How many Linux vulnerabilities and exploits were exposed since last 6 months? Many! With recent Shellshock, Heartbleed, Poodle, Ghost and maybe many more to come. Suddenly, I didn’t feel that much secure anymore with my Linux as it’s the core packages that are affected.. What’s next? My openVPN is not secured anymore? My SSH session keys are vulnerable? I decided to do a Linux security audit of my Linux system. After setting up an external firewall, I suddenly realized, it’s just too big for me to do it manually. That’s when I found Lynis. Lynis is an open source security auditing tool. It was reasonably well documented and did many things quickly that could’ve took me ages.
For this whole test, I used Lynis free version.
How Linux security audit works?
Lynis will perform hundreds of individual tests to determine the security state of the system. Many of these tests are also part of common security guidelines and standards. Examples include searching for installed software and determine possible configuration flaws. Lynis goes further and does also test individual software components, checks related configuration files and measures performance. After these tests, a scan report will be displayed with all discovered findings.
Typical use cases for Lynis:
- Security auditing
- Vulnerability scanning
- System hardening
Installation
You can install Lynis from repository (i.e. using yum or apt-get) but I found that it’s not the most up-to-date version of Lynis. You’re better off downloading it to a local directory and running it from there.
Lynis with Installation – package
Although no installation is needed, a common method to use Lynis is installing it via a package. This could be with the repositories provided by the operating system, or a manually created package. Please note that some repositories go for stability and don’t update software after the release, with exception of security updates. This might result in using a very old version of Lynis and is usually not preferred. So before using a package, confirm that updates are provided.
Red Hat based: $ sudo yum install lynis Debian based: $ sudo apt-get install lynis
But, please don’t use that. It’s useless running an old package! Isn’t that the whole reason your run a security audit?
Lynis without installation – local
This is the way to go as you get the most updated package.
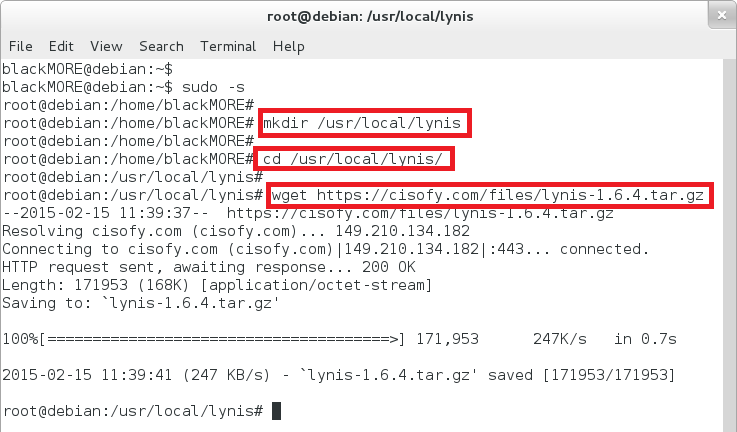
Create a directory (ie. /usr/local/lynis)
Lynis can be started from each directory (or from removable media).
blackMORE@debian:~$ sudo -s root@debian:/home/blackMORE# root@debian:/home/blackMORE# mkdir /usr/local/lynis root@debian:/home/blackMORE# root@debian:/home/blackMORE# cd /usr/local/lynis/ root@debian:/usr/local/lynis#
Download Lynis tarball
Go to the Downloads section and copy the link to the Lynis tarball (current version is lynis-1.6.4.tar.gz). Use this link together with wget (usually installed by default). Mac OS users can use curl tool, where BSD users could use fetch.
