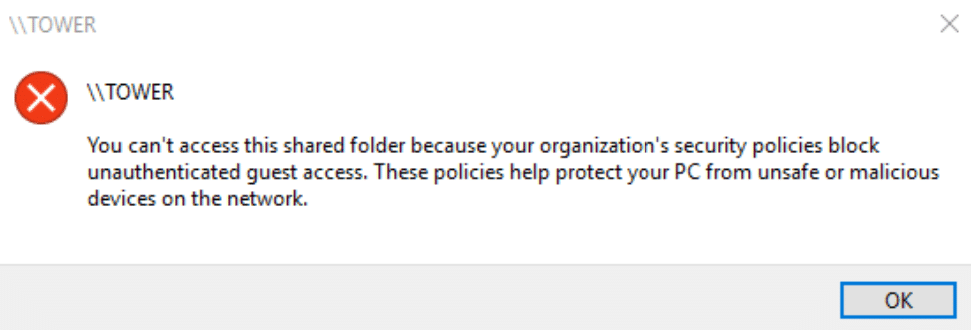
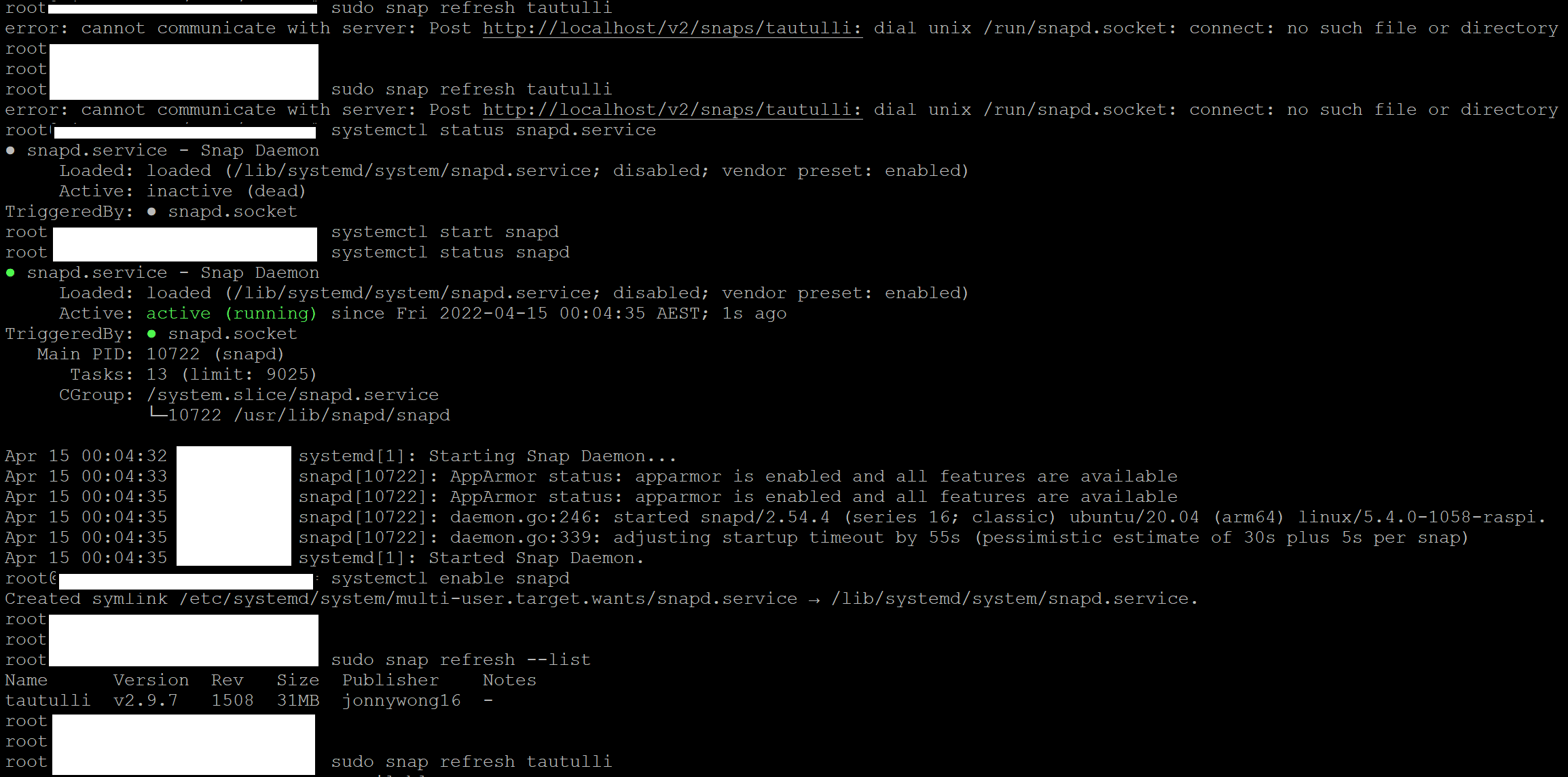
This is a pesky and annoying problem. I often lock …
Read More »
April 2, 2025
Netflix’s Chaos Monkey: Embracing Failure for Resilience
Netflix Chaos Monkey: Master system resilience by deliberately breaking things. Learn how this innov…
March 29, 2025
How to Install Unraid NAS: Complete Step-by-Step Guide for Beginners (2025)
Build your own powerful home server in 2025? Learn how to install Unraid NAS with our comprehensive …
March 27, 2025
Starter Guide on Hacking and Information Security: The Two Paths
The two distinct paths to mastering ethical hacking and cybersecurity: the easy "script kiddie" rout…
November 5, 2024
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never been…
June 18, 2024
Please use the command line updater because updating via browser is disabled in your config.php error on NextCloud
Received error upon launching Docker NextCloud on my Unraid server. Update needed Please use the com…
March 5, 2024
Whispers: A Powerful Static Code Analysis Tool for Credential Detection
“My little birds are everywhere, even in the North, they whisper to me the strangest stories.&…
March 5, 2024
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
If you’ve encountered an issue where Hashcat initially only recognizes your CPU and not the GP…
March 5, 2024
Identifying harmful activity on your captured traffic
This Python script utilises Wireshark or TCPdump to analyse network traffic stored in a specified .p…
May 20, 2023
Nyxt: Hacker’s Dream Browser
