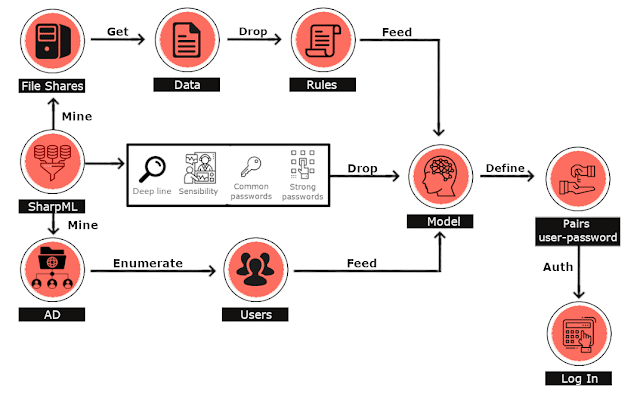
SharpML is a proof of concept file share data mining tool using Machine Learning in Python and C#. The tool is discussed in more detail on this blog here, but is summarised below also. SharpML performs a number of operations with a view to mining file shares, querying Active Directory for users, dropping an ML model and associated rules, performing Active Directory authentication checks, with a view to automating the process of hunting for passwords in file shares by feeding the mined data into the ML model.
Read More »Vulnerable docker environment for learning to hack
Vulhub is an open-source collection of pre-built vulnerable docker environment for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment.
Read More »Exploit ACL Based Privilege Escalation Paths in Active Directory
Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a starting and ending point and will use Neo4j pathfinding algorithms to find the most efficient ACL based privilege escalation path.
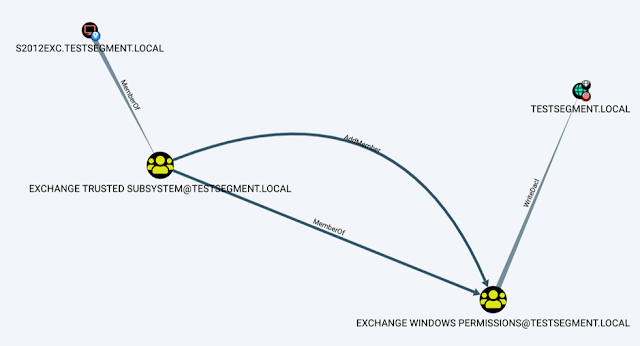
Read More »BloodHound – Hacking Active Directory Trust Relationships
Tools for Hacking Active Directory Trust Relationships. BloodHound is for hacking active directory trust relationships and it uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment.
Read More »Change IP address in packet capture file (faking IP)
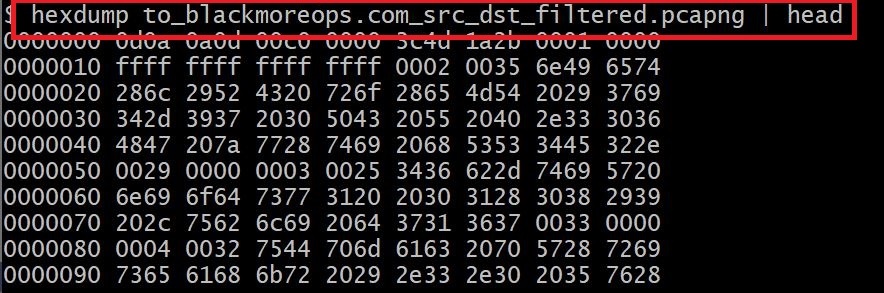
I'm sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you're trying to send the capture file to someone that you don't really share your real IP's with or you just want to change cause you can. If you've tried this and looked around the interwebs, you'd surely know that there's not many guides available and most people would just tell casually "just use sed" or use "WireEdit" and pay some fees for their license. Now, both works but I just got pissed off in a particular situation where sed wasn't an options (the file was literally few GB's in size and most text editors would just freeze) and to make things worse, I needed to filter a lot of info and only keep source and destination IP addresses in there for privacy's sake. Yeah, that means removing all those noises like DNS, UDP, Broadcast, Cisco ARP, Broadcast, MDNS (yes, that too), SSDP ... yes, pretty much anything except TCP/UDP, HTTP and TLS trarffic between my server and the destination server. So, in summary I had to filter all of these noises and change IP address in packet capture file to hide source IP address, this is similar to faking IP address in packet captures. You can also use other tools to do it on the fly but they require more setup and all I just wanted to do is to hide my source IP.
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….