Finding cPanel logs been always an issue for everyone. cPanel seems to distribute the logs in all over the disk. Saying that, cPanel got a nice Poster that you can print out but the PDF file is 42MB. This post is a collection of all the cPanel logs location for access, …
Read More »Determine if a disk is SSD or HDD
This is one of those random things I do and decided to put it in the website. I know that my personal computer is running on HDD, but when I am logged into a remote Linux system and suddenly I started wondering about how to determine if the underlying disk …
Read More »Regin Malware: Top-tier espionage tool enables stealthy surveillance
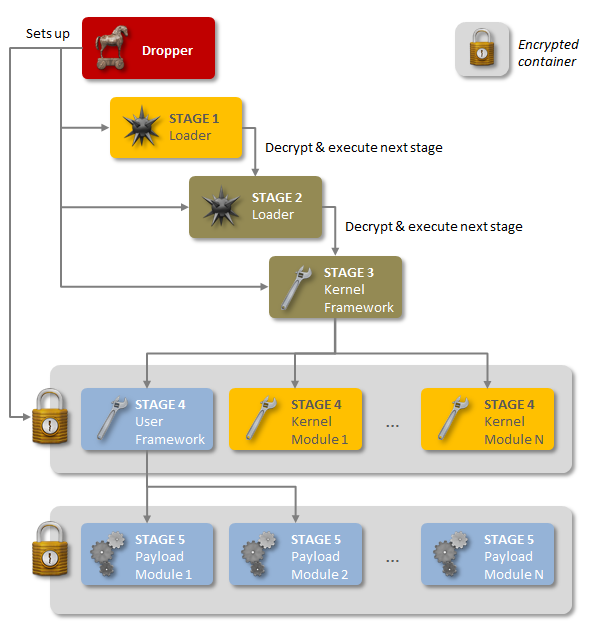
I don’t usually reblog or post others post in here. But this is something EVERYONE should be aware of. An advanced piece of malware, known as Regin Malware, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, …
Read More »No internet for me!
No Internet for me!!! I am moving to a much faster Fibre connection, so temporarily living on a Mobile Internet. This was me for first few hours: Then this happened! BoooYaaaa Feel free to comment via my Facebook or Twitter account …
Read More »Download accelerator manager for Linux – Flareget
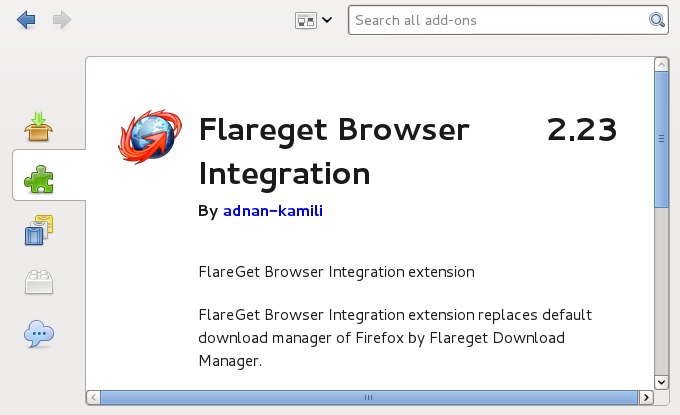
Before many started using Linux, we used Windows. One thing Windows gives you is plenty of softwares (well call them shareware’s if you want). In Windows did you use a download accelerator manager to download large files? Did you use FlashGet? or Internet Download Manager? Well, in Linux you can …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….