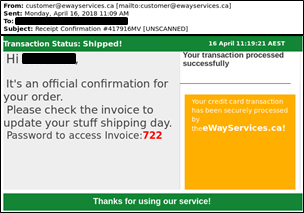
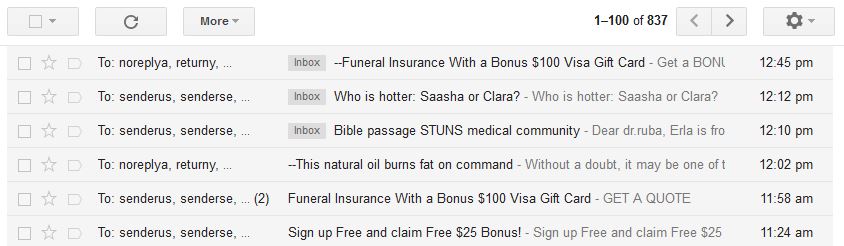
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate. Emotet continues to be among the most costly …
Read More »Using Rigorous Credential Control to Mitigate Trusted Network Exploitation
Recommended best practices for mitigating this threat include rigorous credential and privileged-access management, as well as remote-access control, and audits of legitimate remote-access logs. While these measures aim to prevent the initial attack vectors and the spread of malicious activity, there is no single proven threat response. Using a defense-in-depth …
Read More »Catching bad guys
Ever wondered how the good guys catch bad guys? I meant to say, what’s the process of catching bad guys who create virus, malware, crypto-lockers? It’s sort of a grey area and mostly not discussed very openly about the different methodologies used for Catching bad guys who create and distribute …
Read More »telus.com spam emails to gmail account
Just something I bumped into this morning and decided to quickly write a post. Woke up this morning and first thing I saw is a bunch of spam emails in my Gmail account. I kept getting these spam emails that are said to be sent by me but are sent …
Read More »How to add RBL on Zimbra Server?
A DNS-based Blackhole List (DNSBL) or Real-time Blackhole List (RBL) is an effort to stop email spamming. It is a “blacklist” of locations on the Internet reputed to send email spam. The locations consist of IP addresses which are most often used to publish the addresses of computers or networks …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….