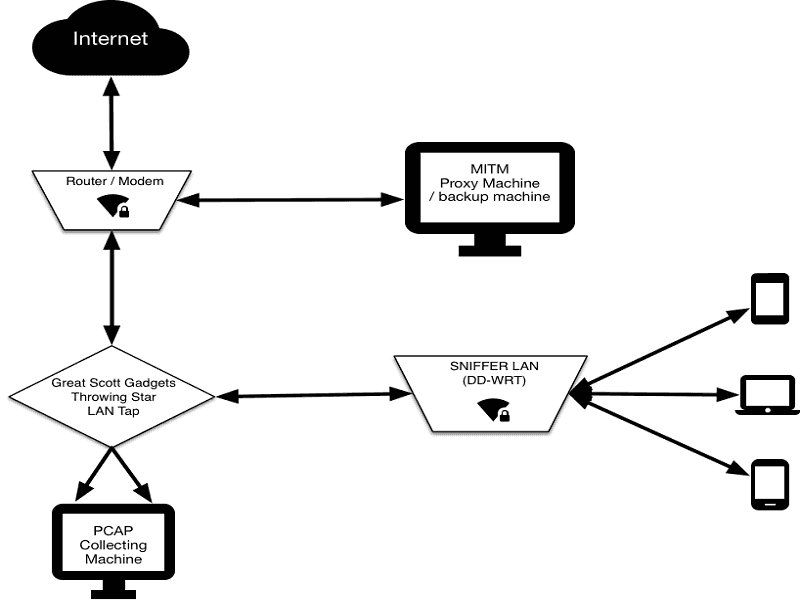
Snifflab is a technical test environment for capturing and decrypting WiFi data transmissions. Snifflab creates a WiFi hotspot that is continually collecting all the packets sent over it. All connected clients’ HTTPS communications are subjected to a “Man-in-the-middle” attack, whereby they can later be decrypted for analysis. This article presents …
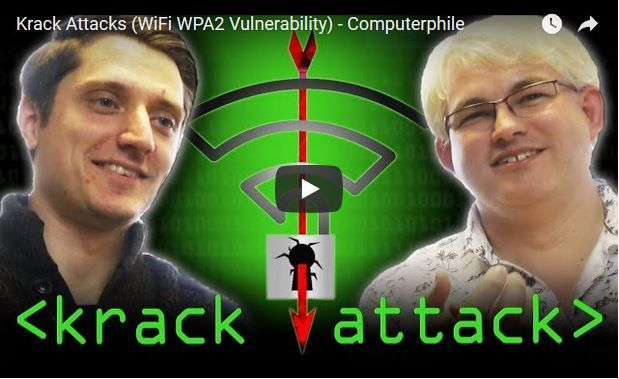
Read More »Wireless WPA2 password cracking using KRACK attacks
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. …
Read More »Buffer overflow attack in Kali Linux
This is a great video made by Assistant Professor Dr Mike Pound on how to make yourself root user on a computer using a buffer overflow attack in Kali Linux. Assistant Professor Dr Mike Pound details how it’s done in the following video:
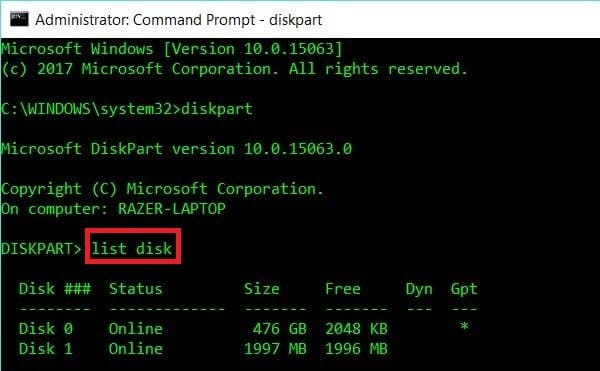
Read More »Format Linux USB Drive to recover full disk space in Windows 10
This is quite a common problem when you have a USB Disk that was used to burn a Bootable Linux distro is dd mode. You plug in the USB drive in Windows 10 (or any windows for that fact) and all you see is a Drive with zero MB disk …
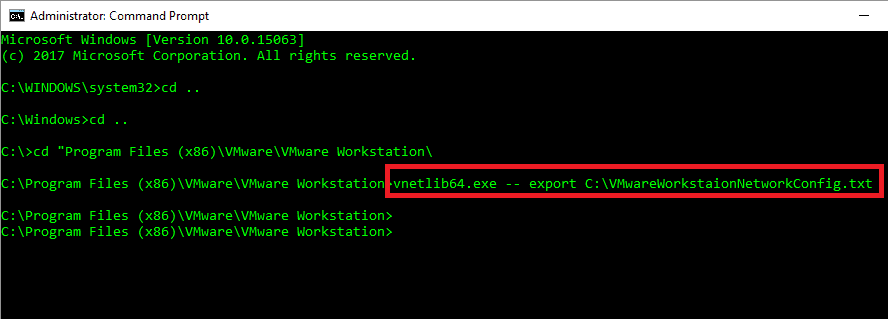
Read More »Export VMware Workstation Virtual Network Settings
I am using VMware® Workstation 12 Pro and setup a very complex networking config with multiple NIC’s, DHCP, Host-Only and VLANs. I have 10 active VM’s that needs to setup a complex environment and most of these VM’s needs 3.5GB to 2GB RAM to run with 2vCPU each. I could …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….