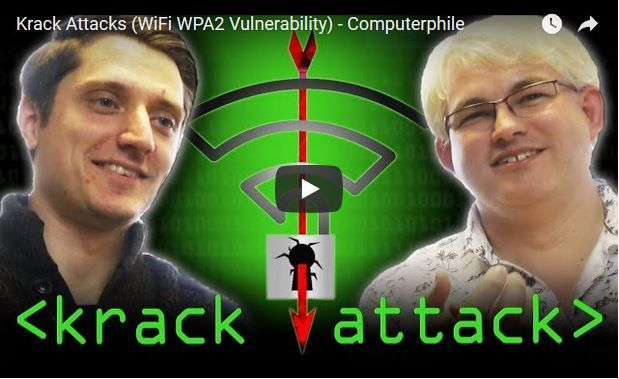
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. …
Read More »Fix Java error Unsigned application requesting unrestricted access to system
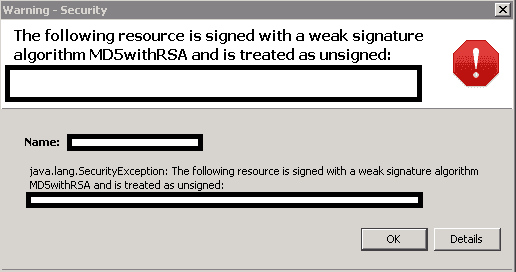
Tried to login to one of my server that requires Java and immediately got this error: Unsigned application requesting unrestricted access to system. The following resource is signed with a weak signature algorithm MD5withRSA and is treated as unsigned After some research on Google I found that the root cause …
Read More »Pay the Ransom or Face the Music – Hackers Threaten Apple Over iCloud Compromised Accounts
If you are an Apple user and thought that your data was secure, perhaps it’s time you retracted that thought. According to Motherboard, an Information and Technology Security magazine, a gang of hackers going by the name “Turkish Crime Family” allegedly claim a hold of over 200 million iCloud Compromised …
Read More »dns2proxy – Offensive DNS server post-explotation tool – DNS spoofing, phishing and pharming
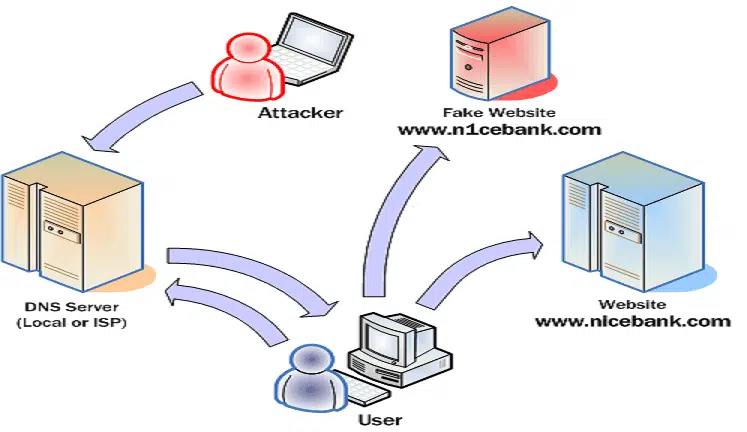
dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim. This tools offers different features for post-explotation once you change the DNS server of a Victim. DNS spoofing, also referred to as DNS cache poisoning, is a form of …
Read More »Encrypted EMail Service ProtonMail Opens Door for TOR Users
Let’s admit it: Privacy and Security are the two elements that matter most on our cyber cruising. Anyone including the government that sleuths on our online activities and data is not so welcome. The good news is that now even your email communication can happen in disguise through Tor network …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….