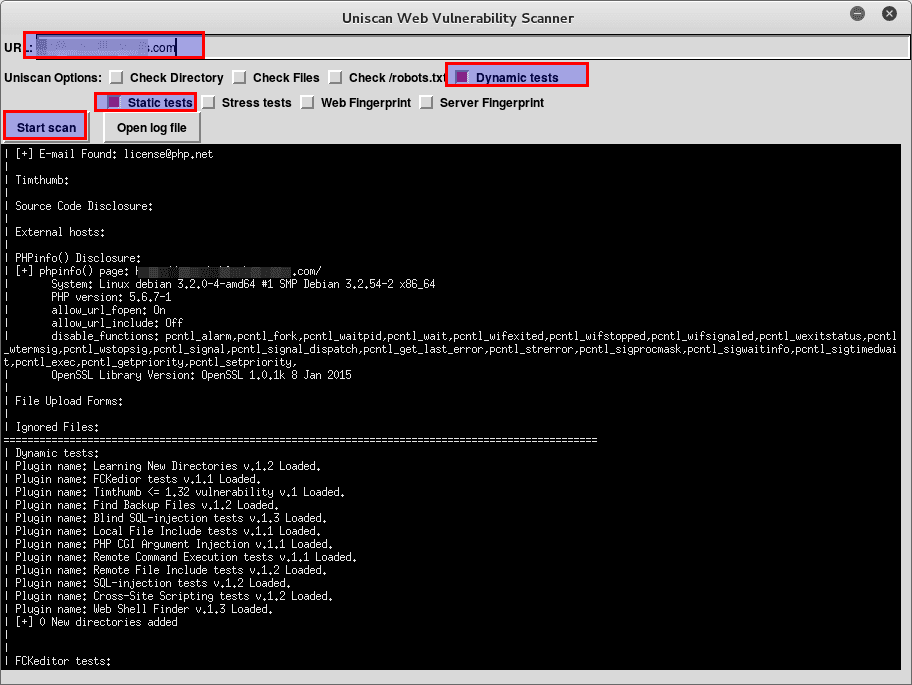
Uniscan is a simple Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. It’s a very simple yet quite powerful tool to scan website for vulnerabilities in Kali Linux (or any Linux as a matter of fact). It does the job fast and without hassle. You don’t …
Read More »DoS website using slowhttptest in Kali Linux – slowloris, slow HTTP POST and slow Read attack in one tool
SlowHTTPTest is a highly configurable tool that simulates some Application Layer Denial of Service attacks. It works on majority of Linux platforms, OSX and Cygwin – a Unix-like environment and command-line interface for Microsoft Windows. It implements most common low-bandwidth Application Layer DoS attacks, such as slowloris, Slow HTTP POST, …
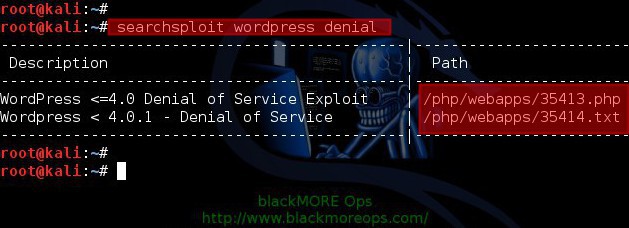
Read More »Denial of Service Attack Proof of Concept PHP Exploit for <=4.0 WordPress DoS Attack - CVE-2014-9034
Proof of Concept PHP exploit for WordPress DoS Attack CVE-2014-9034 worked like a charm on my own WordPress website. Surprisingly, CVE-2014-9034 was published for sometime and it seems WordPress still hasn’t fixed this issue. I will explain how to use this Proof of Concept tool and test your own WordPress …
Read More »Securing SSH with two factor authentication using Google Authenticator
Two-step verification (also known as Two-factor authentication, abbreviated to TFA) is a process involving two stages to verify the identity of an entity trying to access services in a computer or in a network. This is a special case of a multi-factor authentication which might involve only one of the …
Read More »Recommended books for Pentesters – A collection of books for Linux security administrators and pentesters
So you want to be pentester? A common question is where do you start? This post gives you a list of recommended books for Pentesters. It is useful for any Linux security administrators and aspiring pentesters or anyone who is interested to learn the basic workings of Penetration test with …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….