This is a part 2 of the guide WPSCAN and quick wordpress security. It guides reader on how to fix Directory listing in WordPress. Read part 1 here WPSCAN and quick wordpress security – Part 1 Run WPSCAN WPSCAN shows I have Directory listing enabled. root@kali:~# wpscan --url www.blackmoreops.com _______________________________________________________________ …
Read More »How to benchmark Pyrit
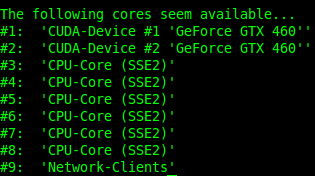
This is a short guide on How to benchmark Pyrit Assuming you managed to setup CUDA and Pyrit correctly, move on to the code section. If not, go back and follow this guide: How to Install Nvidia Kernel Module Cuda and Pyrit Benchmarking Pyrit: # pyrit benchmark The Pyrit …
Read More »How to Install Nvidia Kernel Module Cuda and Pyrit in Kali Linux
Install Nvidia Kernel Module Cuda and Pyrit in Kali Linux UPDATE: 13/03/2014 – Readers should follow these new guides that works flawlessly with Kali 1.0.6. Use this guide as a fallback. Install proprietary NVIDIA driver on Kali Linux – NVIDIA Accelerated Linux Graphics Driver Install NVIDIA driver kernel …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….