So you read newspapers? You know there was this massive DDoS (NTP amplification attack) attack last year? So, what about right now at this instance? Do you want to see Live DDoS attack maps that shows live DDoS attacks around the world? 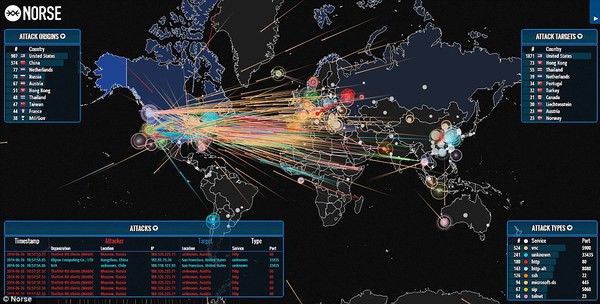
Watch in Awe the multi Gigabit DDoS attacks happening worldwide right now!!! .. Truly amazing and scary. Very interesting interactions between USA and China.
In time I will add more monitoring (there are quite a few more but they are not Live). Before we go in and see the maps lets go over the basics first.
Note: These maps are severely CPU and memory(RAM) intensive. If you’re behind a proxy server, NORSE maps wont work. You will possibly need Flash and Java on your Linux machines to view these maps live. I’ve edited the maps to allow you to view on any screen size. (i.e. mobile or large LCD)
What is DDoS?
In computing, a denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users.
Although the means to carry out, the motives for, and targets of a DoS attack vary, it generally consists of efforts to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet.
As clarification, DDoS (Distributed Denial of Service) attacks are sent by two or more persons, or bots (see botnet). DoS (Denial of Service) attacks are sent by one person or system. As of 2014, the frequency of recognized DDoS attacks had reached an average rate of 28 per hour.
Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers.
DoS threats are also common in business, and are sometimes responsible for website attacks.
This technique has now seen extensive use in certain games, used by server owners, or disgruntled competitors on games, such as server owners’ popular Minecraft servers. Increasingly, DoS attacks have also been used as a form of resistance. Richard Stallman has stated that DoS is a form of ‘Internet Street Protests’. The term is generally used relating to computer networks, but is not limited to this field; for example, it is also used in reference to CPU resource management.
One common method of attack involves saturating the target machine with external communications requests, so much so that it cannot respond to legitimate traffic, or responds so slowly as to be rendered essentially unavailable. Such attacks usually lead to a server overload. In general terms, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
Denial-of-service attacks are considered violations of the Internet Architecture Board’s Internet proper use policy, and also violate the acceptable use policies of virtually all Internet service providers. They also commonly constitute violations of the laws of individual nations.
Some interesting facts
- According to TrendMicro Research $150 can buy a week-long DDoS attack on the black market.
- According to ATLAS Threat Report more than 2000 daily DDoS Attacks are observed world-wide by Arbor Networks.
- According to Verisign/Merril Research worldwide 1/3 of all downtime incidents for different online services are attributed to DDoS attacks.
- Attackers build networks of infected computers, known as ‘botnets’, by spreading malicious software through emails, websites and social media. Once infected, these machines can be controlled remotely, without their owners’ knowledge, and used like an army to launch an attack against any target. Some botnets are millions of machines strong.
- Botnets can generate huge floods of traffic to overwhelm a target. These floods can be generated in multiple ways, such as sending more connection requests than a server can handle, or having computers send the victim huge amounts of random data to use up the target’s bandwidth. Some attacks are so big they can max out a country’s international cable capacity.
- Specialized online marketplaces exist to buy and sell botnets or individual DDoS attacks. Using these underground markets, anyone can pay a nominal fee to silence websites they disagree with or disrupt an organization’s online operations. A week-long DDoS attack, capable of taking a small organization offline can cost as little as $150.
