SSL (Secure Sockets Layer) is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral. SSL is an industry standard and is used by millions of websites …
Read More »Install, setup, configure and run OpenVAS on Kali Linux
Vulnerability scanning is a crucial phase of a penetration test and having an updated vulnerability scanner in your security toolkit can often make a real difference by helping you discover overlooked vulnerable items. For this reason, we’ve manually packaged the latest and newly released OpenVAS 8.0 tool and libraries for …
Read More »Catching bad guys
Ever wondered how the good guys catch bad guys? I meant to say, what’s the process of catching bad guys who create virus, malware, crypto-lockers? It’s sort of a grey area and mostly not discussed very openly about the different methodologies used for Catching bad guys who create and distribute …
Read More »PuTTY alternatives
PuTTY is the most popular SSH client for Windows based systems. In fact it’s so popular that people actually install it in Linux (apt-get install putty)I. PuTTY is easy to use and you can save a lot of preferences. However, is PuTTY is best? To be honest, I think not. …
Read More »Meltdown and Spectre – Severe CPU vulnerabilities
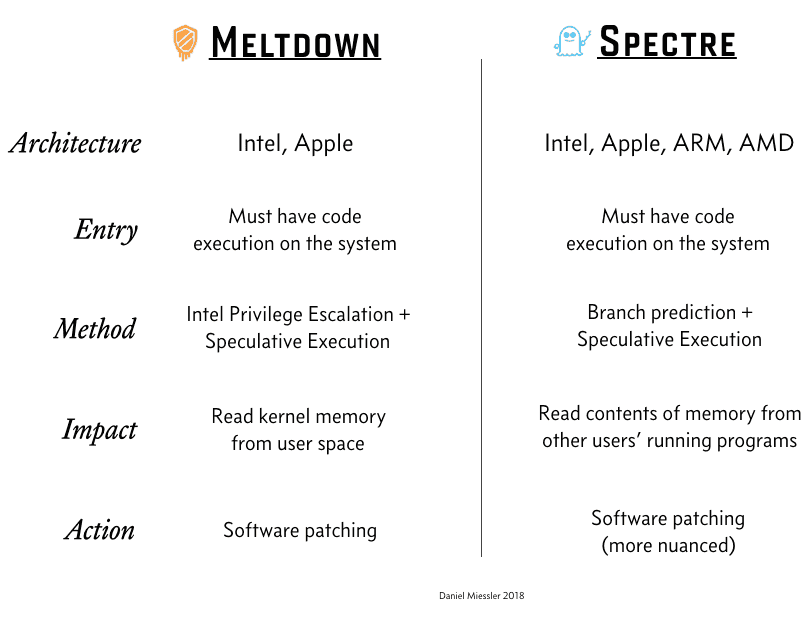
During the first week of January 2018, the world has been plunged into hot and anxious discussions concerning two newly discovered vulnerabilities in nearly all major ARM-based CPUs including smartphones, tablets, and some computers. The vulnerability itself even extends to the IBM’s POWER processors which run nearly all supercomputers! Starting …
Read More » blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….