Web application firewalls are usually placed in front of the web server to filter the malicious traffic coming towards server. If you arehired as a penetration tester for some company and they forgot to tell you that they are using web application firewall than you might get into a serious …
Read More »Targeting websites with Password Reset Poisoning
Most of web application security vulnerabilities, leverage user input in ways that were not initially intended by their developer(s). Password Reset Poisoning is one such vulnerability, that leverages commonly unthought of headers, such as the Host header seen in an HTTP request: GET https://example.com/[email protected] HTTP/1.1 Host: evilhost.com Notice the difference …
Read More »Setting up Damn Vulnerable Web Application (DVWA) – Pentesting Lab
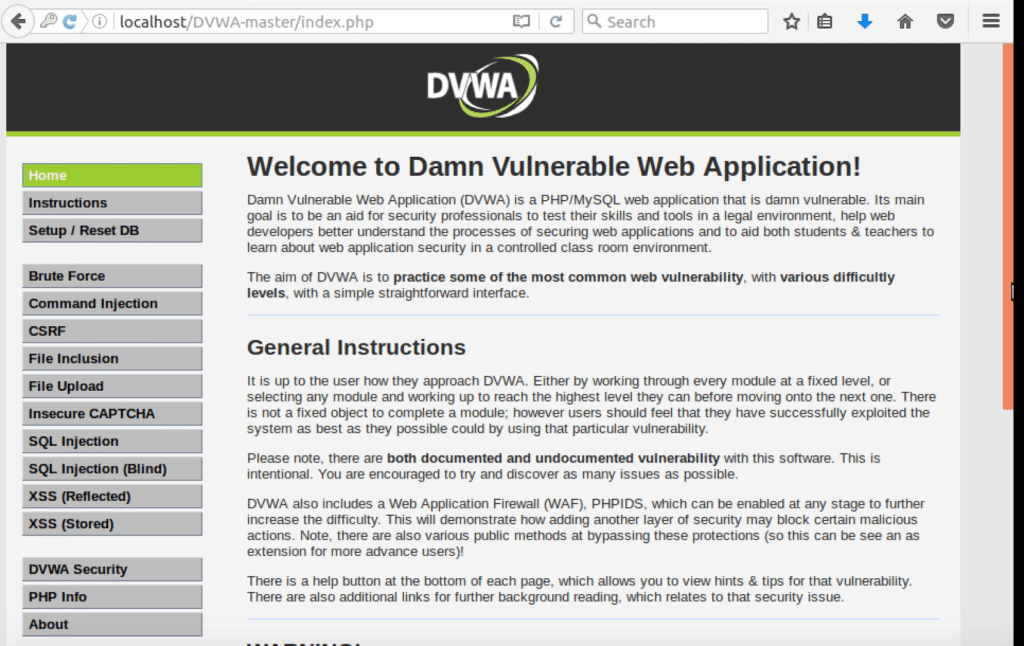
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to …
Read More »SecLists – Security Tester’s Companion
SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more. The goal is to enable a security tester to pull this repo …
Read More »124 legal hacking websites to practice and learn
List of 124 legal hacking websites to practice and learn
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….