Types of Attacks
DDoS attacks come in many different forms, from Smurfs to Teardrops, to Pings of Death. Below are details about the types of attacks and amplification methods found on the map:
Attack Class: Four common categories of attacks
TCP Connection Attacks – Occupying connections
These attempt to use up all the available connections to infrastructure devices such as load-balancers, firewalls and application servers. Even devices capable of maintaining state on millions of connections can be taken down by these attacks. Learn more…
Volumetric Attacks – Using up bandwidth
These attempt to consume the bandwidth either within the target network/service, or between the target network/service and the rest of the Internet. These attacks are simply about causing congestion. Learn more…
Fragmentation Attacks – Pieces of packets
These send a flood of TCP or UDP fragments to a victim, overwhelming the victim’s ability to re-assemble the streams and severely reducing performance. Learn more…
Application Attacks – Targeting applications
These attempt to overwhelm a specific aspect of an application or service and can be effective even with very few attacking machines generating a low traffic rate (making them difficult to detect and mitigate). Learn more…
Amplification: Two ways attacks can multiply traffic they can send
DNS Reflection – Small request, big reply
By forging a victim’s IP address, an attacker can send small requests to a DNS server and ask it to send the victim a large reply. This allows the attacker to have every request from its botnet amplified as much as 70x in size, making it much easier to overwhelm the target. Learn more…
Chargen Reflection – Steady streams of text
Most computers and internet connected printers support an outdated testing service called Chargen, which allows someone to ask a device to reply with a stream of random characters. Chargen can be used as a means for amplifying attacks similar to DNS attacks above Learn more…
Here’s a list of all possible UDP Based attacks I’ve compiled in my previous post
List of more UDP based Amplification Attacks
- DNS
- NTP
- Understanding and mitigating NTP-based DDoS attacks
- Technical Details Behind a 400Gbps NTP Amplification DDoS Attack
- NTP Amplification Attack Tool posted by anonymous user in github
- SNMPv2
- SNMP Reflected Amplification DDoS Attack
- SNMP Reflected Denial of Service
- NetBIOS
- NETBIOS based pentesting tutorial by Gaurav Kumar
- Denial of Service Attack in NetBIOS Services
- NetBIOS Attack Methods
- SSDP
- Protect Yourself Against Denial-of-Service Attacks – SSDP
- UPnP Networking Flaws Expose Tens Of Millions Of IPs To Hack Attacks
- CharGEN
- Chargen denial of service (Chargen Denial of Service)
- A Chargen-based DDoS? Chargen is still a thing?
- ECHO Chargen Loop DoS
- QOTD
- BitTorrent
- Kad
- Quake Network Protocol
- Steam Protocol
The list of known protocols, and their associated bandwidth amplification factors, is listed below. US-CERT would like to offer thanks to Christian Rossow for providing this information to us.
| Protocol | Bandwidth Amplification Factor | Vulnerable Command |
| DNS | 28 to 54 | see: TA13-088A [1] |
| NTP | 556.9 | see: TA14-013A [2] |
| SNMPv2 | 6.3 | GetBulk request |
| NetBIOS | 3.8 | Name resolution |
| SSDP | 30.8 | SEARCH request |
| CharGEN | 358.8 | Character generation request |
| QOTD | 140.3 | Quote request |
| BitTorrent | 3.8 | File search |
| Kad | 16.3 | Peer list exchange |
| Quake Network Protocol | 63.9 | Server info exchange |
| Steam Protocol | 5.5 | Server info exchange |
Digital Attack Map (by Google Research, Big Picture team and Arbor)
Top daily DDoS attacks worldwide
Digital DDoS attack maps is a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks. The tool surfaces anonymous attack traffic data to let users explore historic trends and find reports of outages happening on a given day.
Link to Original map: http://www.digitalattackmap.com/
NORSE DDoS attack maps by Norse Corp
Norse Dark Intelligence
Every second, Norse collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries. The attacks shown are based on a small subset of live flows against the Norse honeypot infrastructure, representing actual worldwide cyber attacks by bad actors. At a glance, one can see which countries are aggressors or targets at the moment, using which type of attacks (services-ports).
