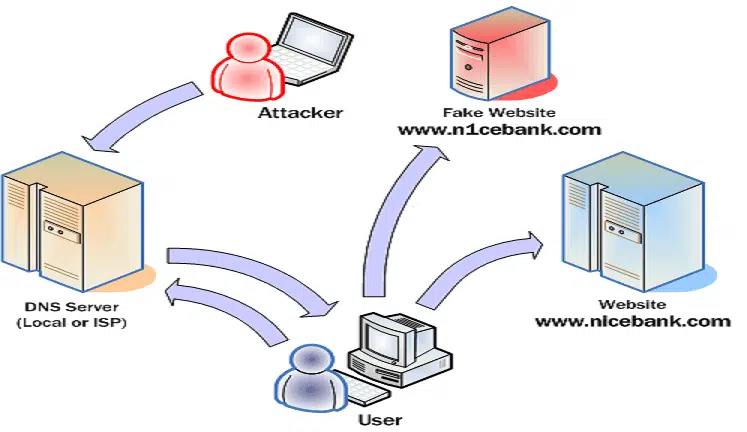
dns2proxy is an offensive DNS server that offers various features for post-exploitation once you’ve changed the DNS server of a victim. This tools offers different features for post-explotation once you change the DNS server of a Victim. DNS spoofing, also referred to as DNS cache poisoning, is a form of …
Read More »Encrypted EMail Service ProtonMail Opens Door for TOR Users
Let’s admit it: Privacy and Security are the two elements that matter most on our cyber cruising. Anyone including the government that sleuths on our online activities and data is not so welcome. The good news is that now even your email communication can happen in disguise through Tor network …
Read More »How to install VirtualBox Guest Additions in Kali Linux (Kali Rolling / Kali Linux 2016.2 / Kali 2017)
Since Kali Linux 2016 came out (also known as Kali Rolling), it seems that Official VirtualBox guest addition doesn’t work well anymore. It also created lots of confusion and debate as when someone asks for help, they don’t always specify which version of Kali they are using and that leads …
Read More »Android Banking Trojan Virus code leaks and sparks copycats immediately
In the dark tech world, it is uncommon for virus coders to develop Android banking Trojans and distribute their source code for free to the public. However, according to Dr. Web, a Russian security firm, a dark web hacker forum recently released freely the code of such a malicious app …
Read More »Find Linux Exploits by Kernel version
Sometimes it’s really hard to find the correct exploit for the device that you are pentesting. I found two good references that may be helpful or least will give you a good starting point. Both of these resources can suggest Linux exploits based on kernel version. The first one is …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….