Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Generally, the hidden messages appear to be (or be part of) something else: images, articles, shopping lists, or some other cover text. This post would cover Steganography in Kali Linux – Hiding data in image. You can pretty much use the same method to hide data in Audio or Video files.
 In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. For example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it.
In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. For example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it.
The advantage of steganography over cryptography alone is that the intended secret message does not attract attention to itself as an object of scrutiny. Plainly visible encrypted messages—no matter how unbreakable—arouse interest, and may in themselves be incriminating in countries where encryption is illegal. Thus, whereas cryptography is the practice of protecting the contents of a message alone, steganography is concerned with concealing the fact that a secret message is being sent, as well as concealing the contents of the message.
Steganography in Kali Linux
There’s two primary tools available in Kali Linux for Steganographic use.
a. Steghide
Steghide is a steganography program that is able to hide data in various kinds of image- and audio-files. The color- respectivly sample-frequencies are not changed thus making the embedding resistant against first-order statistical tests.
Features:
- compression of embedded data
- encryption of embedded data
- embedding of a checksum to verify the integrity of the extraced data
- support for JPEG, BMP, WAV and AU files
b. StegoSuite
Stegosuite is a free steganography tool written in Java. With Stegosuite you can hide information in image files.
Features
- BMP, GIF and JPG supported
- AES encryption of embedded data
- Automatic avoidance of homogenous areas (only embed data in noisy areas)
- Embed text messages and multiple files of any type
- Easy to use
Hiding data in image using steghide
Install Steghide
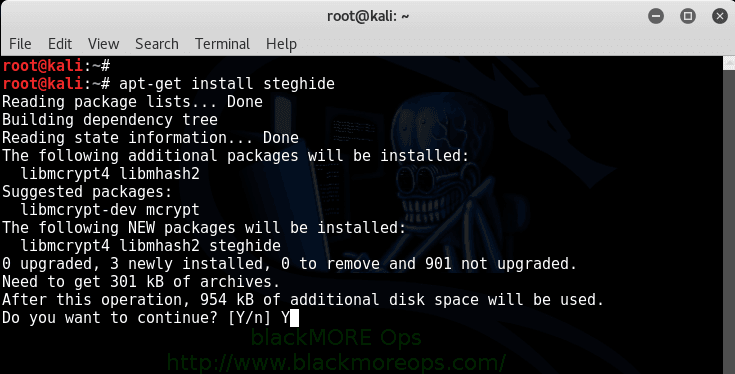
Installation is simple in Kali Linux as steghide is already available in Kali Linux repository. Run the following command and you’re done.
root@kali:~# apt-get install steghide
Hide text file in Image
I created a folder steghide in root home folder and placed picture.jpg and secret.txt file in there. picture.jpg is the file where I am going to hide secret.txt file. I am going to show the commands here.
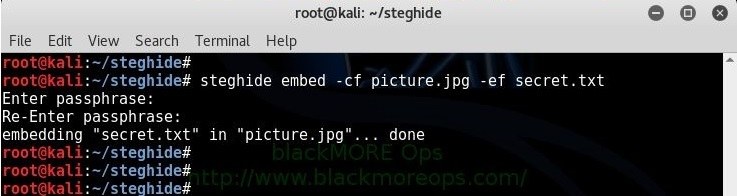
To hide text file in Image in Kali Linux using steghide, use the following command:
root@kali:~/steghide# steghide embed -cf picture.jpg -ef secret.txt Enter passphrase: Re-Enter passphrase: embedding "secret.txt" in "picture.jpg"... done root@kali:~/steghide#
This command will embed the file secret.txt in the cover file picture.jpg.
Now you can email, share or do anything with this new picture.jpg file without having to worry about exposing your data.
Extracting text file from Image
After you have embedded your secret data as shown above you can send the file picture.jpg to the person who should receive the secret message. The receiver has to use steghide in the following way:
root@kali:~/steghide# steghide extract -sf picture.jpg Enter passphrase: the file "secret.txt" does already exist. overwrite ? (y/n) y wrote extracted data to "secret.txt".
If the supplied passphrase is correct, the contents of the original file secret.txt will be extracted from the stego file picture.jpg and saved in the current directory.