root@debian:/usr/local/lynis# wget https://cisofy.com/files/lynis-1.6.4.tar.gz --2015-02-15 11:39:37-- https://cisofy.com/files/lynis-1.6.4.tar.gz Resolving cisofy.com (cisofy.com)... 149.210.134.182 Connecting to cisofy.com (cisofy.com)|149.210.134.182|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 171953 (168K) [application/octet-stream] Saving to: `lynis-1.6.4.tar.gz' 100%[======================================>] 171,953 247K/s in 0.7s 2015-02-15 11:39:41 (247 KB/s) - `lynis-1.6.4.tar.gz' saved [171953/171953] root@debian:/usr/local/lynis# sha256sum lynis-1.6.4.tar.gz 886c74b591706f896149fe74adb481b58c549d32243d0cf620b46dfdd25dc66d lynis-1.6.4.tar.gz root@debian:/usr/local/lynis#
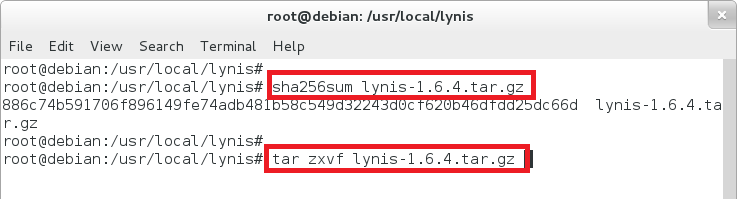
After downloading, test the file to confirm the integrity of the download. The related SHA1, SHA256 hash is provided on the website as well. Depending on your OS, this can be performed with the command sha1, sha1sum, sha256sum or with openssl.
root@debian:/usr/local/lynis# sha1sum lynis-1.6.4.tar.gz root@debian:/usr/local/lynis# sha1 lynis-1.6.4.tar.gz root@debian:/usr/local/lynis# openssl sha1 lynis-1.6.4.tar.gz
The resulting hash displayed should be the same as on the website. If not, try downloading it on another machine or via a browser, to confirm the download was not corrupted.
Unpack the tarball
Now unpack the tarball and change into Lynis directory.
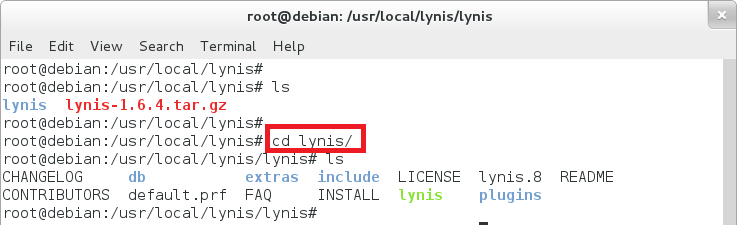
root@debian:/usr/local/lynis# tar zxvf lynis-1.6.4.tar.gz root@debian:/usr/local/lynis# cd lynis/
Lynis help menu
Lynis comes with it’s own help menu that shows some basic options and to-do.
root@debian:/usr/local/lynis/lynis# ./lynis --help
[ Lynis 1.6.4 ]
################################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
Copyright 2007-2014 - CISOfy & Michael Boelen, http://cisofy.com
Enterprise support and plugins available via CISOfy - http://cisofy.com
################################################################################
[+] Initializing program
------------------------------------
Scan options:
--auditor "<name>" : Auditor name
--check-all (-c) : Check system
--no-log : Don't create a log file
--pentest : Non-privileged scan (useful for pentest)
--profile <profile> : Scan the system with the given profile file
--quick (-Q) : Quick mode, don't wait for user input
--tests "<tests>" : Run only tests defined by <tests>
--tests-category "<category>" : Run only tests defined by <category>
Layout options:
--no-colors : Don't use colors in output
--quiet (-q) : No output, except warnings
--reverse-colors : Optimize color display for light backgrounds
Misc options:
--check-update : Check for updates
--debug : Debug logging to screen
--view-manpage (--man) : View man page
--version (-V) : Display version number and quit
Enterprise options:
--plugin-dir "<path>" : Define path of available plugins
--upload : Upload data to central node
See man page and documentation for all available options.
Exiting..
