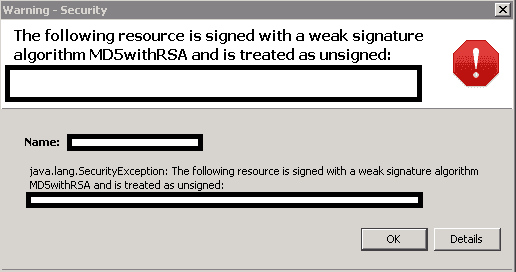
Tried to login to one of my server that requires Java and immediately got this error: Unsigned application requesting unrestricted access to system. The following resource is signed with a weak signature algorithm MD5withRSA and is treated as unsigned After some research on Google I found that the root cause …
Read More »Encrypted EMail Service ProtonMail Opens Door for TOR Users
Let’s admit it: Privacy and Security are the two elements that matter most on our cyber cruising. Anyone including the government that sleuths on our online activities and data is not so welcome. The good news is that now even your email communication can happen in disguise through Tor network …
Read More »Kali Linux Cheat Sheet for Penetration Testers
Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. Kali Linux Cheat Sheet for Penetration testers is a high level overview for typical penetration testing environment ranging from nmap, sqlmap, ipv4, enumeration, fingerprinting …
Read More »How to add RBL on Zimbra Server?
A DNS-based Blackhole List (DNSBL) or Real-time Blackhole List (RBL) is an effort to stop email spamming. It is a “blacklist” of locations on the Internet reputed to send email spam. The locations consist of IP addresses which are most often used to publish the addresses of computers or networks …
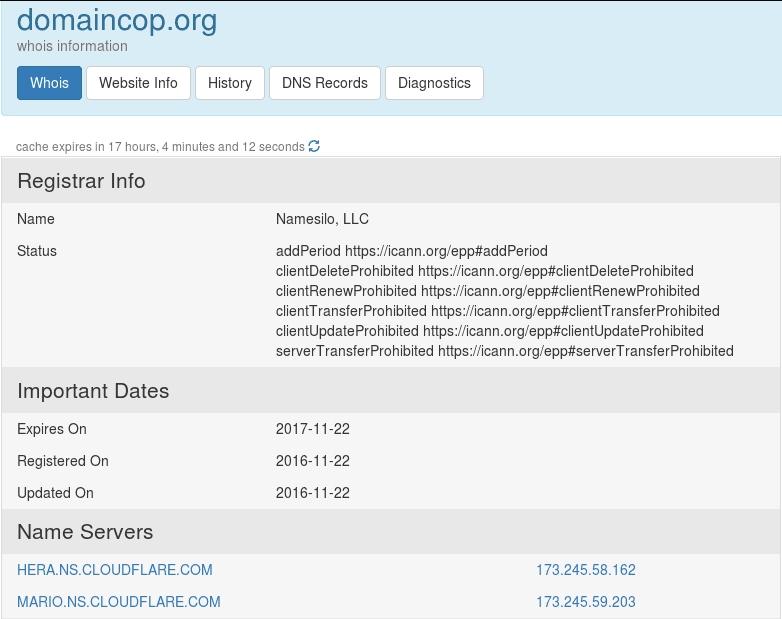
Read More »Shortest spam run ever – domaincop.org Domain Abuse Notice Spam
Woke up this morning and found two emails from domaincorp.org in my Inbox stating my domains are being used for spamming and spreading malware recently. Subject line contained “Domain Abuse Notice” which looked serious!
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….