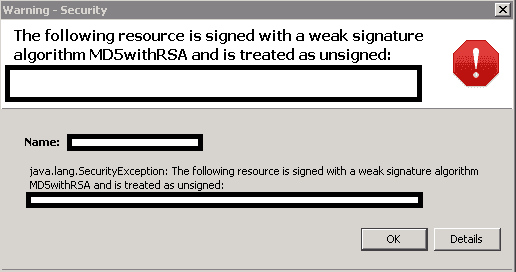
Tried to login to one of my server that requires Java and immediately got this error: Unsigned application requesting unrestricted access to system. The following resource is signed with a weak signature algorithm MD5withRSA and is treated as unsigned After some research on Google I found that the root cause …
Read More »Fix for Prolific USB to Serial RJ45 Ethernet Code 10 error
I use Prolific USB to RJ45 Ethernet dongle and I found that recently in almost any Windows version, I get Core 10 error. This guide shows how to fix Prolific USB to Serial or Prolific USB RJ45 Ethernet Code 10 error. This guide should work for Windows XP, Windows 7, Windows …
Read More »Kali Linux Cheat Sheet for Penetration Testers
Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. Kali Linux Cheat Sheet for Penetration testers is a high level overview for typical penetration testing environment ranging from nmap, sqlmap, ipv4, enumeration, fingerprinting …
Read More »Get help when your device is CryptoLocked
Law enforcement and IT Security companies have joined forces to disrupt cybercriminal businesses with ransomware connections. The “No More Ransom” website is an initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre and two cyber security companies – Kaspersky Lab and Intel Security …
Read More »Add timestamp to history command output in Linux
My last post was about adding timestamp to terminal in Linux. But isn’t it better to simply add timestamp to history command? This enables you to open your terminal anytime, run history command and find out when you ran which command, all without keeping terminal or putty windows open indefinitely. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….