Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never been more straightforward. This comprehensive guide walks you through creating a complete AI development workspace, featuring NVIDIA CUDA for GPU acceleration, Ollama for local LLM hosting, Docker for containerization, and Stable Diffusion for AI image …
Read More »Penetration Testing Tools for Beginners
Penetration tools for beginners. Karkinos is a light-weight Beginner Friendly Penetration Testing Tool, which is basically a ‘Swiss Army Knife’ for pen-testing and/or hacking CTF’s.
Read More »Vulnerable docker environment for learning to hack
Vulhub is an open-source collection of pre-built vulnerable docker environment for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment.
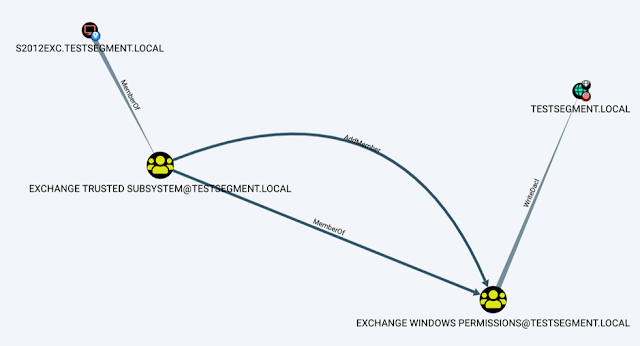
Read More »Exploit ACL Based Privilege Escalation Paths in Active Directory
Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a starting and ending point and will use Neo4j pathfinding algorithms to find the most efficient ACL based privilege escalation path.
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….