I had some interesting traffic showing up in my Google Analytics today. So far I’ve seen 21 referral traffic from forum.topic44122300.darodar.com to my home page http://www.blackmoreops.com/. Readers, I highly recommend reading comments section for more views and details. Making comments doesn’t require registration in this site, so you can leave …
Read More »Check for Shellshock Bash Vulnerability and how to fix it
A flaw was found in the way Bash evaluated certain specially crafted environment variables. An attacker could use this flaw to override or bypass environment restrictions to execute shell commands. Certain services and applications allow remote unauthenticated attackers to provide environment variables, allowing them to exploit this issue. In this …
Read More »Securing SSH with two factor authentication using Google Authenticator
Two-step verification (also known as Two-factor authentication, abbreviated to TFA) is a process involving two stages to verify the identity of an entity trying to access services in a computer or in a network. This is a special case of a multi-factor authentication which might involve only one of the …
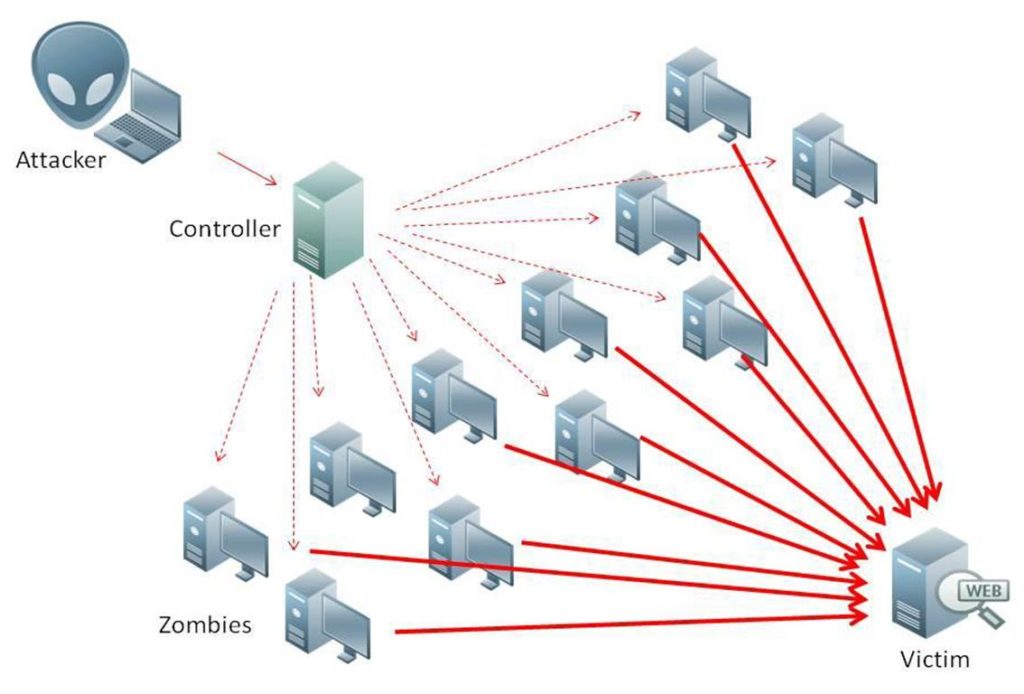
Read More »Alert (TA14-017A) – UDP based Amplification Attacks
This is something I would like to keep track, so posting it here. Very useful and scary that how easily it can happen. Alert (TA14-017A) Following diagram shows how UDP based Amplification Attacks are carried out. Very simple, a 4MB ADSL connection can amplify upto 400MB traffiic easily. …
Read More »802.11 Recommended USB Wireless Cards for Kali Linux
802.11 Recommended USB Wireless Cards for Kali Linux This post lists some of the best performing, supported and recommended USB Wireless Cards for Kali Linux. There isn’t a “best” card. There is whatever is right for YOU. Following recommended USB Wireless cards appears to be working for Kali Linux (i.e. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….