The Pentbox is a safety kit containing various tools for streamlining PenTest conducting a job easily. It is programmed in Ruby and oriented to GNU / Linux, with support for Windows, MacOS and every systems where Ruby is installed. In this small article we will explain how to set up …
Read More »New Mozilla Firefox Version 37.0 fixed 13 security issues and introduced Opportunistic Encryption support
Mozilla Foundation just released it’s latest Firefox (Version 37.0). It’s been rolled out for Windows, Mac, Linux and Android operating systems. Those who don’t know, it was released on the week of March 31st. Well to be honest, as of writing this article, Version 37.0.1 was already out on April …
Read More »How to Install Google Chrome in Kali Linux? – Part 3 – Running Chrome
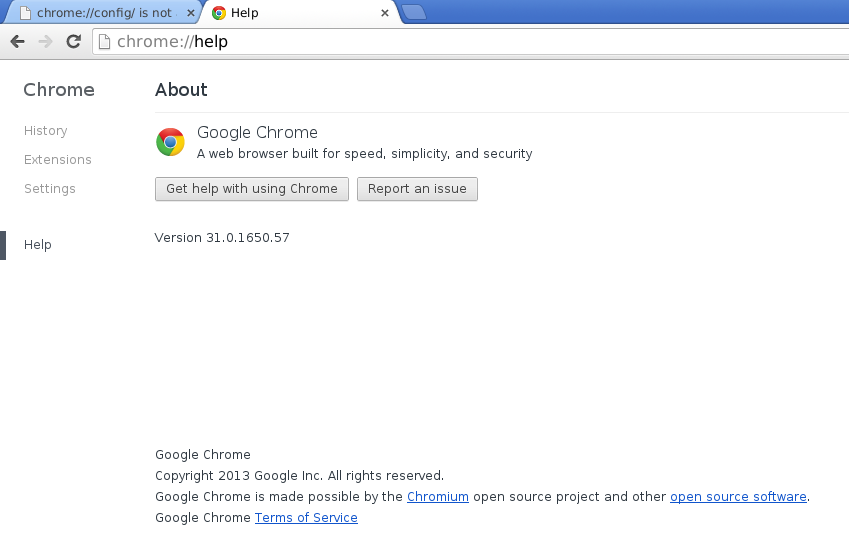
Continued from How to Install Google Chrome in Kali Linux? – Part 2 – Installation Running Google Chrome in Kali Linux You have follow choices to run Google Chrome in Kali Linux: Run Google Chrome as a Standard user in Kali Linux Create a Standard non-root user and run Google …
Read More »How to Install Google Chrome in Kali Linux? – Part 2 – Installation
Install Google Chrome in Kali Linux: From our previous post (How to Install Google Chrome in Kali Linux? – Part 1 – Discussion)we know that we can install Google Chrome in two different ways: Download and Install .deb package from Google. Install Google Chrome by adding Google Repositories Let’s …
Read More »How to Install Google Chrome in Kali Linux? – Part 1 – Discussion
Google Chrome is a web browser developed by Google. It used the WebKit layout engine until version 27 and, with the exception of its iOS releases, from version 28 and beyond uses the WebKit fork Blink. It was first released as a beta version for Microsoft Windows on September 2, …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….