During the first week of January 2018, the world has been plunged into hot and anxious discussions concerning two newly discovered vulnerabilities in nearly all major ARM-based CPUs including smartphones, tablets, and some computers. The vulnerability itself even extends to the IBM’s POWER processors which run nearly all supercomputers! Starting to get worried? For now, you shouldn’t because this article attempts to explain the details of the vulnerabilities including what you can, and what you can’t do. On January 3rd, 2018, Google Project Zero disclosed the two major vulnerabilities dubbed Meltdown and Spectre which threatens virtually all devices regardless of the operating system or the manufacturer.
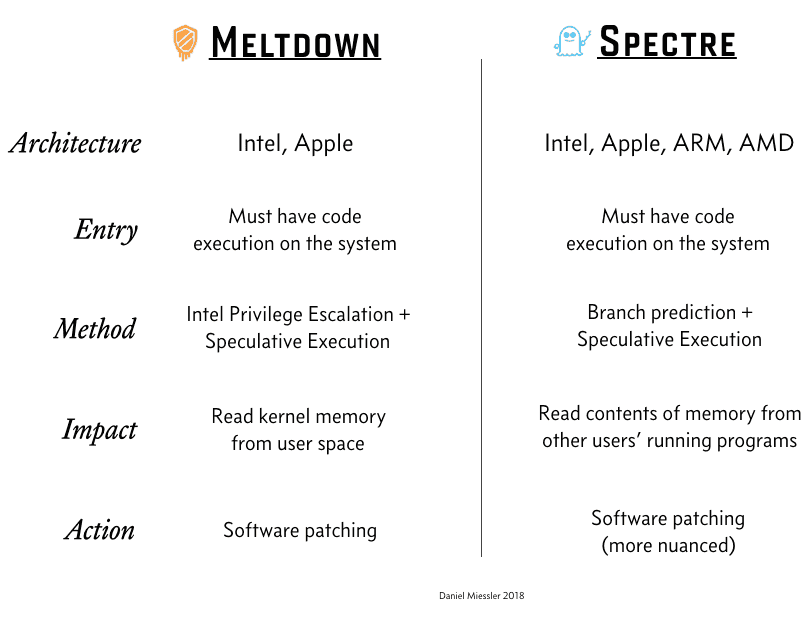
The ARM-based CPU architectures contain the vulnerability that could literally allow attackers to access protected data in the memory during program execution. These protected data include passwords, credit card information, and other sensitive information. Although Meltdown and Spectre are potentially two distinct forms of attack, they all exploit a feature in both older and modern processors known as “speculative execution.” This feature allows CPUs to optimize its performance, hence speed up processes. But what exactly is speculative execution?
Speculative Execution
Understanding Meltdown and Spectre requires a clear understanding of how CPUs execute programs. As mentioned above, a CPU’s performance can be improved through speculatively executing instructions based on the assumption that are considered likely to be true. In case the speculation turns out to be false, then the CPU discards the execution and unwinds it using the correct execution. To put this into perspective, think of your computer as a restaurant a customer comes in every day at 8.00 am and orders the exact same breakfast. Eventually, the cook sees the pattern and starts making the order ahead of time, it’s more efficient, and breakfast is ready when the customer comes in the door. But what if that regular customer decides to order something different now the cook has to throw away the prepared breakfast and start over.
Speculative execution works in a similar way whenever computers perform calculations that aren’t actually needed the results are thrown away. This data ends up in an unsecured part of the computer’s cache memory (usually L2 cache) where unauthorized users can access it through a side channel attacks.
Spectre
While this vulnerability can be used to exploit the interactions in the kernel and the L2 cache memory in all modern ARM-based CPUs, ARM has been claiming that their processors are not affected. However, tests from Google and Microsoft confirms that ARM processors are indeed affected. But why are the chip manufacturers so disquiet? The main reason why Spectre is a serious security concern is that it provides a gateway for hackers to make use of regular applications such as browsers to access the Kernel module of the Operating System. In fact, Spectre can be used to trick the running machine in such a way that it gives up protected memory data from the Kernel to the attacker with the knowledge or consent of the user. To demonstrate this, let’s consider the code below:
Output_value = Input_value + Array[x]
{
Result = Retrieve_data(Output_value);
Return Result;
}
From the above code, speculative execution assumes the value of Result and executes the code while it waits for the actual Output_value to be released from the memory. If the CPU’s assumption was right, then the execution continues. On the other hand, if Output_value turns out to be a different value, then the value of Result that the CPU had initially assumed will be discarded to the cache memory. As you can see, if an attacker wants to know the value of Result from what the CPU speculates, they would simply supply any value to Output_value then proceed to the cache memory via side-channel analysis and fetch the data. A Spectre exploit can easily affect systems that use shared resources such as virtual servers, web servers and many more.
But why is this data left unsecured? Back in the 1960s, when speculative execution was invented computers were very self-contained. Since there was no way to see the data being discarded, nobody thought it was a risk, and it was never secured. Today, computers and mobile devices share system resources with many applications and environments. Typically, sharing is good, but when unprotected data from speculative execution ends up in shared memory, it can become a serious problem. Cyber criminals use a side channel attack to sneak in and hijack the data. Even worse, Spectre tends to break the isolation between different applications allowing even error-free programs that follow best practices to leak their secrets.
Severity of Spectre
As mentioned, Spectre is a hardware-based vulnerability and developing a foolproof patch for the system could be a challenge. However, if an attacker successfully creates its exploit, then the implications might be severe.
Meltdown
This vulnerability is likely to affect only Intel processors. Its target is the differentiating factor between the application memory and the system’s Core Memory. In a typical CPU, there are two layers of memory; the application memory which stores data for applications such as browser data, media player data, etc. The other part is the Core Memory which stores protected system data such as passwords, encryption keys, etc. Therefore, Meltdown allows attackers to use programs to access the protected memory revealing both application and operating system data.
Notice that unlike Spectre which breaks down the isolation between applications, Meltdown is more dangerous because it breaks down the isolation between the operating system and the applications. The term Meltdown means that there is a total meltdown of operating system.
Severity of Meltdown
The severity is high if not mitigated.
Mitigation
The reality is, patching these vulnerabilities can significantly affect the performance of the CPU. So, is there something you can do to prevent your computer, smartphone, or tablet from these vulnerabilities? Yes. For now, make sure that your system is up to date as various vendors are attempting to patch the vulnerabilities. Remember, these vulnerabilities affects all the devices be it smartphones, cloud servers, laptops as well as desktops.
Note that it’s still unclear to whether ARM-based processors slow down the system when executing the patch.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….


