The Pentbox is a safety kit containing various tools for streamlining PenTest conducting a job easily. It is programmed in Ruby and oriented to GNU / Linux, with support for Windows, MacOS and every systems where Ruby is installed. In this small article we will explain how to set up a honeypot in Kali Linux. If you don’t know what is a honeypot, “a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems.”
Download Pentbox:
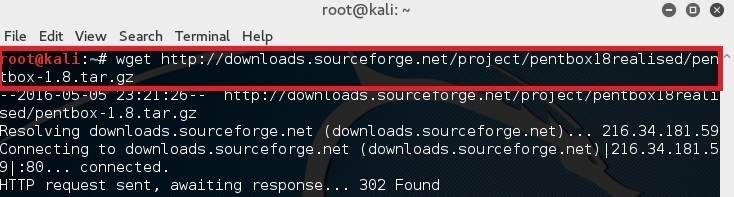
Simply type in the following command in your terminal to download pentbox-1.8.
root@kali:~# wget http://downloads.sourceforge.net/project/pentbox18realised/pentbox-1.8.tar.gz
Uncompress pentbox files
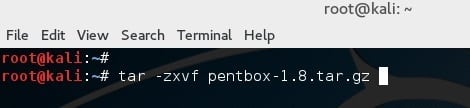
Decompressing the file with the following command:
root@kali:~# tar -zxvf pentbox-1.8.tar.gz
Run pentbox ruby script
Change directory into pentbox folder
root@kali:~# cd pentbox-1.8/
Run pentbox using the following command
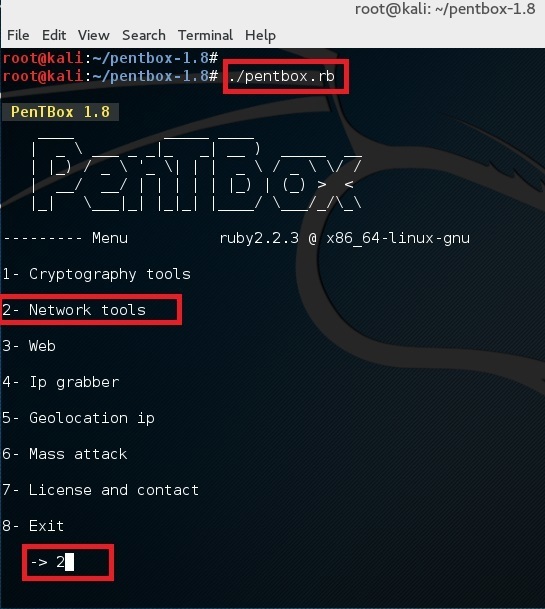
root@kali:~# ./pentbox.rb
Setup a honeypot
Use option 2 (Network Tools) and then option 3 (Honeypot).
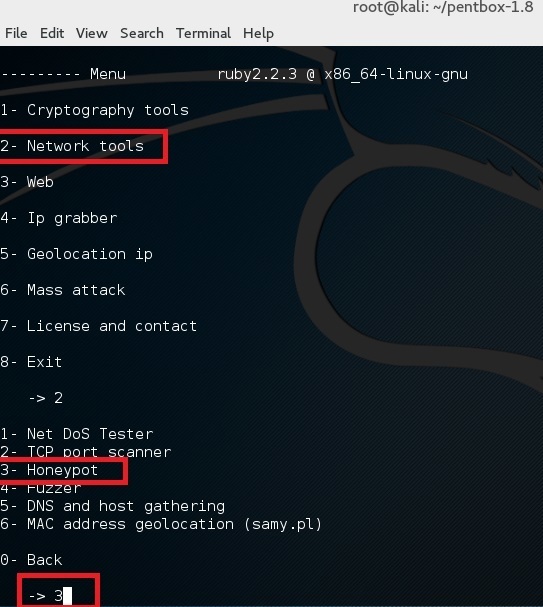
Finally for first test, choose option 1 (Fast Auto Configuration)
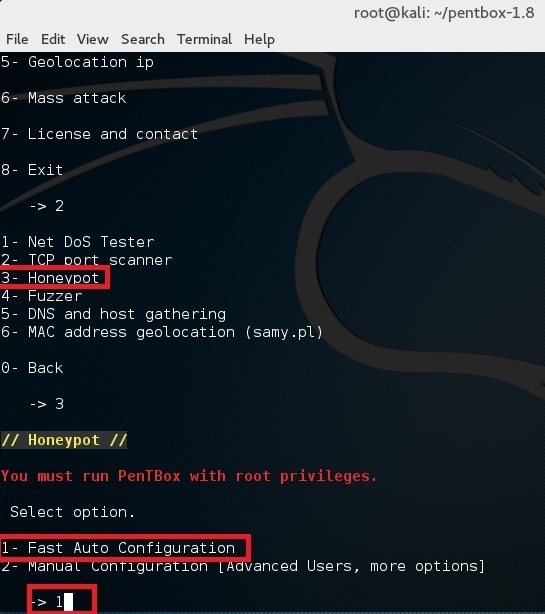
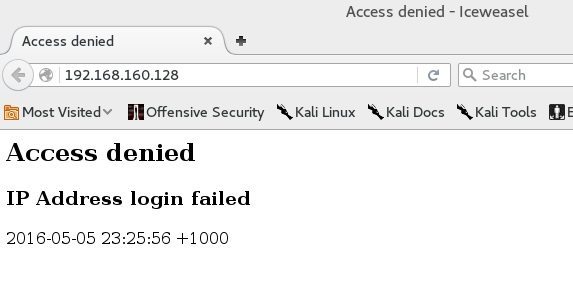
This opens up a honeypot in port 80. Simply open browser and browse to http://192.168.160.128 (where 192.168.160.128 is your IP Address. You should see an Access denied error.
