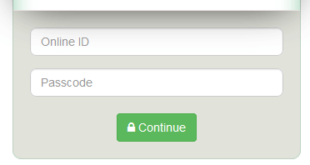
In the dark tech world, it is uncommon for virus coders to develop Android banking Trojans and distribute their source code for free to the public. However, according to Dr. Web, a Russian security firm, a dark web hacker forum recently released freely the code of such a malicious app …
Read More »Find Linux Exploits by Kernel version
Sometimes it’s really hard to find the correct exploit for the device that you are pentesting. I found two good references that may be helpful or least will give you a good starting point. Both of these resources can suggest Linux exploits based on kernel version. The first one is …
Read More »Steganography in Kali Linux – Hiding data in image
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Generally, the hidden messages appear to be (or be part of) something else: images, articles, shopping lists, or some other cover text. This post would cover Steganography in Kali Linux – …
Read More »Shortest spam run ever – domaincop.org Domain Abuse Notice Spam
Woke up this morning and found two emails from domaincorp.org in my Inbox stating my domains are being used for spamming and spreading malware recently. Subject line contained “Domain Abuse Notice” which looked serious!
Read More »Hacking QNX systems over QCONN
This is a simple user submitted guide on Hacking QNX systems over QCONN port(8000). In case you are wondering what is a QNX system, QNX is a mobile operating system that was originally developed for embedded systems. The operating system’s developer, QNX Software Systems, was acquired by Research in Motion …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….