If you are an Apple user and thought that your data was secure, perhaps it’s time you retracted that thought. According to Motherboard, an Information and Technology Security magazine, a gang of hackers going by the name “Turkish Crime Family” allegedly claim a hold of over 200 million iCloud Compromised …
Read More »Kali Linux Cheat Sheet for Penetration Testers
Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. Kali Linux Cheat Sheet for Penetration testers is a high level overview for typical penetration testing environment ranging from nmap, sqlmap, ipv4, enumeration, fingerprinting …
Read More »Top 30 SSH shenanigans
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best known example application is for remote login to computer systems by users. SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with …
Read More »Take picture of unauthorized user trying to access your Laptop
Did you ever tried to guess your friends password? Did you ever tried to login to your partners password protected computer? Sounds silly and childish but many are guilty of it. Most cases it’s no big deal but I am sure all of us would like to know who tried …
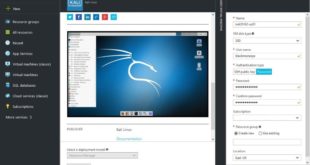
Read More »Run Kali Linux in Microsoft Azure on SSD for free
Big news for Kali Linux users, now you can run Kali Linux in Microsoft Azure cloud and that’s on super fast SSD! It seems Microsoft Azure Marketplace is adding more and more Linux distro including FreeBSD images in their repo. Just to make things better, you can technically run it …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….