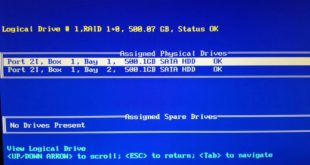
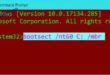
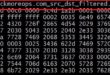
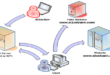
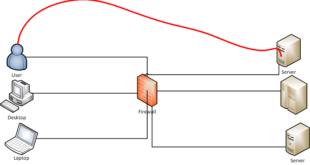
When the HP Proliant DL380 G7 boots up the only displayed BIOS options are F9 …
Read More »-
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never …
Read More » -
Please use the command line updater because updating via browser is disabled in your config.php error on NextCloud
-
Nyxt: Hacker’s Dream Browser
-
Install and Run Citrix Workspace on Linux
-
Change IP address in packet capture file (faking IP)
-
Output your microphone to a remote computers speaker
Output your microphone to a remote computers speaker
Read More » -
SSH through host in the middle
-
Three different ways to duplicate installed packages in multiple machines in Linux
-
ssh to machine behind shared NAT
-
How to check Network Interface details in Linux
-
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
If you’ve encountered an issue where Hashcat initially only recognizes your CPU and not the …
Read More » -
Free Android Penetration Testing Toolkit & Risk Assessment
-
Penetration Testing Tools for Beginners
-
Automatically crack WiFi password with besside-ng
-
124 legal hacking websites to practice and learn
-
Steganography in Kali Linux – Hiding data in image
Steganography is the practice of concealing a file, message, image, or video within another file, …
Read More » -
14 top data recovery softwares – Data rescue tools
-
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never …
Read More » -
Whispers: A Powerful Static Code Analysis Tool for Credential Detection
-
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
-
Migrate Plex Server – Ubuntu
-
Boot Ubuntu Server 22.04 LTS from USB SSD on Raspberry Pi 4
-
Install MATE Desktop in Kali Linux 2.x (Kali Sana)
MATE is a fork of GNOME 2. It provides an intuitive and attractive desktop environment …
Read More » -
Use different wallpapers on multiple monitors in Linux
-
Fixing resolution problem on Linux after locking workstation
-
Conky Manager on Debian and Kali Linux
-
Install Cairo-Dock in Kali Linux
-
How to create a Bot Net legally? Put that in your ToS, that’s how!
This is a #rant post, TL'DR. In summary, you can just create a Chrome, Firefox, iOS, Android extension/plugin/app for free, let it grow bigger overtime and then just sell idle users bandwidth to Bot Net for profit. And you just put that somewhere in your looong ToS that everyone just presses "I Agree, get it over with and let me use the service already".
Read More » -
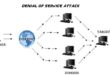
DoS website in Kali Linux using GoldenEye
-
Denial-of-service Attack – DoS using hping3 with spoofed IP in Kali Linux
-
World Live DDoS attack maps – Live DDoS Monitoring
-
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never …
Read More » -
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
-
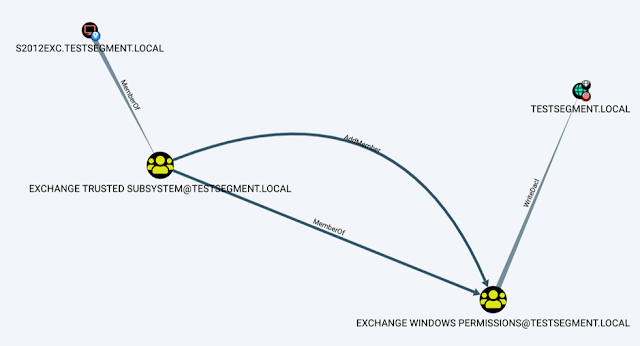
Exploit ACL Based Privilege Escalation Paths in Active Directory
-
How to check Network Interface details in Linux
-
Can’t connect to WiFi in Linux
-
Free Android Penetration Testing Toolkit & Risk Assessment
Free Android Penetration Testing Toolkit & Risk Assessment
Read More » -
Penetration Testing Tools for Beginners
-
Detect SQL Injection (SQLi) and XSS
-
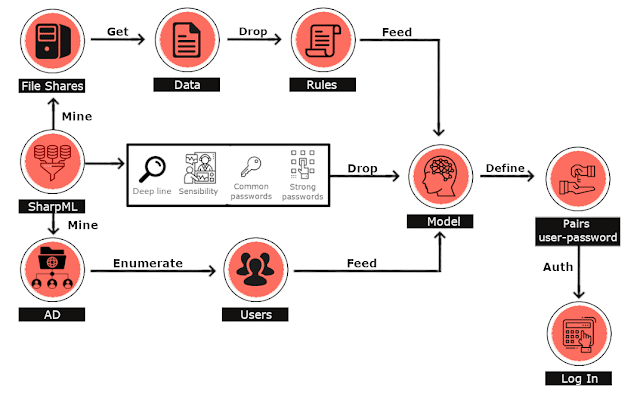
Machine Learning Network Share Password Hunting Toolkit
-
Vulnerable docker environment for learning to hack
-
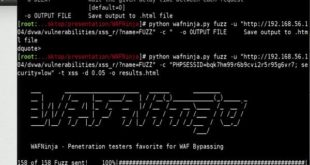
Bypass Web Application Firewall using WAFNinja
WAFNinja is a CLI python tool that helps penetration testers to bypass Web Application Firewall …
Read More » -
dns2proxy – Offensive DNS server post-explotation tool – DNS spoofing, phishing and pharming
-
Free DoS Attack Tools
-
DoS website using slowhttptest in Kali Linux – slowloris, slow HTTP POST and slow Read attack in one tool
-
How to create a Bot Net legally? Put that in your ToS, that’s how!
