In the dark tech world, it is uncommon for virus coders to develop Android banking Trojans and distribute their source code for free to the public. However, according to Dr. Web, a Russian security firm, a dark web hacker forum recently released freely the code of such a malicious app alongside a manual on its usability. The underground black hat community is used to highly-priced commercial transactions over such knock-down products, but this one comes as a bonus to them. The nerve wrecking bit is that unethical hackers are already recompiling the source code and distributing resultant apps under the semblance of innocuous and less suspicious programs. As a matter of fact, a malware going by the name Android.BankBot.149.origin has attracted the attention of the security firm. Dubbed BankBot, this app is the first detected iteration of the malicious code.
Dr. Web discovered that this Trojan is circulating in two main ways: By embedding it in legit APKs, then distributing the infected app using third-party app stores. In a second way, the malicious code is developed as an independent app and hidden behind a genuine app icon and a name such as Google PlayStore; but with banker app capabilities and permissions.
How it works
According to the company, once the user installs it, it prompts them to give it administrative rights and permissions which protect it against deletion from the system. It further hides from the app list and removes all of its shortcuts from the home screen making its presence temporarily forgotten by the user. It runs in the background pending the launch of Russian mobile banking apps and Social media applications which are its primary targets. Meanwhile, it connects to a command and control server awaiting further direction. It is capable of displaying a fake login interface on top of an attacked app by loading a phishing input form able to harvest user’s credentials. It requires the victim to re authenticate hence prompting them to insert their login information. As for the social media apps such as Facebook, Instagram, Twitter, etc. an interface similar to that of an app purchase shows which lures users to enter credit card info. Data collected is then transferred back to the online servers where the attacker can access it.
What is even more disturbing is its capability to manage text messages. If the attack for money siphoning, for example, is successful, the bank withdrawal text notification is intercepted and instead sent to the attacker’s online servers. Here, the text is deleted making the attack a clean and silent one.
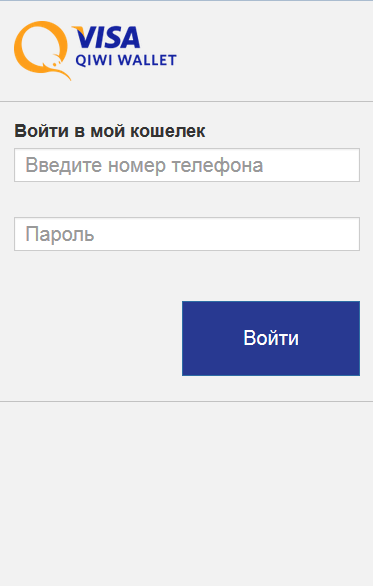
The following are the examples of such fraudulent authentication forms:
