In keeping with the Kali Linux Network Services Policy, there are no network services, including database services, running on boot so there are a couple of steps that need to be taken in order to get Metasploit up and running with database support.
This post solves the following issues when starting Metasploit:
- [-] Error while running command db_connect: Failed to connect to the database: PG::Error: ERROR: permission denied to create database : CREATE DATABASE “metasploit3” ENCODING = ‘utf8’
- [-] Error while running command db_connect: Failed to connect to the database: FATAL: role “root” does not exist
- msf > db_status[*] postgresql selected, no connection
Start the Kali PostgreSQL Service
Metasploit uses PostgreSQL as its database so it needs to be launched first.
service postgresql start
You can verify that PostgreSQL is running by checking the output of ss -ant and making sure that port 5432 is listening.
State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 :::22 :::* LISTEN 0 128 *:22 *:* LISTEN 0 128 127.0.0.1:5432 *:* LISTEN 0 128 ::1:5432 :::*
Start the Kali Metasploit Service
With PostgreSQL up and running, we next need to launch the metasploit service. The first time the service is launched, it will create a msf3 database user and a database called msf3. The service will also launch the Metasploit RPC and Web servers it requires.
service metasploit start
Launch msfconsole in Kali
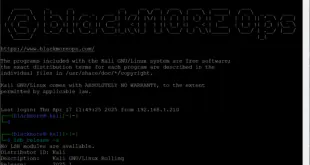
Now that the PostgreSQL an Metasploit services are running, you can launch msfconsole and verify database connectivity with the db_status command as shown below.
msfconsole msf > db_status [*] postgresql connected to msf3 msf >
Configure Metasploit to Launch on Startup
If you would prefer to have PostgreSQL and Metasploit launch at startup, you can use update-rc.d to enable the services as follows.
update-rc.d postgresql enable update-rc.d metasploit enable
I don’t claim ownership with this post, this is also available in Kali Linux Official Documentation. I again suggest readers to do some study and read Kali Official Documentation.
Source: Starting Metasploit Framework
If you’re interested on how to use metasploit to pentest Windows 2003 Server, following guide will take you through step by step procedures.
Hack Remote PC (Windows 2003 server) with Metasploits
Thanks for reading. Please share.
 blackMORE Ops Learn one trick a day ….
blackMORE Ops Learn one trick a day ….


[….] Starting Metasploit web server: thin/opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/lib/thin/daemonizing.rb:173:in `remove_stale_pid_file’: log/thin.pid already exists, seems like it’s already running (process ID: 0). Stop the process or delete log/thin.pid. (Thin::PidFileExist)
from /opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/lib/thin/daemonizing.rb:43:in `daemonize’
from /opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/lib/thin/controllers/controller.rb:61:in `start’
from /opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/lib/thin/runner.rb:187:in `run_command’
from /opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/lib/thin/runner.rb:152:in `run!’
from /opt/metasploit/apps/pro/ui/vendor/bundle/ruby/1.9.1/gems/thin-1.5.1/bin/thin:6:in `’
from /opt/metasploit/apps/pro/ui/scripts/ctl.rb:33:in `load’
from /opt/metasploit/apps/pro/ui/scripts/ctl.rb:33:in `start_thin’
from /opt/metasploit/apps/pro/ui/scripts/ctl.rb:47:in `’
when i do “service metasploit start”
That’s the problem ..
Why not stop MetaSploit first if it’s already running…
and then start it ..
…
Did you by any chance demonized it? i.e. run it at boot? that can cause it..
No me funciona, inicio todos los servicios pero cuando ejecuto db_status me dice [*] postgresql selected, no connection” [!] Database not connected or cache not built, using slow search
1.When you will make tutorials for msfconsole ?
2.How to choose exploit ?
3.How to choose payload ?
4.Please skip windows xp
5.Thank you.
Hi,please create tutorial how to use msfconsole step by step using windows 7 ,please forget xp. If you still there.
I don’t do Windows tuts. I ‘DO’ Windows!
BTW, nice blog you have there, some very useful and handy tips.
thank you
root@kali:~# service metasploit start
Job for metasploit.service failed. See ‘systemctl status metasploit.service’ and ‘journalctl -xn’ for details.
Is it odd that I’m able to start msfconsole without first starting the Postgresql service? I didn’t think I’d be able to do so, but sure enough – it works.
Someone asked me why it’s not a great idea to use only preexisting exploits created by others. I don’t have a good answer for that question. Can anyone chip in a thought or two?