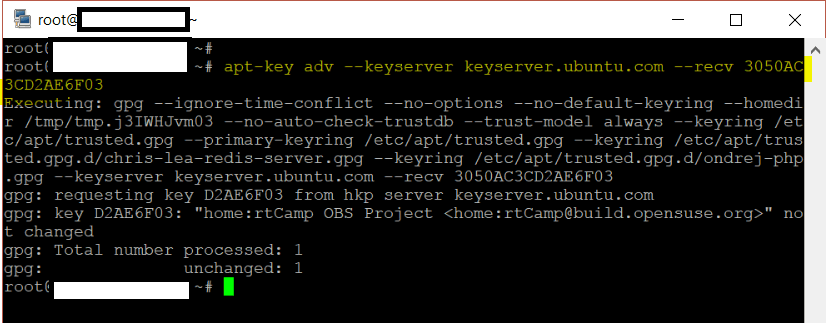
I was trying to update one of my server that has some Opensuse repositories and received this error “W: GPG error: http://download.opensuse.org Release: The following signatures were invalid: KEYEXPIRED 1501595774” root@someserver:~# apt-get update . . . ---SNIP---- Ign http://download.opensuse.org Translation-en Fetched 481 B in 4s (97 B/s) Reading package lists... …
Read More »Fix Java error Unsigned application requesting unrestricted access to system
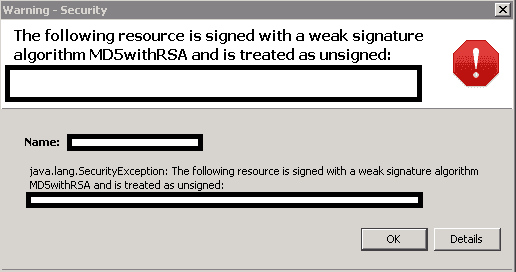
Tried to login to one of my server that requires Java and immediately got this error: Unsigned application requesting unrestricted access to system. The following resource is signed with a weak signature algorithm MD5withRSA and is treated as unsigned After some research on Google I found that the root cause …
Read More »USB and SSD drive speedtest in Linux
The speed of a drive is measured in terms of how much data it can read or write in unit time. The dd command is a simple command line tool that can be used to read and write arbitrary blocks of data to a drive and measure the speed at …
Read More »Encrypted EMail Service ProtonMail Opens Door for TOR Users
Let’s admit it: Privacy and Security are the two elements that matter most on our cyber cruising. Anyone including the government that sleuths on our online activities and data is not so welcome. The good news is that now even your email communication can happen in disguise through Tor network …
Read More »How to install VirtualBox Guest Additions in Kali Linux (Kali Rolling / Kali Linux 2016.2 / Kali 2017)
Since Kali Linux 2016 came out (also known as Kali Rolling), it seems that Official VirtualBox guest addition doesn’t work well anymore. It also created lots of confusion and debate as when someone asks for help, they don’t always specify which version of Kali they are using and that leads …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….