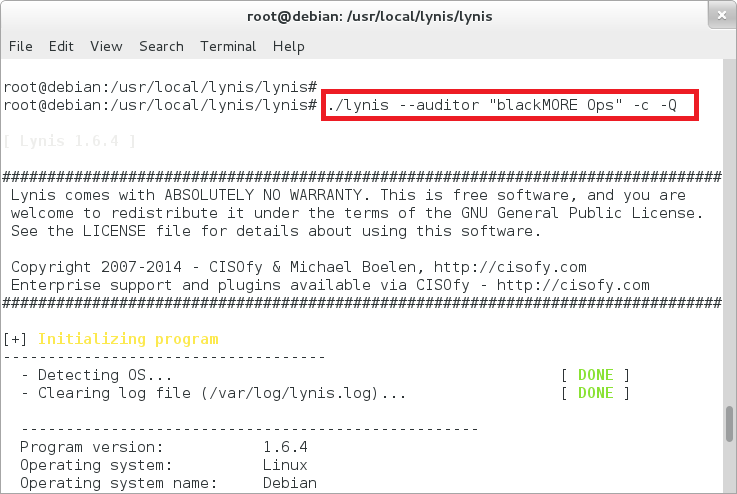
Running Lynis
I did a quick test of my Debian server using Lynis.
root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -Q
[ Lynis 1.6.4 ]
################################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
Copyright 2007-2014 - CISOfy & Michael Boelen, http://cisofy.com
Enterprise support and plugins available via CISOfy - http://cisofy.com
################################################################################
[+] Initializing program
------------------------------------
- Detecting OS... [ DONE ]
- Clearing log file (/var/log/lynis.log)... [ DONE ]
---------------------------------------------------
Program version: 1.6.4
Operating system: Linux
Operating system name: Debian
Operating system version: 7.8
Kernel version: 3.2.0
Hardware platform: x86_64
Hostname: debian
Auditor: blackMORE Ops
Profile: ./default.prf
Log file: /var/log/lynis.log
Report file: /var/log/lynis-report.dat
Report version: 1.0
Plugin directory: ./plugins
---------------------------------------------------
- Checking profile file (./default.prf)...
- Program update status... [ NO UPDATE ]
[+] System Tools
------------------------------------
- Scanning available tools...
- Checking system binaries...
- /bin [ FOUND ]
- /sbin [ FOUND ]
<--snip-->
It pretty much stopped doing anything my Debian server while checking PHP:
[+] Software: PHP
------------------------------------
- Checking PHP [ NOT FOUND ]
- Checking PHP disabled functions [ NONE ]
-------------->>>No more activity for a long period<<<---------------------
I found that the fix was simple, I just had to edit include/tests_php file to include my php.ini file location.
root@debian:/usr/local/lynis/lynis# vi include/tests_php
Added /etc/php5/fpm/php.ini \ before the last PHPINILOCS line:
#
InsertSection "Software: PHP"
# Possible locations of php.ini
PHPINILOCS="/etc/php.ini \
/etc/php/cgi-php5/php.ini /etc/php/cli-php5/php.ini /etc/php/apache2-php5/php.ini \
/etc/php/apache2-php5.4/php.ini /etc/php/apache2-php5.5/php.ini \
/etc/php5/cgi/php.ini \
/etc/php5/cli/php.ini \
/etc/php5/cli-php5.4/php.ini /etc/php5/cli-php5.5/php.ini /etc/php5/cli-php5.6/php.ini \
/etc/php5/apache2/php.ini \
/private/etc/php.ini \
/var/www/conf/php.ini \
/etc/php5/fpm/php.ini \
/usr/local/etc/php.ini /usr/local/lib/php.ini"
PHPINIDIRS="/etc/php5/conf.d"
#
Now saved and rerun Lynis and it went smoothly:
[+] Software: PHP
------------------------------------
- Checking PHP [ FOUND ]
- Checking PHP disabled functions [ FOUND ]
- Checking register_globals option [ OK ]
- Checking expose_php option [ ON ]
- Checking enable_dl option [ OFF ]
- Checking allow_url_fopen option [ ON ]
- Checking allow_url_include option [ OFF ]
You can run few variations of the command
root@debian:/usr/local/lynis/lynis# ./lynis -c (or) root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -Q (or) root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -Q -q (or) root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -q -Q --pentest (or similar)
Reviewing Lynis report
Lynis saves it’s report in /var/log/lynis.log.Quick Lynis scan shows the following:
root@debian:/usr/local/lynis/lynis# root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -Q -q - Checking for password protection [ WARNING ] - Shellshock: CVE-2014-6277 (segfault, lcamtuf bug #1) [ WARNING ] - Checking vulnerable packages [ WARNING ] - Checking for a running NTP daemon or client [ WARNING ] root@debian:/usr/local/lynis/lynis#
Now I look into /var/log/lynis.log to find more info.
