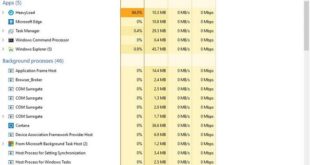
Everyone knows how to kill a process in Windows using Task Manager. However, when you’re on a Terminal Server Environment with 20 other users and you need to kill all matching processes on Windows from Command prompt it is just not possible because there might be 100 processes running. But …
Read More »124 legal hacking websites to practice and learn
Joe Shenouda is well known in The Netherlands as “The Netdetective” who has extensive experience in IT, ICS & Information Security as an international hands-on technical engineer, trainer, consultant & research fellow with a successful record in developing & leading technical corporate Cybersecurity programs for military & global organizations. He …
Read More »Publicly Available Tools Seen in Cyber Incidents Worldwide
Remote Access Trojan: JBiFrost First observed in May 2015, the JBiFrost RAT is a variant of the Adwind RAT, with roots stretching back to the Frutas RAT from 2012. A RAT is a program that, once installed on a victim’s machine, allows remote administrative control. In a malicious context, it …
Read More »Generate WiFi IVS dump with makeivs-ng on Kali Linux
makeivs-ng is part of the aircrack-ng package and is used to generate an IVS dump file with a given WEP key. The aim of the tool is to provide a way to create dumps with a known encryption key for testing. makeivs-ng – generate a dummy IVS dump file with …
Read More »Information gathering and correlation with Unicornscan on Kali Linux
Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the community to use under the terms of the GPL license. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….