Grype is a vulnerability scanner for container images and filesystems with an easy to install binary that supports the packages for most major *nix based operating systems.

Features of Grype Vulnerability Scanner For Container Images & Filesystems
Scan the contents of a container image or filesystem to find known vulnerabilities and find vulnerabilities for major operating system packages in:
- Alpine
- BusyBox
- CentOS / Red Hat
- Debian
- Ubuntu
Find vulnerabilities for language-specific packages:
- Ruby (Bundler)
- Java (JARs, etc)
- JavaScript (NPM/Yarn)
- Python (Egg/Wheel)
- Python pip/requirements.txt/setup.py listings
Supports Docker and OCI image formats.
Installation
Recommended
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/bin
…or, you can specify a release version and destination directory for the installation:
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b
Homebrew
brew tap anchore/grype brew install grype
Note: Currently, Grype is built only for macOS and Linux.
Using Grype Vulnerability Scanner For Container Images & Filesystems
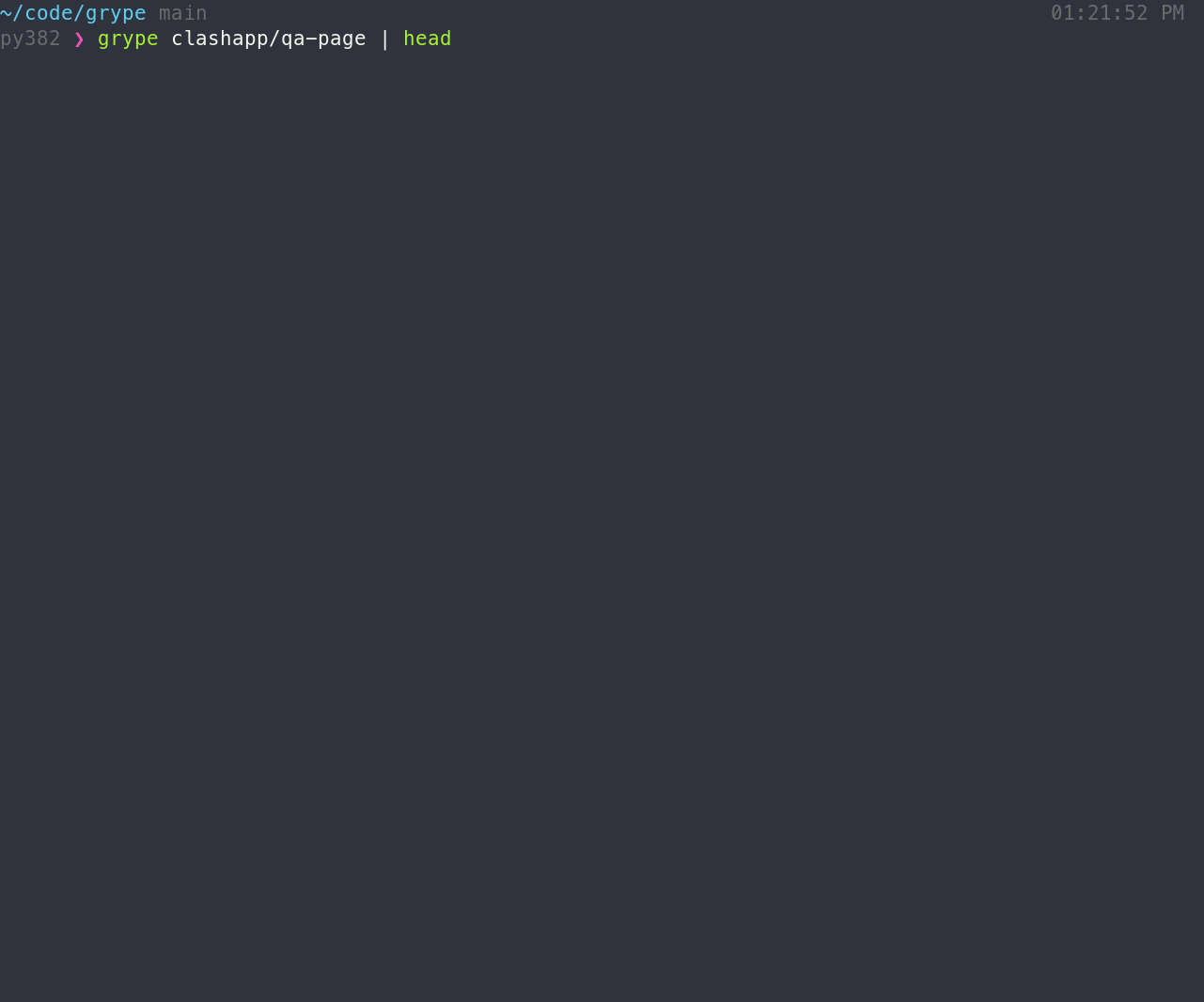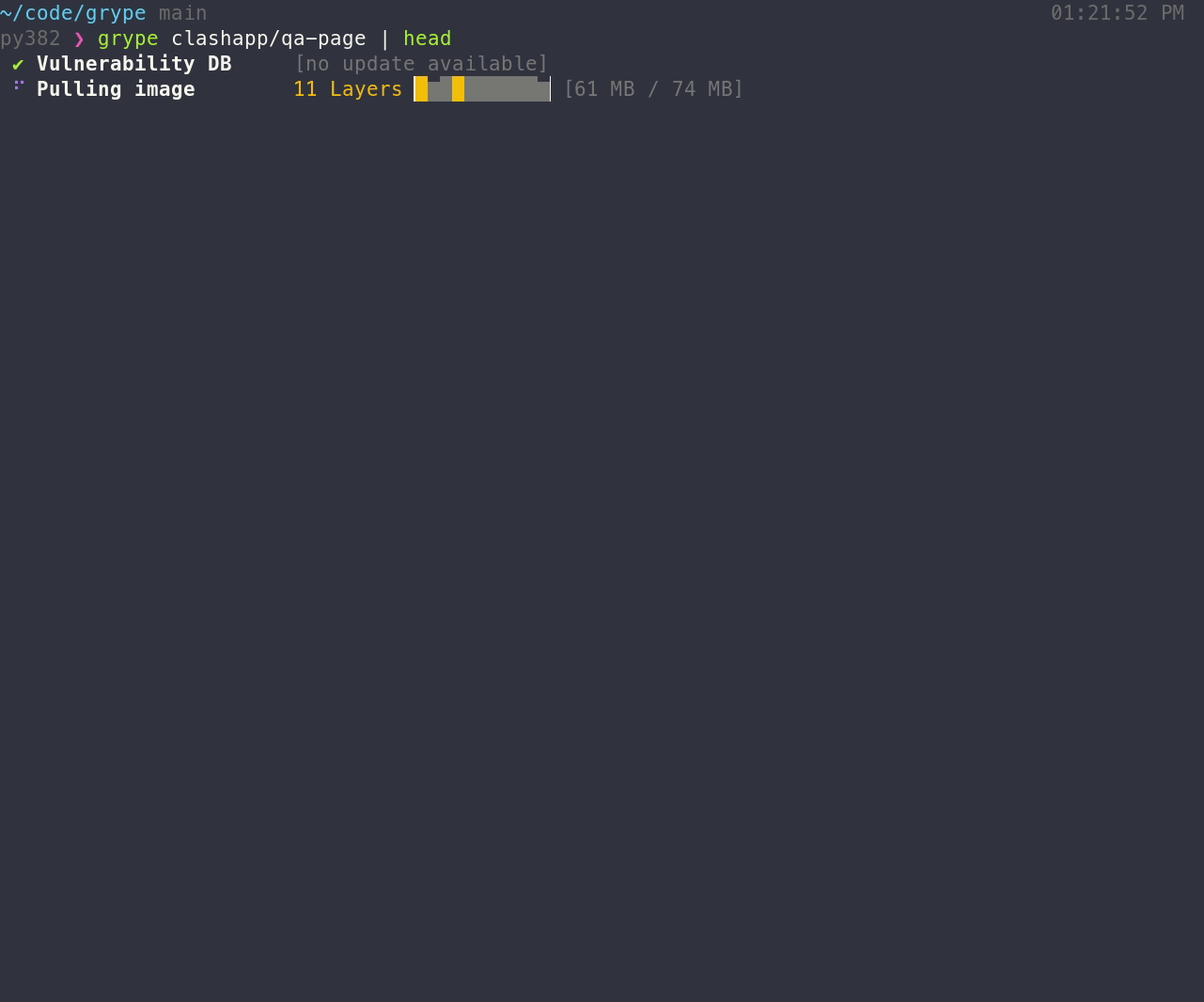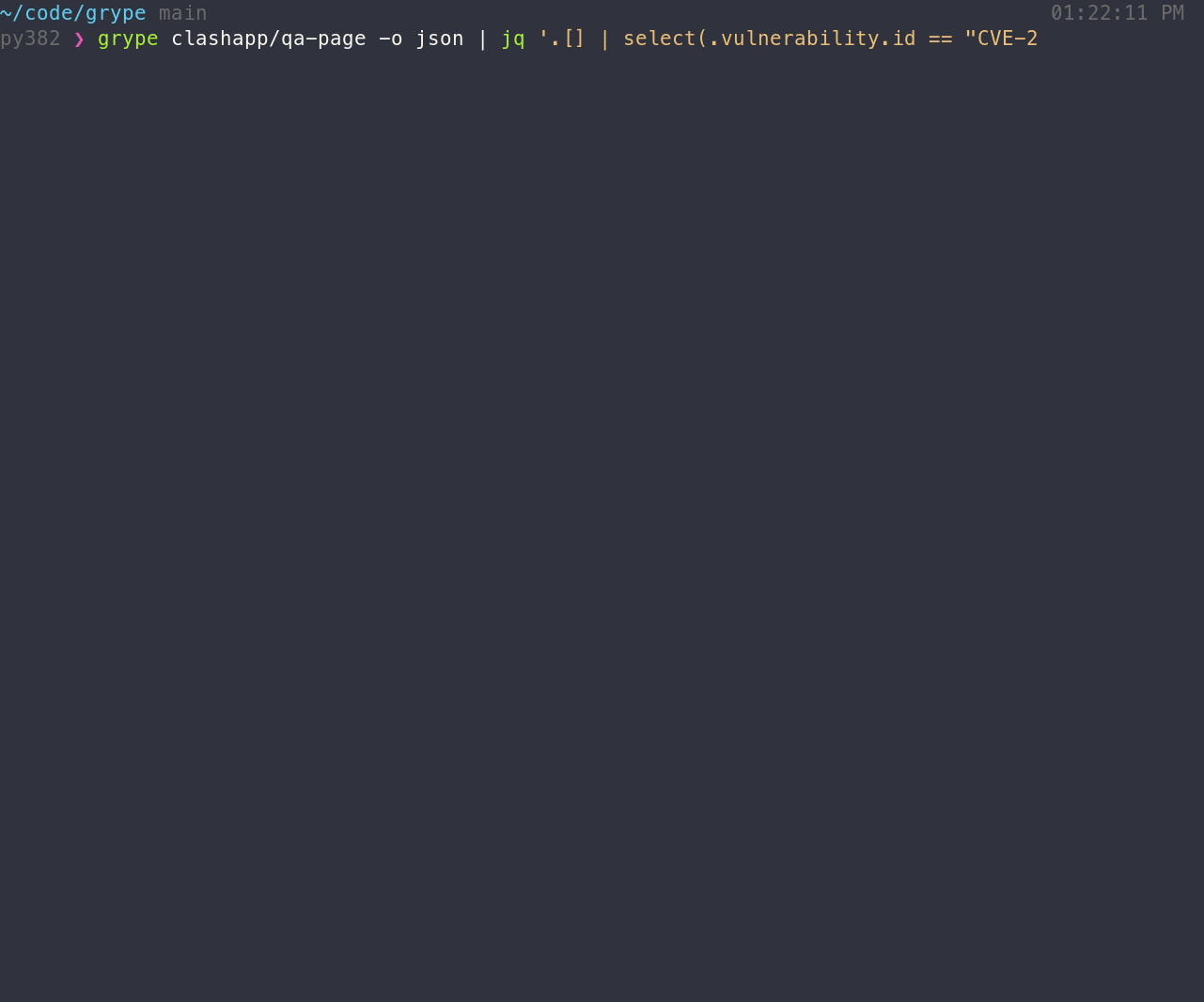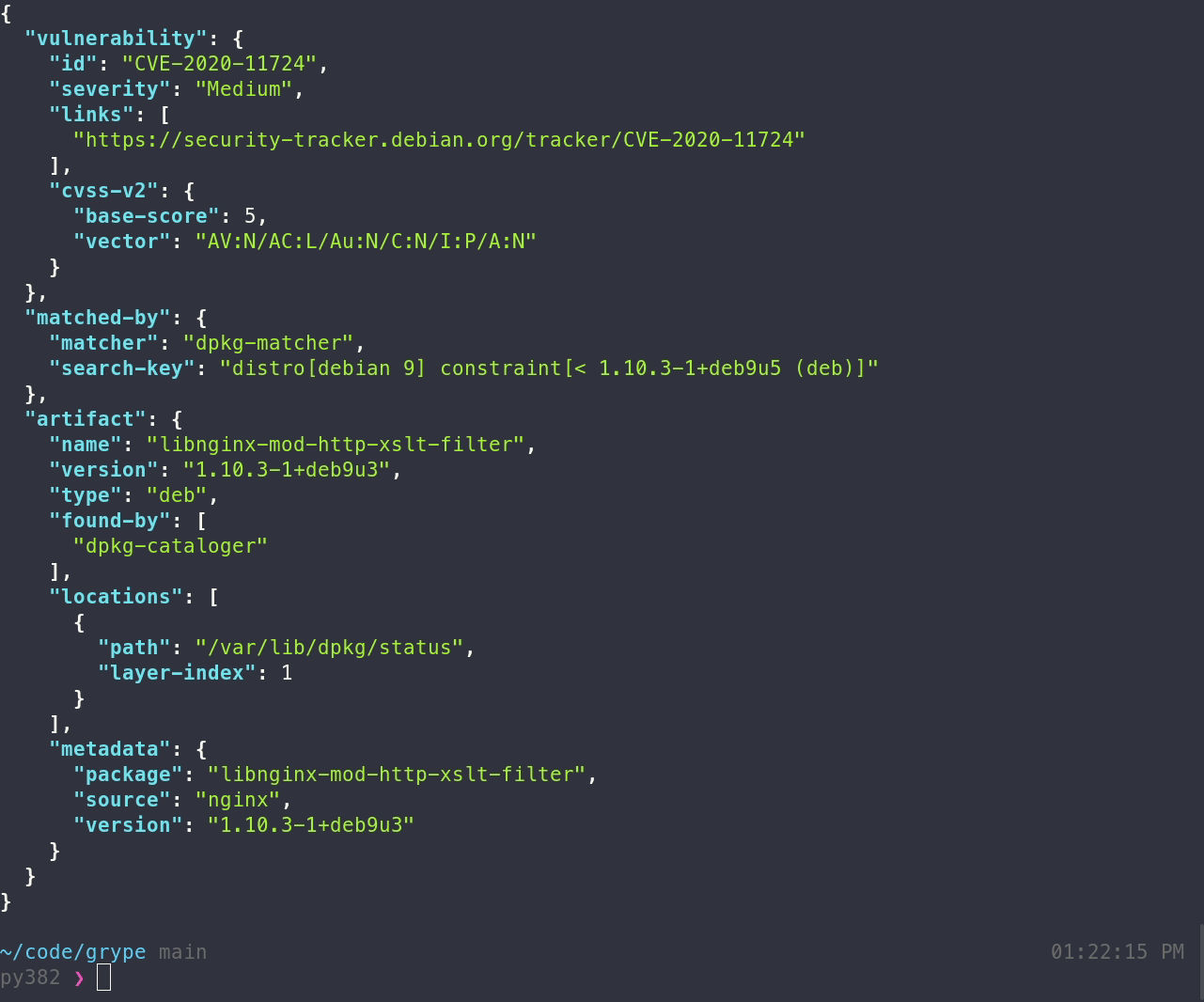
Install the binary, and make sure that grype is available in your path. To scan for vulnerabilities in an image:
grype
The above command scans for vulnerabilities that are visible in the container (i.e., the squashed representation of the image). To include software from all image layers in the vulnerability scan, regardless of its presence in the final image, provide –scope all-layers:
grype --scope all-layers
Grype can scan a variety of sources beyond those found in Docker.
# scan a container image archive (from the result of `docker image save ...`, `podman save ...`, or `skopeo copy` commands) grype path/to/image.tar # scan a directory grype dir:path/to/dir
Resources
You can download Grype or read more here.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….


