A quick guide on enabling AMD GPU for Hashcat on Kali Linux
Read More »BloodHound – Hacking Active Directory Trust Relationships
Tools for Hacking Active Directory Trust Relationships. BloodHound is for hacking active directory trust relationships and it uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment.
Read More »Accessing the RAID setup on an HP Proliant DL380 G7
Guide on accessing the RAID setup on an HP Proliant DL380 G7
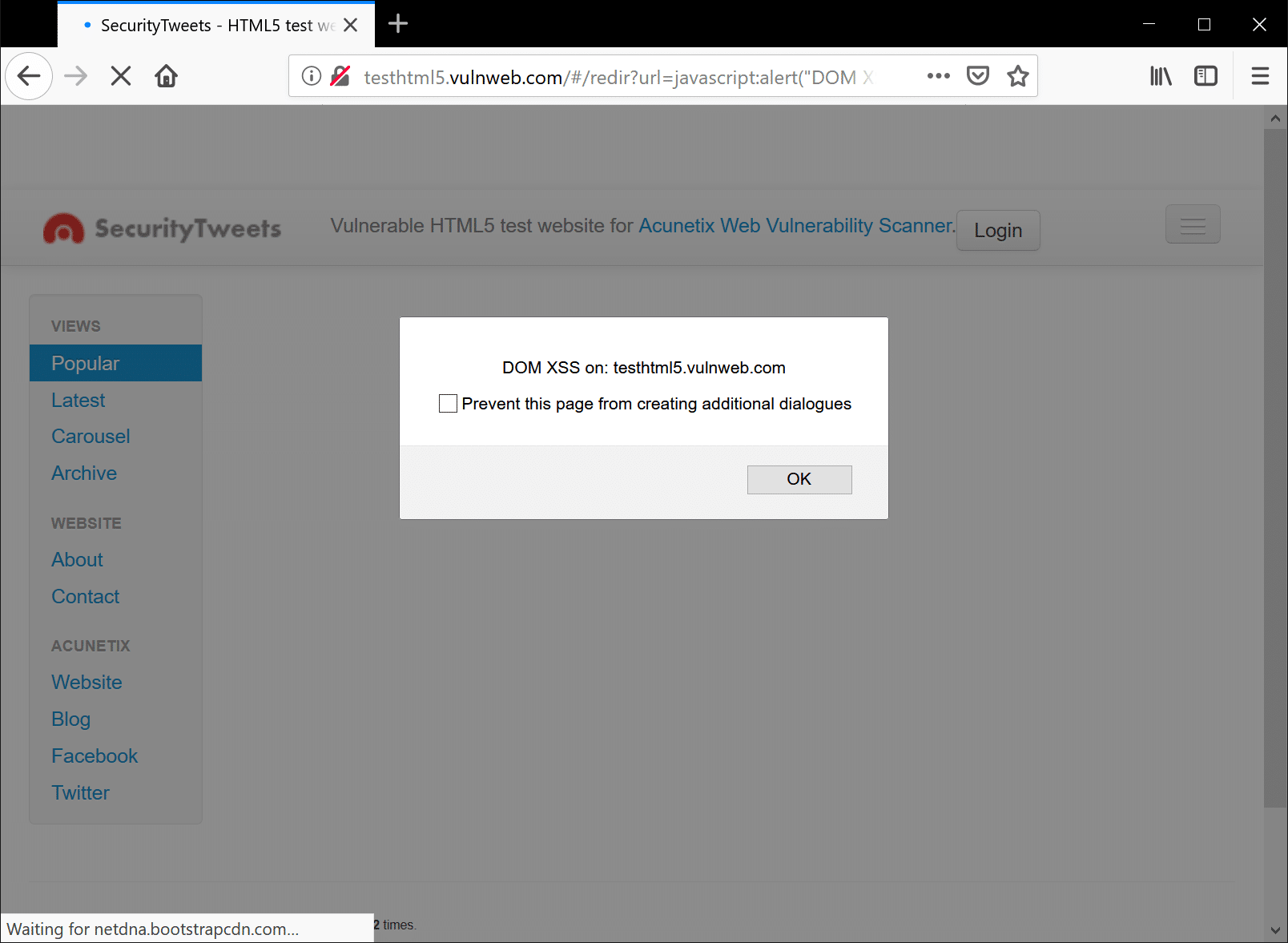
Read More »How to Prevent DOM-based Cross-site Scripting
There’s no denying the role that JavaScript has played in making web applications the sleek, interactive, online experiences that we know and love today. This powerful scripting language brought interactivity and animation to the web. But with great power comes great responsibility. Cross-site-scripting (XSS) remains a persistent stalwart among the …
Read More »Inception Attackers Target Europe with Year-old Office Vulnerability
The Inception attackers have been active since at least 2014 and have been documented previously by both Blue Coat and Symantec; historical attacks used custom malware for a variety of platforms, and targeting a range of industries, primarily in Russia, but also around the world. This blog describes attacks against …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….