Remote Access Trojan: JBiFrost First observed in May 2015, the JBiFrost RAT is a variant of the Adwind RAT, with roots stretching back to the Frutas RAT from 2012. A RAT is a program that, once installed on a victim’s machine, allows remote administrative control. In a malicious context, it …
Read More »Information gathering and correlation with Unicornscan on Kali Linux
Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the community to use under the terms of the GPL license. …
Read More »Install, setup, configure and run OpenVAS on Kali Linux
Vulnerability scanning is a crucial phase of a penetration test and having an updated vulnerability scanner in your security toolkit can often make a real difference by helping you discover overlooked vulnerable items. For this reason, we’ve manually packaged the latest and newly released OpenVAS 8.0 tool and libraries for …
Read More »Remove GRUB bootloader from Windows 10
My Razer 2016 laptop had Windows 10, Kali and Ubuntu installed but after a Windows update Linux partitions became inaccessible. I removed both Kali and Ubuntu partitions including SWAP but GRUB was till there. I needed to remove GRUB safely without breaking anything else and the following method on how …
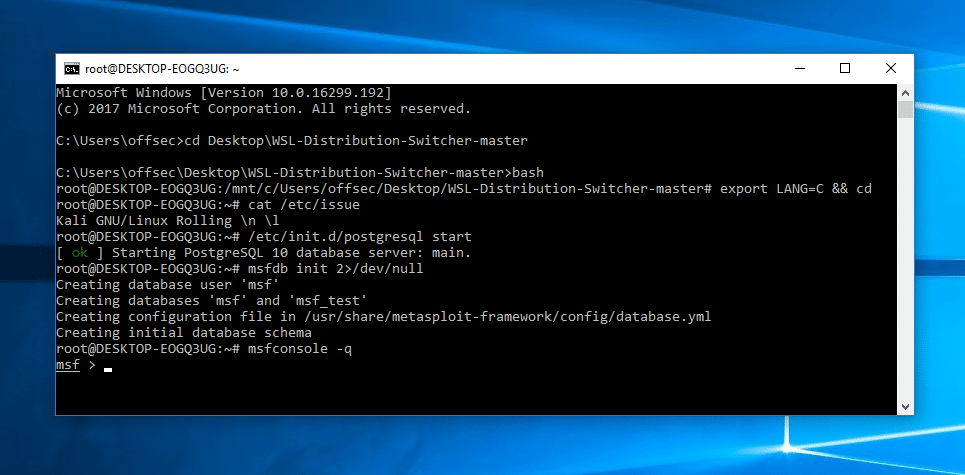
Read More »Kali Linux on Windows Subsystem for Linux
Kali Linux developers and Offensive Security team is always trying to find new ideas and better ways to run Kali Linux. With the recent introduction of Windows Subsystem for Linux (WSL) in Windows 10, it opened a new way to run Kali Linux. Tell me, do you play games? Sure. …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….