In the ever-evolving digital landscape, the demand for specialized tools and platforms has grown exp…
May 19, 2023
Migrate Plex Server – Ubuntu
To migrate your Plex server to a new Ubuntu server, you can follow these steps: 1. Set up the new Ub…
Recent Posts
-
Advantages disadvantages of using Proxy vs VPN vs TOR vs TOR and VPN together.
What makes you truly anonymous and leaves next to no …
Read More » -
How to Install Unraid NAS: Complete Step-by-Step Guide for Beginners (2025)
-
Free VPN providers of 2015
-
A very detailed guide on how to setup VPN on Kali Linux and Ubuntu
-
Cyber Actors Target Home and Office Routers and Networked Devices Worldwide
DHS and FBI recommend that all SOHO router owners power cycle …
Read More » -
Poll: Vote for best USB Wireless cards for Kali Linux
-
Generate WiFi IVS dump with makeivs-ng on Kali Linux
-
Crack a WEP key of an open network without user intervention with Wesside-ng
-
Browse anonymously in Kali Linux with Anonsurf
anonsurf allows you push your whole system via TOR network. …
Read More » -
HIDDEN COBRA – FASTCash Campaign targeting banks
-
How to benchmark Pyrit
-
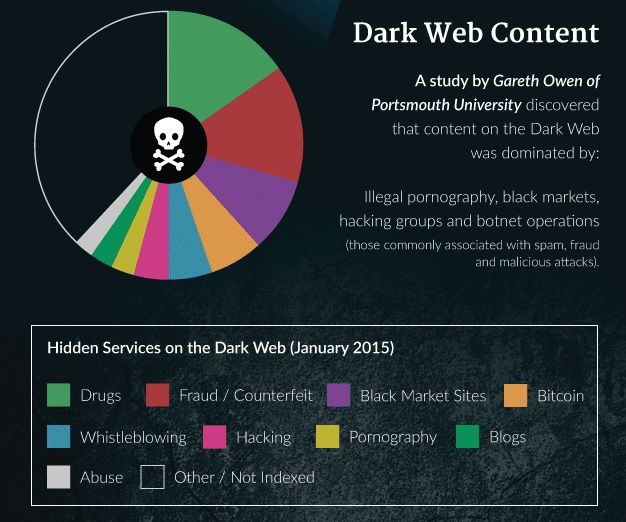
How to access Dark Web?
-
Output your microphone to a remote computers speaker
Output your microphone to a remote computers speaker
Read More » -
SSH through host in the middle
-
Three different ways to duplicate installed packages in multiple machines in Linux
-
ssh to machine behind shared NAT
-
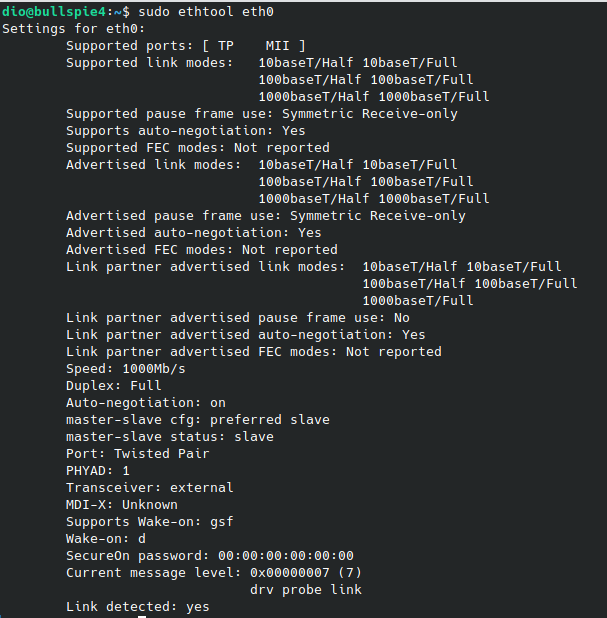
How to check Network Interface details in Linux
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….