Sometimes you need to send a file containing sensitive information across to someone over internet and you started thinking, “Gee, I’ve got some pretty sensitive information in the file. How can I send it securely?” There are many ways to send encrypted files. A good way for encrypting files is using a long password with GPG or GNU Privacy Guard (GnuPG or GPG) tool. Once you’ve encrypted the file, you can do few things.
- Put the file in an FTP or Web server the requires a second set of username and passwords.
- To further secure, you can put a firewall rule to allow a single IP/Network to access that location.
- Send the file via email as an attachment.
- Send the file via encrypted email. (double encryption). We will look into email encryption soon.
- Create a torrent file and send it securely as a private torrent if the file is too big. (i.e. movies, large files etc.)
So the possibilities are endless. GnuPG or GPG works in Windows, Linux, Mac (any iOS devices), Android, Blackberry etc. In short GnuPG or GPG is supported on all platforms and that’s what makes it such a good encryption tool.
GNU Privacy Guard (GnuPG or GPG)
GnuPG is a hybrid encryption software program in that it uses a combination of conventional symmetric-key cryptography for speed, and public-key cryptography for ease of secure key exchange, typically by using the recipient’s public key to encrypt a session key which is only used once. This mode of operation is part of the OpenPGP standard and has been part of PGP from its first version.
GnuPG encrypts messages using asymmetric keypairs individually generated by GnuPG users. The resulting public keys may be exchanged with other users in a variety of ways, such as Internet key servers. They must always be exchanged carefully to prevent identity spoofing by corrupting public key “owner” identity correspondences. It is also possible to add a cryptographic digital signature to a message, so the message integrity and sender can be verified, if a particular correspondence relied upon has not been corrupted.
Downloan GnuPG
You can download GnuPG for the following Operating systems from this Download GnuPG link.
- Windows
- OS X
- Debian
- RPM
- Android
- VMS (OpenVMS)
- RISC OS
- *BSD
- *NIX
- AIX
- HPUX
- IRIX
- Solaris, SunOS
List of supported Operating systems can be found in GnuPG Supported Operating Systems list.
Apart from these, most operating systems have their own implementation of GnuPG which are supported by each other as the underlying encryption and decryption works in a similar way.
Encrypting files in Linux
To encrypt a single file, use command gpg as follows:
root@kali:~# gpg -c secretfilename
To encrypt secretfilename.txt file, type the command:
root@kali:~# gpg -c secretfilename.txt
Sample output:
Enter passphrase: Repeat passphrase:
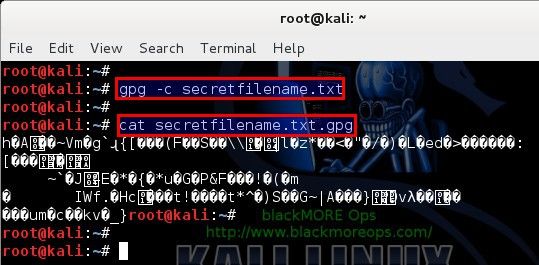
This will create a secretfilename.txt.gpg file. GnuPG or GPG help doco below:
[toggle title=”GnuPG or GPG help menu” state=”close”]
root@kali:~# gpg --help
gpg (GnuPG) 1.4.12
Copyright (C) 2012 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Home: ~/.gnupg
Supported algorithms:
Pubkey: RSA, RSA-E, RSA-S, ELG-E, DSA
Cipher: 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128,
CAMELLIA192, CAMELLIA256
Hash: MD5, SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
Compression: Uncompressed, ZIP, ZLIB, BZIP2
Syntax: gpg [options] [files]
sign, check, encrypt or decrypt
default operation depends on the input data
Commands:
-s, --sign [file] make a signature
--clearsign [file] make a clear text signature
-b, --detach-sign make a detached signature
-e, --encrypt encrypt data
-c, --symmetric encryption only with symmetric cipher
-d, --decrypt decrypt data (default)
--verify verify a signature
--list-keys list keys
--list-sigs list keys and signatures
--check-sigs list and check key signatures
--fingerprint list keys and fingerprints
-K, --list-secret-keys list secret keys
--gen-key generate a new key pair
--delete-keys remove keys from the public keyring
--delete-secret-keys remove keys from the secret keyring
--sign-key sign a key
--lsign-key sign a key locally
--edit-key sign or edit a key
--gen-revoke generate a revocation certificate
--export export keys
--send-keys export keys to a key server
--recv-keys import keys from a key server
--search-keys search for keys on a key server
--refresh-keys update all keys from a keyserver
--import import/merge keys
--card-status print the card status
--card-edit change data on a card
--change-pin change a card's PIN
--update-trustdb update the trust database
--print-md algo [files] print message digests
Options:
-a, --armor create ascii armored output
-r, --recipient NAME encrypt for NAME
-u, --local-user use this user-id to sign or decrypt
-z N set compress level N (0 disables)
--textmode use canonical text mode
-o, --output use as output file
-v, --verbose verbose
-n, --dry-run do not make any changes
-i, --interactive prompt before overwriting
--openpgp use strict OpenPGP behavior
--pgp2 generate PGP 2.x compatible messages
(See the man page for a complete listing of all commands and options)
Examples:
-se -r Bob [file] sign and encrypt for user Bob
--clearsign [file] make a clear text signature
--detach-sign [file] make a detached signature
--list-keys [names] show keys
--fingerprint [names] show fingerprints
Please report bugs to <gnupg-bugs@gnu.org>.
[/toggle]
If you ever forgot your password (passphrase), you cannot recover the data as it use very strong encryption.
Decrypt a file
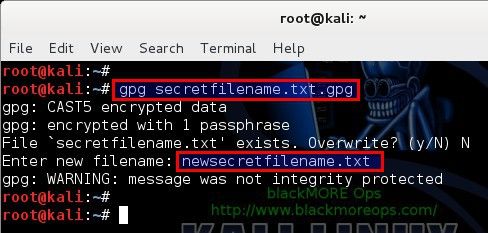
To decrypt file use the gpg command as follow:
root@kali:~# gpg secretfilename.txt.gpg
Sample outputs:
gpg secretfilename.txt.gpg gpg: CAST5 encrypted data Enter passphrase:
Decrypt file and write output to file secretfilename.txt you can run command:
root@kali:~# gpg secretfilename.txt.gpg –o secretfilename.txt
Famous usage of GnuPG
In May 2014, The Washington Post reported on a 12-minute video guide “GPG for Journalists” posted to Vimeo in January 2013 by a user named anon108. The Post identified anon108 as fugitive NSA leaker Edward Snowden, who it said made the tutorial—”narrated by a digitally disguised voice whose speech patterns sound similar to those of Snowden”—to teach journalist Glenn Greenwald email encryption. Greenwald said that he could not confirm the authorship of the video.
Conclusion
As you can see, GnuPG does have real life usage and in many cases it was used in both legal and illegal activities. I won’t go in to discuss about the legality of the usage, but if you are ever in the need of sending and transferring a file that requires encryption, then GnuPG or GPG is definitely a worthy tool to consider for encrypting files in Linux, Unix, Windows or any known platforms.
Hope you’ve enjoyed this little guide. Please share and RT.
Thank You Very Much