Grabber is a web application scanner. Basically it detects some kind of vulnerabilities in your website. Grabber is simple, not fast but portable and really adaptable. This software is designed to scan small websites such as personals, forums etc. absolutely not big application: it would take too long time and flood your network.
Why this kind of application ?
This is a very small application (currently 2.5kLOC in Python) and the first reason of this scanner is to have a “minimum bar” scanner for the Samate Tool Evaluation Program at NIST.
Grabber is also for me a nice way to do some automatics verification on websites/scripts I do. Users should know some things about web vulnerabilities before using this soft because it only tell you what vulnerability it is… not how to solve it.
Current features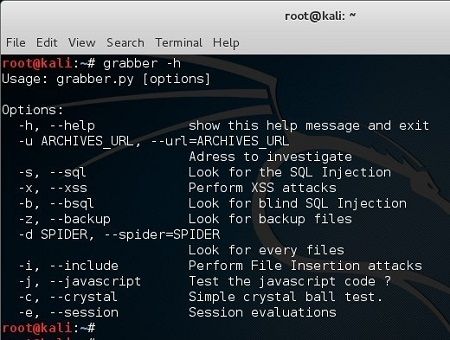
Because it’s a small tool, the set of vulnerabilities is small…
- Cross-Site Scripting
- SQL Injection (there is also a special Blind SQL Injection module)
- File Inclusion
- Backup files check
- Simple AJAX check (parse every JavaScript and get the URL and try to get the parameters)
- Hybrid analysis/Crystal ball testing for PHP application using PHP-SAT
- JavaScript source code analyzer: Evaluation of the quality/correctness of the JavaScript with JavaScript Lint
- Generation of a file [session_id, time(t)] for next stats analysis.
Does it scan the JavaScript ?
Yes! It can handle the JavaScript files, parse it to retrieve the server sides scripts names and try to get some parameters name…
What’s nice with Grabber ?
Because every patterns are in a “quite standard” XML file, you can add, or test what ever you want. You can also focus of a kind of vulnerability then do a massive test. You can also do all the test on a single page…
What are you using ?
This application is based on:
- Researchs from famous websites/guys:
- ha.ckers.org (the XSS vector at least)
- SPI-Dynamics lab/portal
- Whitehatsec
- cgisecurity.com
- OWASP etc.
- and a huge amount of information given by lots of tools (Pantera, Paros, Wapiti, WebInspect, Hailstorm, AppScan etc.)
- Python:
Grabber aim to be simple. It’s a small tool, does not provide any GUI or PDF report! There is XML reports (you can easily create a XSLT to render the XML for you manager).
What needs to be done on Grabber ?
There are couple of things I want to fix/do:
- Cookies/Http Auth/Login Page authentification systems
- Multi site support (which is not too hard to do due to the XML structure)
- Fix the parsers
- Make a real/better detection system
- Plug a JavaScript engine for real XSS detection
- Make a real output
- Provide solution for the given vulnerabilities? (not quite sure about this)
- Definitely, playing with the differents encodings types.
How do I use Grabber ?
Grabber comes per-installed with Kali Linux.
Grabber Help Menu - Press to expand
root@kali:~# grabber -h
Usage: grabber [options]
Options:
-h, --help show this help message and exit
-u ARCHIVES_URL, --url=ARCHIVES_URL
Adress to investigate
-s, --sql Look for the SQL Injection
-x, --xss Perform XSS attacks
-b, --bsql Look for blind SQL Injection
-z, --backup Look for backup files
-d SPIDER, --spider=SPIDER
Look for every files
-i, --include Perform File Insertion attacks
-j, --javascript Test the javascript code ?
-c, --crystal Simple crystal ball test.
-e, --session Session evaluations
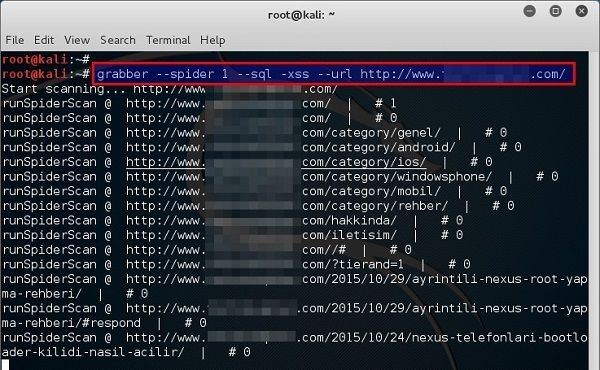
Grabber usage
Spider the web application to a depth of 1 (–spider 1) and attempt SQL (–sql) and XSS (–xss) attacks at the given URL (–url http://kali-test-random-gen.com):
Grabber Output - Click to expand
root@kali:~# grabber --spider 1 --sql -xss --url http://kali-test-random-gen.com/ Start scanning... http://kali-test-random-gen.com/ runSpiderScan @ http://kali-test-random-gen.com/ | # 1 runSpiderScan @ http://kali-test-random-gen.com/ | # 0 runSpiderScan @ http://kali-test-random-gen.com/category/genel/ | # 0 runSpiderScan @ http://kali-test-random-gen.com/category/android/ | # 0 runSpiderScan @ http://kali-test-random-gen.com/category/ios/ | # 0 Start investigation... Method = GET http://kali-test-random-gen.com [Cookie] 0 : [Cookie] 1 : Method = GET http://kali-test-random-gen.com [Cookie] 0 : [Cookie] 1 :
Source: Grabber Homepage
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….



oley be türk be
i get an error Error during the construction of the log system what do i do?
alert(‘xss detected’)
lmao, skript kiddie.
nobody actually goes around laughing at people for being script kiddies unless they themselves were just recently script kiddies.