The two distinct paths to mastering ethical hacking and cybersecurity: the easy "script kiddie" route versus the professional CTF approach. This comprehensive guide reveals how to develop genuine hacking skills through competitive Capture The Flag competitions, with links to 19+ top practice platforms for beginners. Learn why understanding computer systems from the ground up is essential for a successful career in information security.
Read More »Free Android Penetration Testing Toolkit & Risk Assessment
Free Android Penetration Testing Toolkit & Risk Assessment
Read More »Penetration Testing Tools for Beginners
Penetration tools for beginners. Karkinos is a light-weight Beginner Friendly Penetration Testing Tool, which is basically a ‘Swiss Army Knife’ for pen-testing and/or hacking CTF’s.
Read More »Detect SQL Injection (SQLi) and XSS
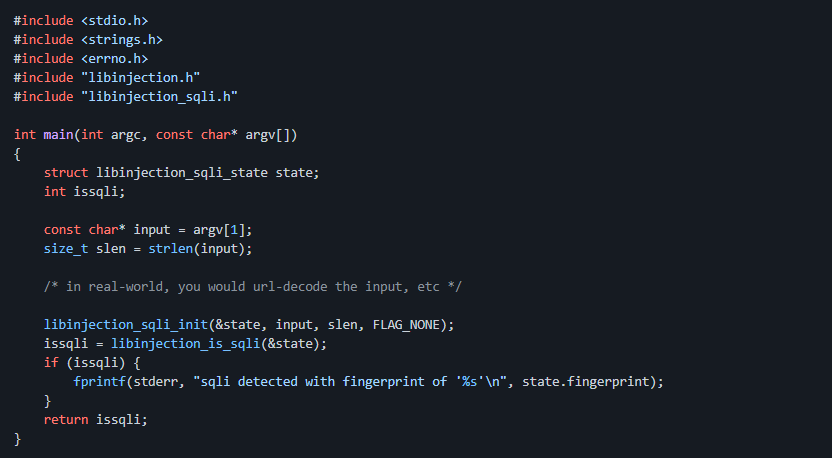
SQLi and other injection attacks remain the top OWASP and CERT vulnerability. Current detection attempts frequently involve a myriad of regular expressions which are not only brittle and error-prone but also proven by Hanson and Patterson at Black Hat 2005 to never be a complete solution. LibInjection is a new open-source C library that detects SQLi using lexical analysis. With little upfront knowledge of what SQLi is, the algorithm has been trained on tens of thousands of real SQLi attacks and hundreds of millions of user inputs taken from a Top 50 website for high precision and accuracy.
Read More »Machine Learning Network Share Password Hunting Toolkit
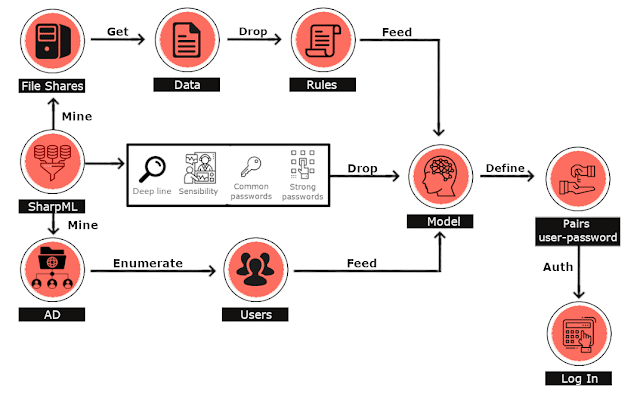
SharpML is a proof of concept file share data mining tool using Machine Learning in Python and C#. The tool is discussed in more detail on this blog here, but is summarised below also. SharpML performs a number of operations with a view to mining file shares, querying Active Directory for users, dropping an ML model and associated rules, performing Active Directory authentication checks, with a view to automating the process of hunting for passwords in file shares by feeding the mined data into the ML model.
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….