First of all, that password protection… /var/log/lynis.log reveals more info
[12:35:10] Performing test ID BOOT-5122 (Check for GRUB boot password) [12:35:10] Found file /boot/grub/grub.cfg, proceeding with tests. [12:35:10] Test: testing if we can access /boot/grub/grub.cfg [12:35:10] Result: file is owned by our current user ID (0), checking if it is readable [12:35:10] Result: file /boot/grub/grub.cfg is readable (or directory accessible). [12:35:10] Result: Didn't find MD5/SHA1 hashed password line in GRUB boot file! [12:35:10] Risk: user can switch to single user mode by editing current menu items or bypassing them. [12:35:10] Additional information: Do NOT use a plaintext password, since the grub.conf or menu.lst file is most likely to be world readable! [12:35:10] If an unsecured OS like DOS is used, add 'lock' below that entry and setup a password with the password option, to prevent direct system access. [12:35:10] Suggestion: Set a password on GRUB bootloader to prevent altering boot configuration (e.g. boot in single user mode without password) [BOOT-5122] [12:35:10] Tip: Run grub-crypt or grub-md5-crypt and create a hashed password. Add a line below the line timeout=<value>, add: password --md5 <password hash> or password --encrypted <password hash> for SHA1 encrypted password [12:35:10] Hardening: assigned 0 hardening points (max for this item: 2), current: 0, total: 2
So, all it’s saying that my system can be rebooted into single user mode and someone can bypass my security. It also gives you some suggestions on what to do.
Shellshock issue? Let’s check that one in /var/log/lynis.log.
[12:35:11] Test: Check for first exploit (CVE-2014-6277) [12:35:11] Output: vulnerable [12:35:11] Result: Vulnerable to original shellshock (CVE-2014-6277). This may not be a security risk, as distributions patched it. Still it shows your bash is vulnerable for crashing.
ohh that’s bad.. that’s really bad.
Next it was complaining about vulnerable packages. /var/log/lynis.log says that I need to do an update of my system.
[12:35:19] Warning: Found one or more vulnerable packages. [PKGS-7392] [12:35:19] Suggestion: Update your system with apt-get update, apt-get upgrade, apt-get dist-upgrade and/or unattended-upgrades [PKGS-7392
And then the NTP issue
[12:35:21] Result: no ntpdate or rdate found in cron directories [12:35:21] Test: checking for file /etc/network/if-up.d/ntpdate [12:35:21] Result: file /etc/network/if-up.d/ntpdate does not exist [12:35:21] Result: Could not find a NTP daemon or client [12:35:21] Suggestion: Use NTP daemon or NTP client to prevent time issues. [TIME-3104] [12:35:21] Hardening: assigned 0 hardening points (max for this item: 2), current: 68, total: 103
I fixed Shellshock and vulnerable package issue with a simple command as outlined in the logs.
root@kali:/# apt-get update, apt-get upgrade, apt-get dist-upgrade
For NTP, I installed ntpdate package
root@debian:/usr/local/lynis/lynis# apt-get install ntpdate
So my final audit looks like this:
root@debian:/usr/local/lynis/lynis# ./lynis --auditor "blackMORE Ops" -c -Q -q - Checking for password protection [ WARNING ] - Shellshock: CVE-2014-6277 (segfault, lcamtuf bug #1) [ WARNING ]
But remember that explanation from /var/log/lynis.log
[12:35:11] Result: Vulnerable to original shellshock (CVE-2014-6277). This may not be a security risk, as distributions patched it. Still it shows your bash is vulnerable for crashing.
So, it’s not really a security risk for me… What about you?
The Good
Followings are what I found good about Lynis (Open Source version)
- For a free tool, Lynis provides some good tests.
- Reports are easy to understand.
- It uses GPLv3 – thank you.
- Users can write own plugins to use with it.
- I could modify the config file pretty easy to fix that PHP issue.
You can have many other good usages out of Lynis, but every user/corporation have different requirements.
Possible improvements
Followings are what I think should be included in next upgrade:
- A proper HTML report (with collapsible sections). – For me this is a MUST (well, actually for my exec’s who likes pretty reports).
