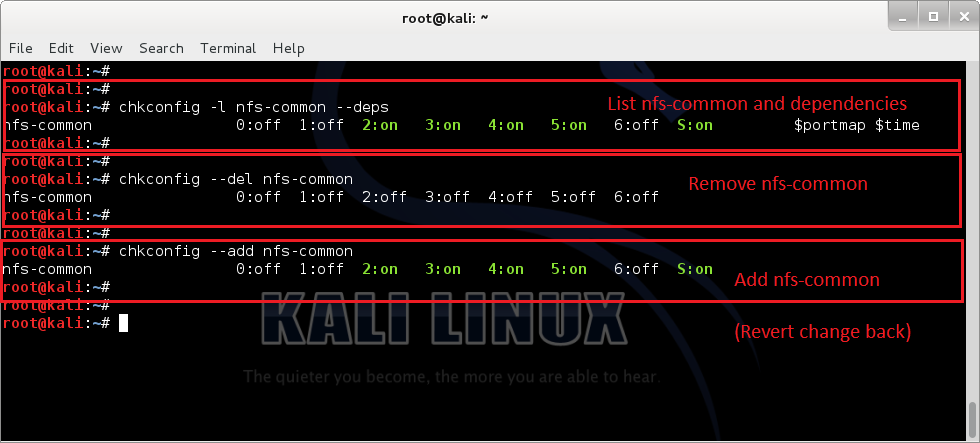
This is a small guide on How to fix “not starting portmapper is not running … (warning)” in Debian or Kali Linux. Fixing “not starting portmapper is not running … (warning)”: In most Kali or Debian installation users see this warning while booting their system. There’s two ways to fix …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….