Uniscan is a simple Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. It’s a very simple yet quite powerful tool to scan website for vulnerabilities in Kali Linux (or any Linux as a matter of fact). It does the job fast and without hassle. You don’t need too much experience to run it, but you might need a good Internet connection and a very long time.
Uniscan got a text or CLI based scanner and a Graphical interface. You can use either but I found CLI to be somewhat faster. But I could be wrong.
[toggle title=”Uniscan Help Menu – Click to expand” state=”close”]
root@kali:~# uniscan -h
####################################
# Uniscan project #
# http://uniscan.sourceforge.net/ #
####################################
V. 6.3
OPTIONS:
-h help
-u <url> example: https://www.example.com/
-f <file> list of url's
-b Uniscan go to background
-q Enable Directory checks
-w Enable File checks
-e Enable robots.txt and sitemap.xml check
-d Enable Dynamic checks
-s Enable Static checks
-r Enable Stress checks
-i <dork> Bing search
-o <dork> Google search
-g Web fingerprint
-j Server fingerprint
usage:
[1] perl ./uniscan.pl -u http://www.example.com/ -qweds
[2] perl ./uniscan.pl -f sites.txt -bqweds
[3] perl ./uniscan.pl -i uniscan
[4] perl ./uniscan.pl -i "ip:xxx.xxx.xxx.xxx"
[5] perl ./uniscan.pl -o "inurl:test"
[6] perl ./uniscan.pl -u https://www.example.com/ -r
root@kali:~#
[/toggle]
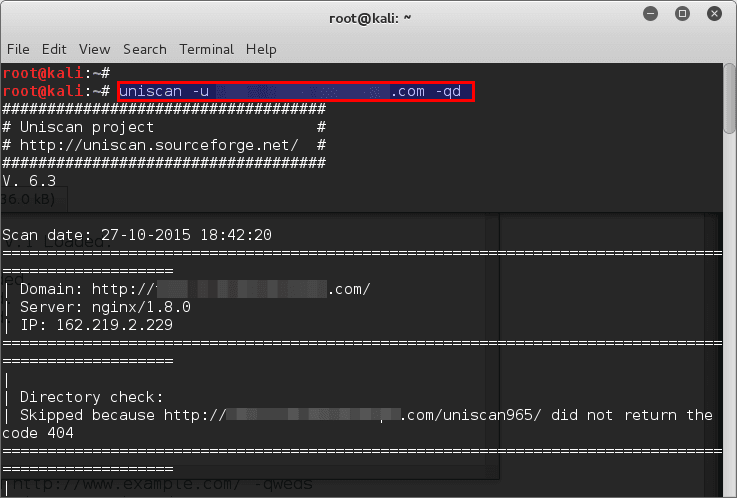
Scanning websites using Uniscan
Scan the given URL (-u http://192.168.1.202/) for vulnerabilities, enabling directory and dynamic checks (-qd):
root@kali:~# uniscan -u http://somesite.com/ -qd #################################### # Uniscan project # # http://uniscan.sourceforge.net/ # ####################################
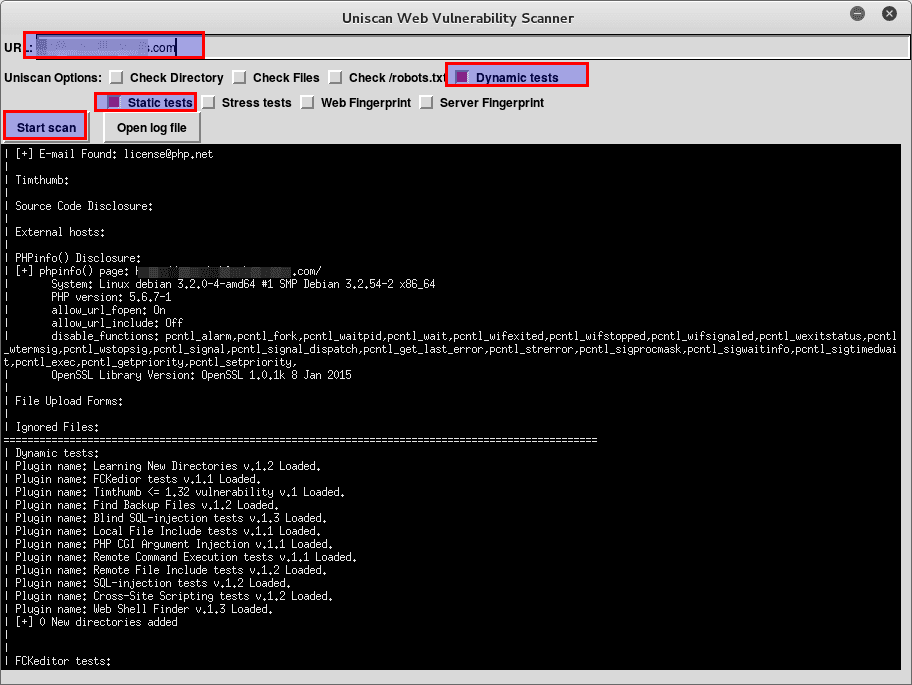
Scanning website using Uniscan-GUI
First run uniscan-gui using the following command from your terminal:
In the GUI you type in the URL of the target site and select the checks you want to perform. Press Start Scan and off you go.
If you want to check everything, it’s better off using uniscan from command line with a -b flag to have uniscan running in background. For example:
root@kali:~# uniscan -u test-a.blackmoreops.com -bqdw
There’s many other tools and I will discuss them in time. In the meantime you can use few tools like hping3, slowloris, GoldenEye etc. to do stress testing