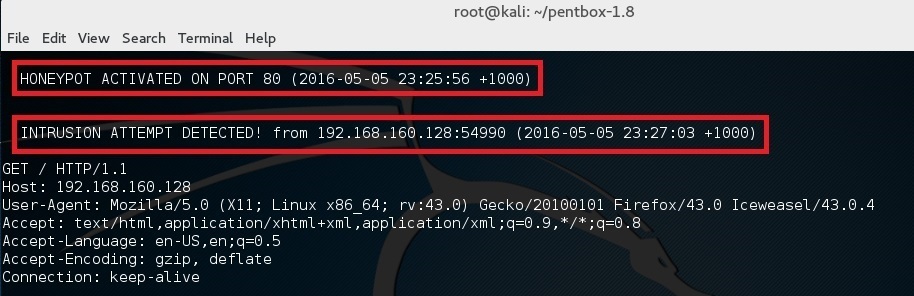
and in the terminal you should see “HONEYPOT ACTIVATED ON PORT 80” followed by “INTRUSION ATTEMPT DETECTED”.
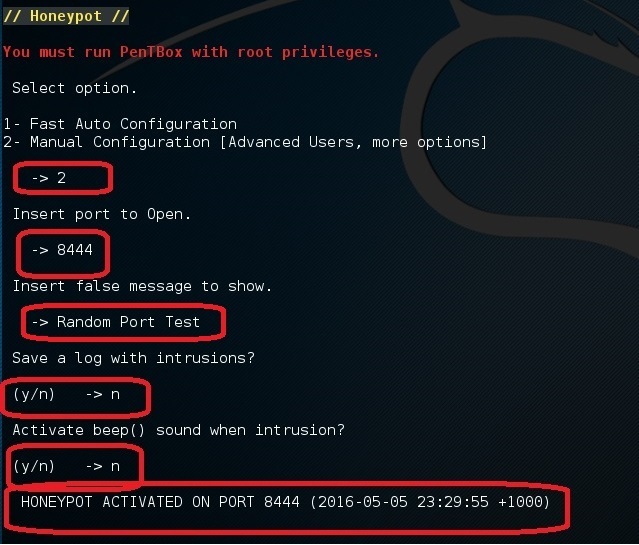
Now, if you do the same steps but this time select Option 2 (Manual Configuration), you should see more extra options
Do the same steps but select port 22 this time (SSH Port). Then do a port forwarding in your home router to forward port external port 22 to this machines’ port 22. Alternatively, set it up in a VPS in your cloud server.
You’d be amazed how many bots out there scanning port SSH continuously. You know what you do then? You try to hack them back for the lulz!
Here’s a video of setting up honeypot if video is your thing:
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….
 .
.



Hmmm This is new for me to learn
Pentbox-1.8 seems to be made by a source completely independent of the genuine Pentbox 1.5… Adding to that, none of the functions listed after number 3 (Web) work… 4 shows terms, 5 exits, 6+ do nothing… This seems pretty suspicious to me considering that only the original functions from 1.5 work and everything else is bogus. I wouldn’t recommend anyone downloads this file.
I’m surprised by your definition of a honeypot. Typically a honeypot is a type of system designed to induce attacks, not deflect or counteract them.
What is the use of honeypot..
Plzz reply
Honey pot is a deliberate security loop hole. Careless attacker might hit honey pot before they hit the more important part of the system. Depend on the kindof honeypot, it can give u information about the attackers.
I want to ask what is the type of this honeypot?