If you have a dedicated server or a VPS, chances are you are the only Administrator/root user who needs to maintain it from SSH or command line. That means, you also get a *hitload of email alerts from your server about botnets trying to access your servers SSH port. There’s many ways you can manage this and secure your server. The most common is to change SSH server ports to something unusual. The second way is to limit SSH access by IP or Subnet. Both has it’s benefits. The third way is to switch to certificate based authentication. But if you are the only SSH/FTP user for your server, then limiting access to specific ports by country is another option without remembering the port or multiple ISP subnets you use. For example, I manage my servers from my mobile (so, it’s using my carriers IP), from home (home ISP), from Work (Work Subnet), from Public WiFi spot over VPN etc. Depending on where I am at and which ports are open in their firewall, I found I can simply limit it by Country Code and use certificate based authentication. That drops false alerts to simply zero. 
I use ConfigServer Security & Firewall (or more commonly known as CSF Firewall). Apart from changing SSH ports, switching to certificate based authentication, I am limiting access to specific ports by country in CSF, and IT IS AWESOME.
To limit the ability to connect on a specific port or ports to visitors with IP addresses originating in a specific country or countries, you must:
- Close that port in firewall
- Define country codes allowed to connect on those blocked ports
- Specify blocked ports to be opened for specified country
In this example, we’re restricting access to a non-standard SSH port, 48695, to IP addresses based in Germany(DE).
Step 1 – Close the Ports in the Firewall
Log in to your server via SSH and browse to /etc/csf folder. Create a backup of csf.conf file.
root@blackTOP:~# root@blackTOP:~# cd /etc/csf root@blackTOP:/etc/csf# root@blackTOP:/etc/csf# cp csf.conf csf.conf-bkp root@blackTOP:/etc/csf# root@blackTOP:/etc/csf# vi csf.conf
Open csf.conf file and scroll down to the IPv4 Port Settings section, and remove the desired port number (in this case Port 22) from the TCP_IN and UDP_IN (if present) fields.
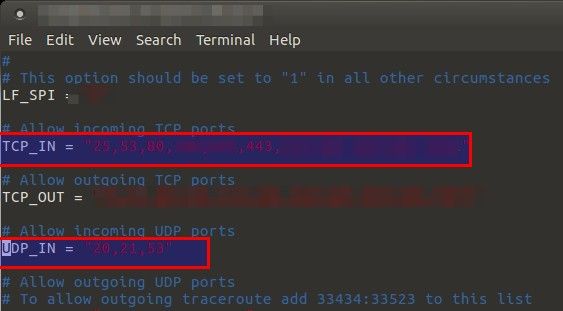
Here, we’ve removed port 48695 from the allowed incoming IPV4 ports, effectively blocking external access to the port:
Step 2 – Add allowed country code
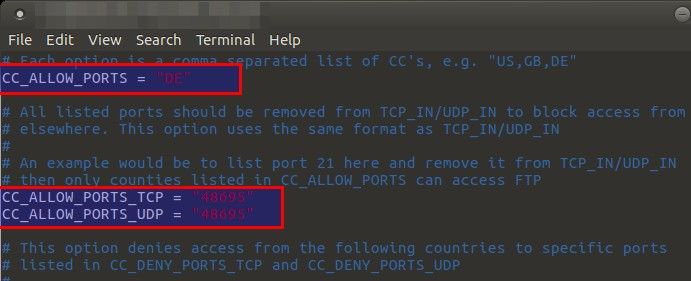
Seach for CC_ALLOW_PORTS i.e. Country Code Lists and Settings section and add the country code to CC_ALLOW_PORTS.
I am allowing traffic originating from DE to connect on ports which have been otherwise closed in the firewall.
Multiple countries can be comma separated with no spaces in between, and you can find a list of ISO 3166-1 alpha-2 codes at https://en.wikipedia.org/wiki/ISO_3166-1_alpha-2
Find CC_ALLOW_PORTS_TCP and CC_ALLOW_PORTS_UDP fields in the config.
Add port 48695 to open to the country (or countries) specified in CC_ALLOW_PORTS here from Step 2. Once all done, save csf.conf.
Step 3 – Restart CSF and LFD
Now we need to restart CSF and LFD.
root@blackTOP:~# service lfd restart root@blackTOP:~# csf -r
This change will allow only users from Germany(DE) to access my custom SSH port in the firewall’s IPV4 Port Settings on port 48695. This works pretty well for me as I am with one of the largest ISP’s who’s IP range is well defined. Also allows me to login via my Mobile as my carrier is also using in-house IP addresses.
If you’re using CSF Firewall, you will find this cheat sheet useful.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….



I also manage my servers from my mobile, from home, from work, from public. However, I establish a VPN connection first (TBH, that’s the first thing that’s done otherwise FWs drop any non-VPC traffic to prevent leak) so that my exit node (external IP) is always the same. Nowadays with cross-platform VPN clients available, I cannot really imagine using any network connected device without a VPN.