Hovering over the Attack Origins, Attack Targets, or Attack Types will highlight just the attacks emanating from that country or over that service-port respectively. Hovering over any bubble on the map, will highlight only the attacks from that location and type. Press s to toggle table sizes. You can also minimize the bubbles.
Norse exposes its threat intelligence via high-performance, machine-readable APIs in a variety of forms. Norse also provides products and solutions that assist organizations in protecting and mitigating cyber attacks.
Link to Original map: http://map.norsecorp.com/#/
Conclusion
To protect your website, you need to be able to block or absorb malicious traffic. Webmasters can talk to their hosting provider about DDoS attack protection. They can also route incoming traffic through a reputable third-party service that provides distributed caching to help filter out malicious traffic — reducing the strain on existing web servers. Most such services require a paid subscription, but often cost less than scaling up your own server capacity to deal with a DDoS attack.
Google Ideas has launched a new initiative, Project Shield, to use Google’s infrastructure to support free expression online by helping independent sites mitigate DDoS attack traffic.
Through the continued collaboration of the many stakeholders involved in improving the Internet, a number of efforts can help to reduce the threat of DDoS attacks.
For example, ten years ago the Network Working Group of the Internet Engineering Task Force published BCP 38 (also known as RFC 2827) as a best practice guideline for how ISPs and hosting providers can filter fake IP addresses to reduce the impact of DDoS activity on themselves and others. Unfortunately, many ISPs have still yet to implement these best practices, preventing its benefits from being fully realized by the wider internet community.
Distributed Denial of Service (DDoS) attacks can be used to make important online information unavailable to the world. Sites covering elections are brought down to influence their outcome, media sites are attacked to censor stories, and businesses are taken offline by competitors looking for a leg up. Protecting access to information is important for the Internet and important for free expression.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….


Awesome map. What is interesting is that many of the attacks are originating from Google’s IP addresses — I guess its fiber service is being misused royally.
Hmm…
Hi Jonathan,
Correct. There’s one more factor that I came up with. You would see most targets are in USA and one would think it is the US Govt sites that are being attacked. But in reality, most big web hosting companies (i.e. Amazon, GoDaddy, Hostgator etc.) and sites like Google, Ebay etc. are mainly based on USA. So I think we are seeting some legit traffic in this map as well (i.e. Port: ha-cluster which is usually Checkpoint Firewall sync traffic as far as I know, correct me if I am wrong here) showed in this map. Occationally you see random bursts which is internal misconiguration where BGP/Private domain traffic leaks out. You would also see script kiddies attacking a website (i.e. for example my server is in USA) and depending on how big that is, you see it in this map. Same goes when Google syncs it’s traffic/data to USA, not too sure how to separate those traffic but it would definitely look like a DDOS attack on USA. Someone who misconfigured their Amazon EC account (files hosted on it — see it here: http://www.behind-the-enemy-lines.com/2012/04/google-attack-how-i-self-attacked.html ) and Google’s content servers from all around the world started syncing to it, ended up with a hefty bill for 8.8 Terabytes traffic. There was this other time some Pakistani ISP misconfigured their BGP to get better youtube view reduce hops). See it here — http://www.cnet.com/au/news/how-pakistan-knocked-youtube-offline-and-how-to-make-sure-it-never-happens-again/
But you get the idea that a simple misconfiguration can lead someone to appear on these maps.
I am not saying that this map is incorrect and obviously those who made it know a LOT better than I do, but when everyone instigates that USA cops the worst DOS/DDOS, it merely means the end point is in USA. Thoughts ? go through the websites and you can possibly track down the big DDOS fight between Spamhaus and Cyber Bunker. Then again, USA seems like the prime target just for the fact many big financial org’s have their HQ in there.
But yes, those who are in Security business would defnitely be using something similar (if not the exact map) like these ones.
Thanks for your comment and visiting my website. Cheers,
-BMO
Hey guys…how can I add such a map on my site http://divtech.pp.ua?