- Filesystem and package integrity tests.
- Include links to CVE articles – very helpful with a HTML report.
- High Level Overview for upper management.
- SQLi tests and suggestions for Database servers.
- More on plausible solutions/suggestions.
- Skip tests when config/include files doesn’t have the correct path.
Conclusion
All in all, I think it’s a good tool to have just for the fact it automates many tests. There’s always room for improvements and Lynis is no different. Any server, be that Linux, Windows or Unix requires scheduled security Audit. While there is no escaping a zero day attack, but with regular audit, you can save your valuable resources. Lynis is a good tool, but you should be using more than one tool just for the fact that different providers (or software developers) have different view on security. As for you, your view should be a secured server with high uptime and data security.
Few words from Michael Boelen, Author of Lynis who sent me an email back in September 10, 2014 at 8:41 pm, one of the first email I received by my Feedback section:
This tool is the result of 7 years of development and much feedback by the community. Now it supported by the original author and his company, development is active and regular updates are being released. The author also stated Lynis would remain free and open source. His way of giving back to the community and make sure nice tools do not get behind a paywall.
Tool: Lynis
Project page: http://cisofy.com/lynis/
Usage: Free
License: GPLv3Download [link to http://cisofy.com/downloads/]

[05:30:38] Performing test ID SHLL-6290 (Perform Shellshock vulnerability tests)
[05:30:38] Test: Check if bash is in the list of shells.
[05:30:38] Test: checking for bash shell in /etc/shells
[05:30:38] Result: command revealed /bin/bash as output
[05:30:38] Result: found /bin/bash as a valid shell
[05:30:38] Test: Check for first exploit (CVE-2014-6271)
[05:30:38] Result: Not vulnerable to original shellshock (CVE-2014-6271)
[05:30:38] Test: Check for first exploit (CVE-2014-6277)
[05:30:38] Result: Not vulnerable to original shellshock (CVE-2014-6277)
[05:30:38] Test: Check for CVE-2014-6278
[05:30:38] Result: Not vulnerable to CVE-2014-6278
[05:30:38] Test: Check for taviso bug CVE-2014-7169
[05:30:38] Result: Not vulnerable to taviso bug (CVE-2014-7169)
[05:30:38] Test: Check for CVE-2014-7186
[05:30:38] Result: Not vulnerable to CVE-2014-7186
[05:30:38] Test: Check for CVE-2014-7187
[05:30:38] Result: Not vulnerable to CVE-2014-7187
[05:30:38] Test: Check for bug Exploit #3 – shellshocker.net (no CVE)
[05:30:38] Result: Not vulnerable to exploit #3 on shellshocker.net (no CVE)
[05:30:38] Hardening: assigned 5 hardening points (max for this item: 5), current: 17, total: 28
I am using gentoo. I’ve got app-shells/bash-4.2_p53 installed.
Thanks for covering Lynis and also providing feedback. The PHP issue has been fixed, as it was simply missing a check to determine if the PHP file was set (and actually found). Thanks for catching that one!
1. A proper HTML report (with collapsible sections). –> That’s our Enterprise version.
2. Filesystem and package integrity tests. –> Covered in Enterprise
3. Include links to CVE articles – very helpful with a HTML report. –> Part of our Enterprise version
4. High Level Overview for upper management. –> Part of our Enterprise version
5. SQLi tests and suggestions for Database servers. –> Definitely getting attention in future updates
6. More on plausible solutions/suggestions. –> We are working on that
7. Skip tests when config/include files doesn’t have the correct path. –> PHP test fixed for upcoming release
For everyone using Lynis on a regular basis, we love to hear your feedback. When you have the budget, consider the upgrade. It helps with the open source development, creation of new features and makes sure the client gets regularly updated, so the community can benefit as well.
Hi Mike,
My pleasure. I didn’t just wanted to do a review like you’ve suggested but actually wanted to use the product and provide some feedback where applicable. Looks like Enterprise is the way to go for large organizations.
Lynis is a fantastic product and yes, I would definitely suggest users to upgrade if there’s a requirement for it. HTML/PDF report is something any ICT Manager would love to see and present to their CTO.
Cheers,
– blackMORE Ops.