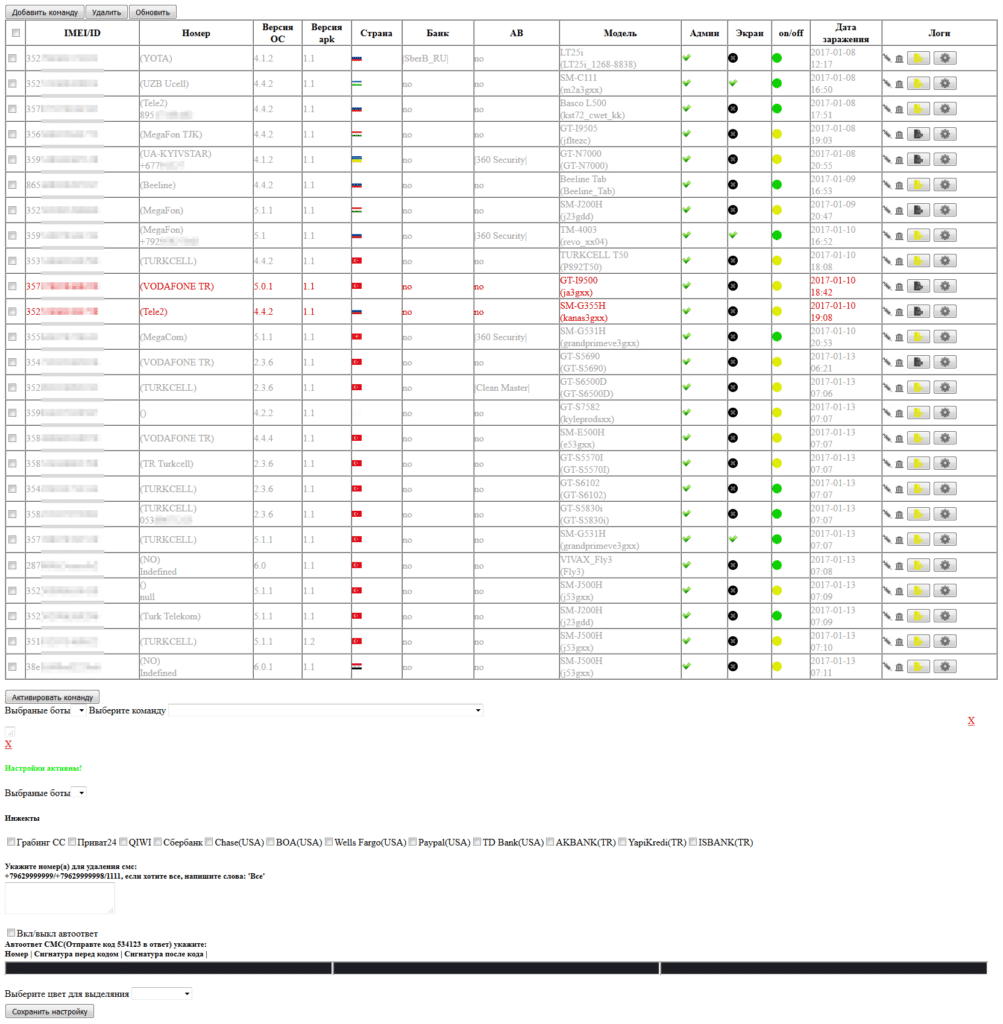
The Trojan can receive the following commands from the command and control server:
- Send SMS – to send SMS;
- Go_P00t_request – to request administrator privileges;
- |UssDg0= – to send a USSD request;
- nymBePsG0 – to request the list of phone numbers from the contact list;
- |telbookgotext= – to send SMS messages with the text from its command to the entire contact list;
- Go_startPermis_request – to request additional permissions SEND_SMS, CALL_PHONE, READ_CONTACTS, ACCESS_FINE_LOCATION on devices with Android 6.0 and higher;
- Go_GPSlocat_request – to get GPS coordinates;
- state1letsgotxt – to receive an executable file containing a list of attacked banking applications;
- |startinj= – to display phishing window WebView with content downloaded from the link specified in a command.
Other actions the Trojan is capable of include the ability to send USSD requests, obtain victim’s contact list, track device via GPS, request additional permissions on latest interactive Android versions and show phishing dialogs.
Information on found matches is sent to the C&C server. The Trojan receives a list of files to be monitored from execution. After one of them is launched, Android.BankBot.149.origin displays WebView on top of the attacked application with a fraudulent authentication form to access the user account. Then the entered information is sent to the server.
How to Avoid These Trojans
Few easy tips you can to follow to avoid these Trojans:
- Download applications from verified and trusted sources only like the Google App market. Google regularly scans all apps uploaded to the Store for malicious activity thus a safer market to obtain apps.
- Exercise prudence while granting an app any requested permission. Only give apps the permissions they need.
- Understand what an app does before installing it. Users are advised against installing any app without a prior understanding of its exact functionality.
- Report any suspicious activity from an app to necessary authorities to be safe.
- Use an anti-virus to block potentially harmful apps.
What to do when infected
Dr. Web advises victims to resist providing any login and credit card information immediately they are aware they are infected. They are further instructed to follow these steps to obliterate the malicious app from their system safely.
- Load the phone in safe mode (This varies across Android versions, contact manufacturer for a detailed guide).
- Once in safe mode, get Dr.Web app from here. The app is powerful enough to conduct a full scan of an infected device and neutralize detected threats.
- Turn the phone off and boot it normally.
The best defense is discreet proactive offense.


