Easside-ng is an auto-magic tool which allows you to communicate via an WEP-encrypted access point (AP) without knowing the WEP key. It first identifies a network, then proceeds to associate with it, obtain PRGA (pseudo random generation algorithm) xor data, determine the network IP scheme and then setup a TAP …
Read More »Export VMware Workstation Virtual Network Settings
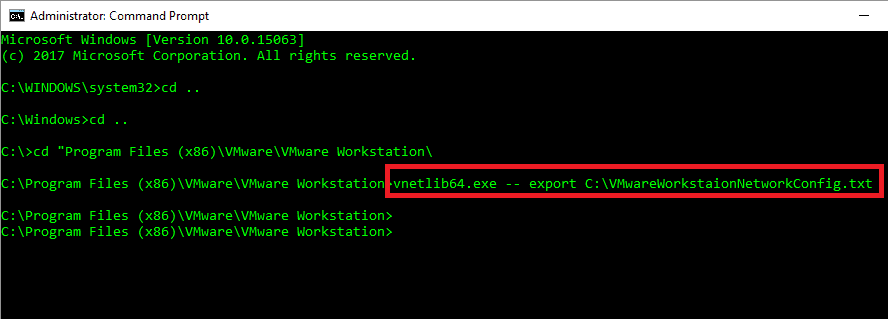
I am using VMware® Workstation 12 Pro and setup a very complex networking config with multiple NIC’s, DHCP, Host-Only and VLANs. I have 10 active VM’s that needs to setup a complex environment and most of these VM’s needs 3.5GB to 2GB RAM to run with 2vCPU each. I could …
Read More »Kali Linux Cheat Sheet for Penetration Testers
Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. Kali Linux Cheat Sheet for Penetration testers is a high level overview for typical penetration testing environment ranging from nmap, sqlmap, ipv4, enumeration, fingerprinting …
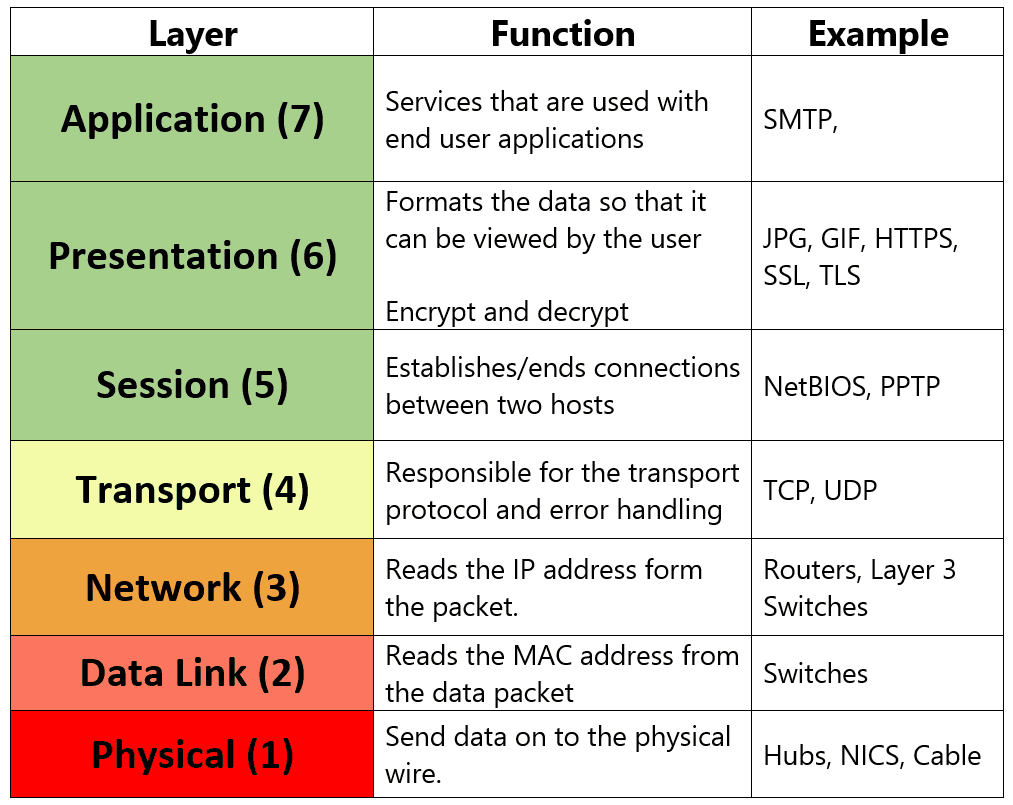
Read More »OSI Layers – Please Do Not Tell Secret Passwords Anytime
I had an interesting day at work trying to figure out how best I can setup a service for a client who is sending UDP licensing traffic through some high-end networking devices over VPN. UDP by design is unreliable. This was causing issues as the UDP packet size was over the …
Read More »Use arp-scan to find hidden devices in your network
The Address Resolution Protocol uses a simple message format containing one address resolution request or response. The size of the ARP message depends on the upper layer and lower layer address sizes, which are given by the type of networking protocol (usually IPv4) in use and the type of hardware …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….