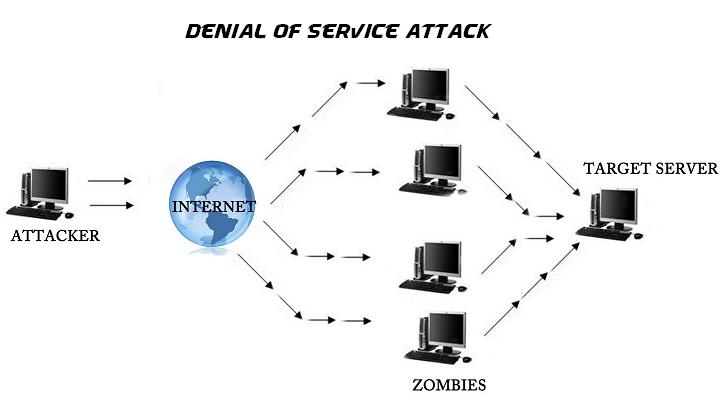
Short for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. Many DoS attacks, such as the Ping of Death and Teardrop attacks, exploit limitations in the TCP/IP protocols. We will review some of …
Read More »Install MATE Desktop in Kali Linux 2.x (Kali Sana)
MATE is a fork of GNOME 2. It provides an intuitive and attractive desktop environment using traditional metaphors for Linux and other Unix-like operating systems. MATE has forked a number of applications originating as the GNOME Core Applications, and developers have written several other applications from scratch. The forked applications …
Read More »Check download speed from Linux terminal
Lets say you are logged into a headless server (command line only) and you get a call about slow internet performance across network. Now of course there might be hundreds of reasons for slowness but you managed to narrow it down to the correction between your Gateway proxy and Upper …
Read More »Fixing E: Could not get lock /var/lib/dpkg/lock – open (11: Resource temporarily unavailable) error in Kali Linux
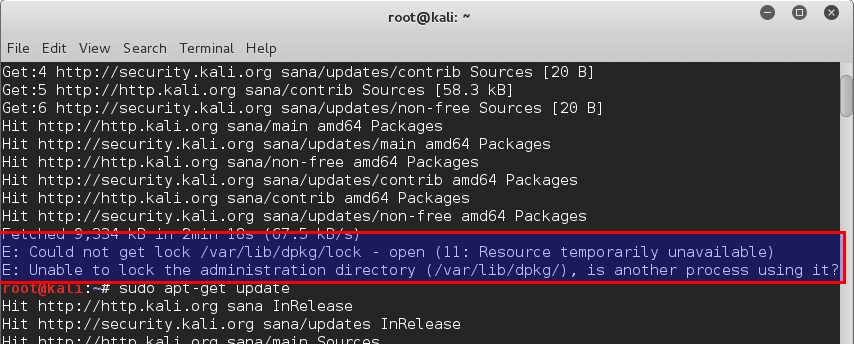
I just reinstalled Kali Linux in my PC and after my first logon, I tried to run apt-get update and had E: Could not get lock /var/lib/dpkg/lock - open (11: Resource temporarily unavailable) error coming up. Interesting, because I am the only user (I just installed the system) and there’s …
Read More »Fixing dpkg: warning: ‘ldconfig’ not found in PATH or not executable error when installing packages.
Overnight I had a new error in Kali Linux 2.0 – Kali Sana. I tried to install gimp and everything seemed going well. Except right at the point when it started installing gimp, I had the following errors coming up: root@kali:~# apt-get install gimp Reading package lists... Done Building dependency …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….