Just to be on safe side, I am checking the content of the secret.txt I extracted. Seems ok.
root@kali:~/steghide# head -3 secret.txt Linux. It’s been around since the mid ‘90s, and has since reached a user-base that spans industries and continents. For those in the know, you understand that Linux is actually everywhere. It’s in your phones, in your cars, in your refrigerators, your Roku devices. It runs most of the Internet, the supercomputers making scientific breakthroughs, and the world\'s stock exchanges. But before Linux became the platform to run desktops, servers, and embedded systems across the globe, it was (and still is) one of the most reliable, secure, and worry-free operating systems available. root@kali:~/steghide#
Viewing Info of embedded data
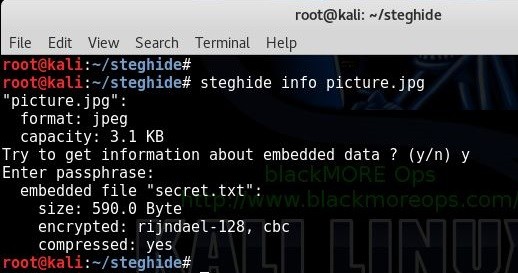
If you have received a file that contains embedded data and you want to get some information about it before extracting it, use the info command:
root@kali:~/steghide# steghide info picture.jpg
"picture.jpg":
format: jpeg
capacity: 3.1 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "secret.txt":
size: 6.5 KB
encrypted: rijndael-128, cbc
compressed: yes
root@kali:~/steghide#
After printing some general information about the stego file (format, capacity) you will be asked if steghide should try to get information about the embedded data. If you answer with yes you have to supply a passphrase.
Steghide will then try to extract the embedded data with that passphrase and – if it succeeds – print some information about it.
If you want more detailed information please read the man(ual) page.
Hiding data in image using Stegosuite
Stegosuite is pretty much a GUI for similar steghide-type functionality.
Install stegosuite
Installation is simple in Kali Linux as stegosuite is already available in Kali Linux repository. Run the following command and you’re done.
root@kali:~# apt-get install stegosuite
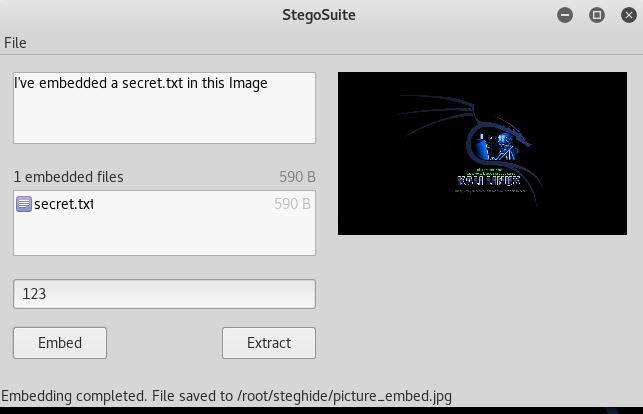
Embed text file in Image using Stegosuite
You need to run it from Application menu (or you can just search it). Go to File > Open and open the image you want to use. Right-click on the file section and select add files and select your secret.txt file. Type in a passphrase and click on embed. Few seconds and it will create a new file picture_embed.jpg.
Extracting text file from Image using Stegosuite
If you want to extract text file or data from the image, simply Open the image, type in the passphrase and click on Extract.
Steganalysis and detection
In computing, steganographically encoded package detection is called steganalysis. The simplest method to detect modified files, however, is to compare them to known originals. For example, to detect information being moved through the graphics on a website, an analyst can maintain known clean-copies of these materials and compare them against the current contents of the site. The differences, assuming the carrier is the same, comprise the payload. In general, using extremely high compression rates makes steganography difficult, but not impossible. Compression errors provide a hiding place for data, but high compression reduces the amount of data available to hold the payload, raising the encoding density, which facilitates easier detection (in extreme cases, even by casual observation).
I found few references that I’ve included here, but I am really not able to find a really good source or tool. Perhaps the readers might suggest more tools and methods.
- Steganalysis: Your X-Ray Vision through Hidden Data
- A few tools to discover hidden data
- Steganography Tools
- An Overview of Steganography for the Computer Forensics Examiner
- Steganography Countermeasures and detection
- Digital Forensic Tools: Imaging, Virtualization, Cryptanalysis, Steganalysis, Data Recovery, Data Carving, Reverse Engineering

I have seen you have posted related linux tools, I have written a article on Top 10 steganography tools for Windows 10
Hi, I have .txt file but I dont know password for decryption…How to make password attack.
Thank you, for your advice