-
Ubiquiti Dream Machine (UDM) – unable to connect to NBN
I don’t want the NBN ISP router running anymore and use Ubiquiti Dream Machine (UDM) …
Read More » -
tor-rootkit – A Python 3 standalone Windows 10 and Linux Rootkit
-
Accessing ESXi console screen from an SSH session
-
Setting up Damn Vulnerable Web Application (DVWA) – Pentesting Lab
-
Communicate via an WEP-encrypted access point with easside-ng
-
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
If you’ve encountered an issue where Hashcat initially only recognizes your CPU and not the …
Read More » -
Failed to open directory on Kali Linux Virtualbox
-
Can’t connect to WiFi in Linux
-
Setting up Damn Vulnerable Web Application (DVWA) – Pentesting Lab
-
124 legal hacking websites to practice and learn
-
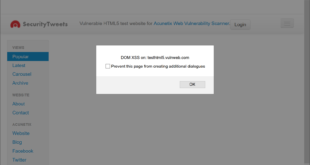
How to Prevent DOM-based Cross-site Scripting
There’s no denying the role that JavaScript has played in making web applications the sleek, …
Read More » -
124 legal hacking websites to practice and learn
-
Check Point SandBlast protected users from a Zero-Day Microsoft Office Vulnerability
-
What are the Challenges of Using Open Source Cybersecurity Tools?
-
SSL Decryption Series: The Security Impact of HTTPS Interception
-
Free Android Penetration Testing Toolkit & Risk Assessment
Free Android Penetration Testing Toolkit & Risk Assessment
Read More » -
124 legal hacking websites to practice and learn
-
Automated Penetration Testing with APT2 Toolkit
-
Publicly Available Tools Seen in Cyber Incidents Worldwide
-
Kali Linux 2018.2 released
-
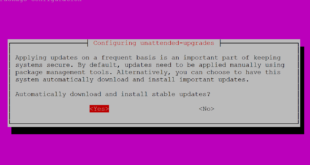
How to configure automatic updates in Ubuntu Server
This guide explains how to configure automatic updates in Ubuntu Server 20.04. This tutorial is …
Read More » -
How to check Network Interface details in Linux
-
A .vimrc config file everyone should use
-
Remove cloud-init from Ubuntu
-
Find exact installation date of Linux
-
Nyxt: Hacker’s Dream Browser
In the ever-evolving digital landscape, the demand for specialized tools and platforms has grown exponentially. …
Read More » -
SamSam Ransomware
-
New Exploits for Unsecure SAP Systems
-
Microsoft Operating Systems BlueKeep Vulnerability
-
How to Prevent DOM-based Cross-site Scripting
-
Introducing Kali Linux NetHunter and NetHunter supported devices
Featured: The Kali Linux NetHunter project is the first Open Source Android penetration testing platform …
Read More »
-
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never …
Read More » -
Enabling AMD GPU for Hashcat on Kali Linux: A Quick Guide
-
Migrate Plex Server – Ubuntu
-
Boot Ubuntu Server 22.04 LTS from USB SSD on Raspberry Pi 4
-
Quick Snap Cheat Sheet for Ubuntu
-
Kali Linux 1.0.7 kernel 3.14 install NVIDIA driver kernel Module CUDA and Pyrit – CUDA, Pyrit and Cpyrit-cuda
In this guide, I will show how to install NVIDIA driver kernel Module CUDA, replace …
Read More » -
Install NVIDIA driver kernel Module CUDA and Pyrit on Kali Linux – CUDA, Pyrit and Cpyrit-cuda
-
20 things to do after installing Kali Linux 1.x
-
How to install Pyrit in Kali Linux?
-
How to install CAL++ in Kali Linux?
