This is a great video made by Assistant Professor Dr Mike Pound on how to make yourself root user on a computer using a buffer overflow attack in Kali Linux. Assistant Professor Dr Mike Pound details how it’s done in the following video:
Read More »Pay the Ransom or Face the Music – Hackers Threaten Apple Over iCloud Compromised Accounts
If you are an Apple user and thought that your data was secure, perhaps it’s time you retracted that thought. According to Motherboard, an Information and Technology Security magazine, a gang of hackers going by the name “Turkish Crime Family” allegedly claim a hold of over 200 million iCloud Compromised …
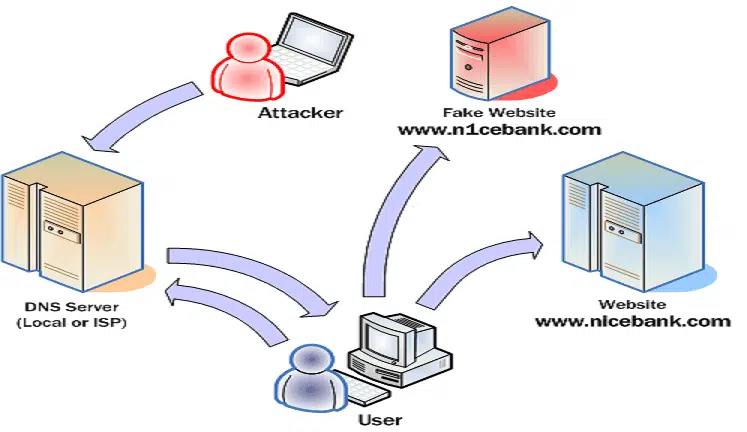
Read More »dns2proxy – Offensive DNS server post-explotation tool – DNS spoofing, phishing and pharming
dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim. This tools offers different features for post-explotation once you change the DNS server of a Victim. DNS spoofing, also referred to as DNS cache poisoning, is a form of …
Read More »Find Linux Exploits by Kernel version
Sometimes it’s really hard to find the correct exploit for the device that you are pentesting. I found two good references that may be helpful or least will give you a good starting point. Both of these resources can suggest Linux exploits based on kernel version. The first one is …
Read More »Steganography in Kali Linux – Hiding data in image
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Generally, the hidden messages appear to be (or be part of) something else: images, articles, shopping lists, or some other cover text. This post would cover Steganography in Kali Linux – …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….