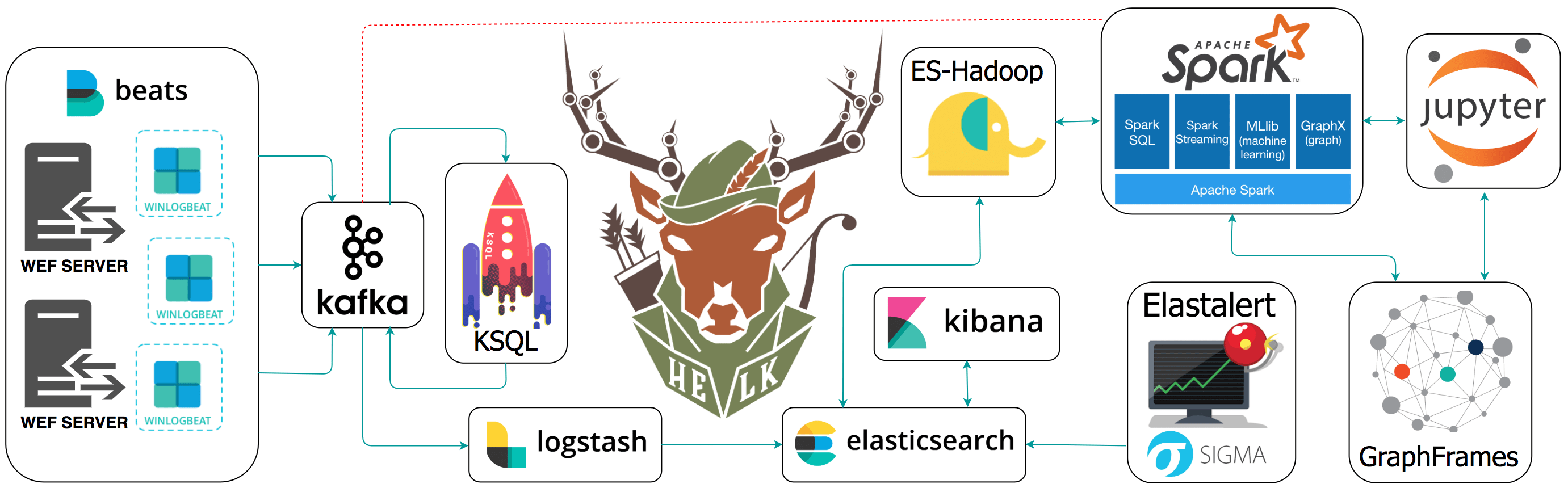
The Hunting ELK or simply the HELK is an Open Source Threat Hunting Platform with advanced analytics capabilities such as SQL declarative language, graphing, structured streaming, and even machine learning via Jupyter notebooks and Apache Spark over an ELK stack.
Read More »PuTTY alternatives
PuTTY is the most popular SSH client for Windows based systems. In fact it’s so popular that people actually install it in Linux (apt-get install putty)I. PuTTY is easy to use and you can save a lot of preferences. However, is PuTTY is best? To be honest, I think not. …
Read More »How to disable IPv6 in Linux?
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated …
Read More »IPv6 issues: Localized Denial-of-service caused by incorrect NXDOMAIN responses from AAAA queries
This is an unusual situation and a misconfiguration on DNS servers that can be exploited using a simple AAAA DNS query. This causes a localized Denial-of-service situation where users behind a specific resolver will get: Error: Unable to determine IP address from host name www.somevulnerablesite.com The DNS server returned: Name …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….