-
Output your microphone to a remote computers speaker
Output your microphone to a remote computers speaker
Read More » -
Advanced Persistent Threat Activity Exploiting Managed Service Providers
-
Setting Up A Free TLS/SSL Certificate With “Let’s Encrypt”
-
Mass delete files in FTP server
-
Top 30 SSH shenanigans
-
Kali Linux 2018.2 released
This Kali release is the first to include the Linux 4.15 kernel, which includes the …
Read More » -
Cracking Wifi WPA/WPA2 passwords using Reaver-WPS
-
Complete WSL AI Development Environment Guide: CUDA, Ollama, Docker & Stable Diffusion Setup
Setting up a powerful AI development environment in Windows Subsystem for Linux (WSL) has never …
Read More » -
Whispers: A Powerful Static Code Analysis Tool for Credential Detection
-
Identifying harmful activity on your captured traffic
-
Boot Ubuntu Server 22.04 LTS from USB SSD on Raspberry Pi 4
-
HELK – An Open Source Threat Hunting Platform
-
Use any Linux applications through a proxy (apt-get, wget etc)
It's pretty normal in many Organizations to use get servers to connect to Internet via a Proxy. In most cases it's for updating apt-get or yum via proxy. However, quite often you might need to download packages directly using wget or curl and setting up apt-get or apt via proxy, wget via proxy, curl via proxy is a pain. What if you could simply setup a Proxy and just use any applications to use that using a simply command? I faced this many times and hence writing this guide. Note that if you're only allowing apt-get via proxy then stick with configuring /etc/apt.conf or /etc/apt/conf.d/00proxy or something similar but if you need to allow different applications via a proxy then this method is best and simplest.
Read More » -
Fixing ProxyChains ERROR: ld.so: object ‘libproxychains.so.3’ from LD_PRELOAD cannot be preloaded: ignored.
-
Identify website technologies with WhatWeb
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb …
Read More » -
Setting up Damn Vulnerable Web Application (DVWA) – Pentesting Lab
-
SecLists – Security Tester’s Companion
-
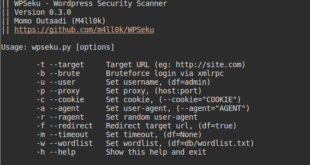
WPSeku – WordPress Security Scanner
-
Hacking QNX systems over QCONN
-
WPSeku – WordPress Security Scanner
WPSeku is a black box WordPress vulnerability scanner that can be used to scan remote …
Read More » -
WPSCAN and quick wordpress security – Fixing Direcroty Listing – Part 2
-
WPSCAN and quick wordpress security
-
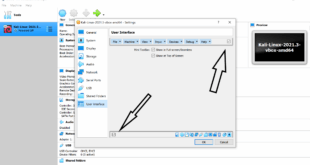
How to unhide menu bar in Virtualbox
So I went in and hid the top menu bar and bottom status bar in Virtualbox. After they disappeared, now I cannot find out how to unhide those. Took me a little bit time to figure out, hence this post so that I don't forget it and someone else having the same to unhide menu bar in Virtualbox can find this.
Read More » -
Failed to open directory on Kali Linux Virtualbox
-
Kali Linux 2018.2 released
-
Troubleshooting Wireless Drivers in Kali Linux
-
How to install VirtualBox Guest Additions in Kali Linux (Kali Rolling / Kali Linux 2016.2 / Kali 2017)
-
Advanced Persistent Threat Activity Exploiting Managed Service Providers
Organizations should configure system logs to detect incidents and to identify the type and scope …
Read More » -
Advantages disadvantages of using Proxy vs VPN vs TOR vs TOR and VPN together.
-
Complete solution for online privacy with own private OpenSSH, OpenVPN and VNC server
-
Free VPN providers of 2015
-
A very detailed guide on how to setup VPN on Kali Linux and Ubuntu
-
Inceptor – Template-Driven AV/EDR Evasion Framework
Modern Penetration testing and Red Teaming often requires to bypass common AV/EDR appliances in order to execute code on a target. With time, defenses are becoming more complex and inherently more difficult to bypass consistently. Inceptor is a tool which can help to automate great part of this process, hopefully requiring no further effort.
Read More » -
PuTTY alternatives
-
Android Banking Trojan Virus code leaks and sparks copycats immediately
-
Top 30 SSH shenanigans
-
Building updated Kali Linux ISO
-
Boot Ubuntu Server 22.04 LTS from USB SSD on Raspberry Pi 4
This is a guide for configuring Raspberry Pi4 to boot Ubuntu from external USB SSD …
Read More » -
Install and Run Citrix Workspace on Linux
-
Use Diskpart to create, delete, clean or extend disk partitions in Windows
-
Can’t connect to WiFi in Linux
-
PuTTY alternatives
-
Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs
This Joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, …
Read More » -
Emotet Malware – one of the most destructive malware right now
-
Using Rigorous Credential Control to Mitigate Trusted Network Exploitation
-
Catching bad guys
-
telus.com spam emails to gmail account
-
Can’t connect to WiFi in Linux
So I installed the latest version of Kali Linux from USB into my RAZER Blade …
Read More » -
Cyber Actors Target Home and Office Routers and Networked Devices Worldwide
-
Automatically crack WiFi password with besside-ng
-
Forging ARP, UDP, ICMP or custom packets with packetforge-ng
-
Crack a WEP key of an open network without user intervention with Wesside-ng
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….